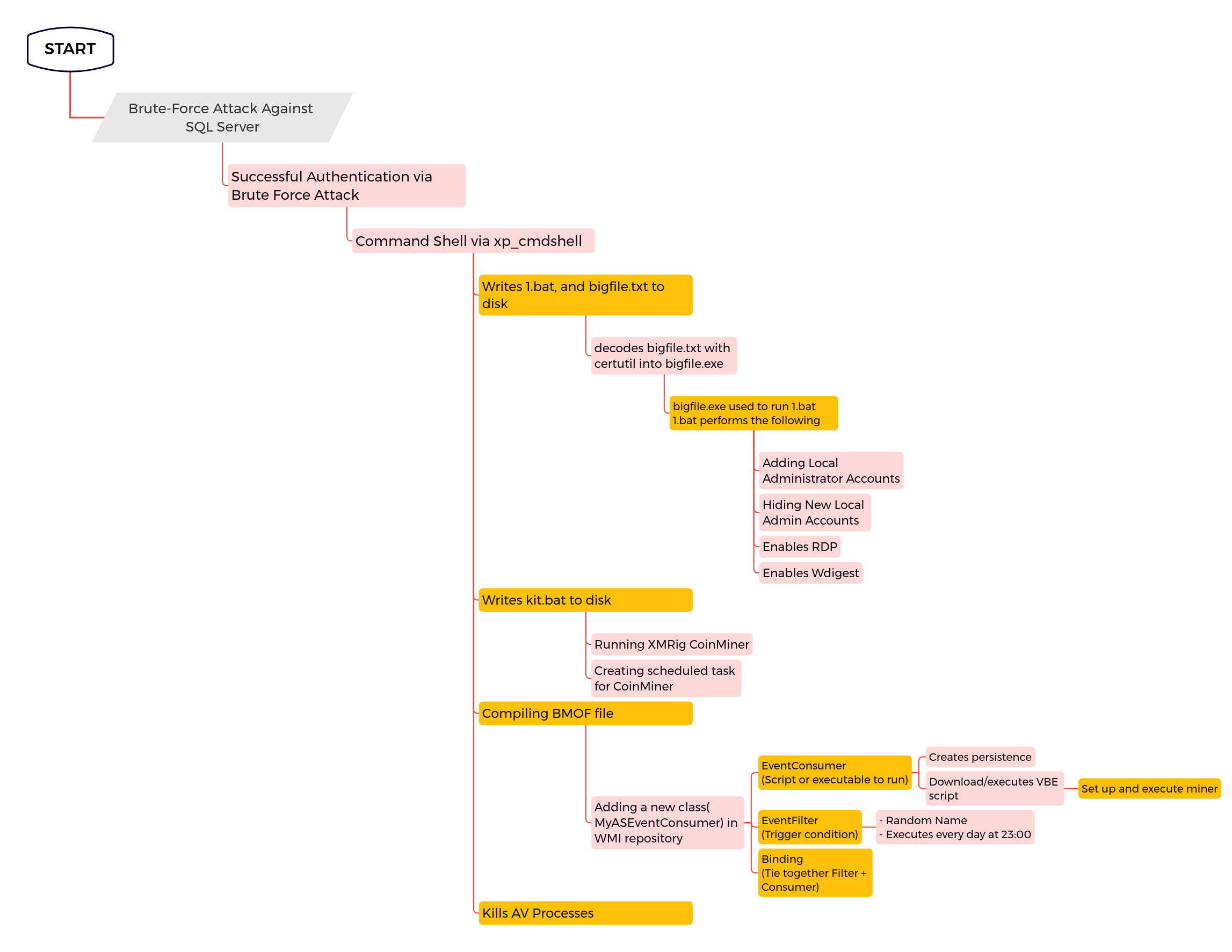
MSSQL XPCmdshell Suspicious Execution
Detects when the MSSQL "xp_cmdshell" stored procedure is used to execute commands
Sigma rule (View on GitHub)
1title: MSSQL XPCmdshell Suspicious Execution
2id: 7f103213-a04e-4d59-8261-213dddf22314
3status: test
4description: Detects when the MSSQL "xp_cmdshell" stored procedure is used to execute commands
5references:
6 - https://www.netspi.com/blog/technical/network-penetration-testing/sql-server-persistence-part-1-startup-stored-procedures/
7 - https://thedfirreport.com/2022/07/11/select-xmrig-from-sqlserver/
8author: Nasreddine Bencherchali (Nextron Systems)
9date: 2022/07/12
10tags:
11 - attack.execution
12logsource:
13 product: windows
14 service: application
15 definition: MSSQL audit policy to monitor for 'xp_cmdshell' must be enabled in order to receive this event in the application log (Follow this tutorial https://dba.stackexchange.com/questions/103183/is-there-any-way-to-monitor-execution-of-xp-cmdshell-in-sql-server-2012)
16 # warning: The 'data' field used in the detection section is the container for the event data as a whole. You may have to adapt the rule for your backend accordingly
17detection:
18 selection:
19 Provider_Name: 'MSSQLSERVER'
20 EventID: 33205
21 Data|contains|all:
22 # You can modify this to include specific commands
23 - 'object_name:xp_cmdshell'
24 - 'statement:EXEC'
25 condition: selection
26falsepositives:
27 - Unknown
28level: high
References
Related rules
- AMSI Bypass Pattern Assembly GetType
- AWS EC2 Startup Shell Script Change
- Arbitrary Shell Command Execution Via Settingcontent-Ms
- Atlassian Confluence CVE-2022-26134
- Audit CVE Event