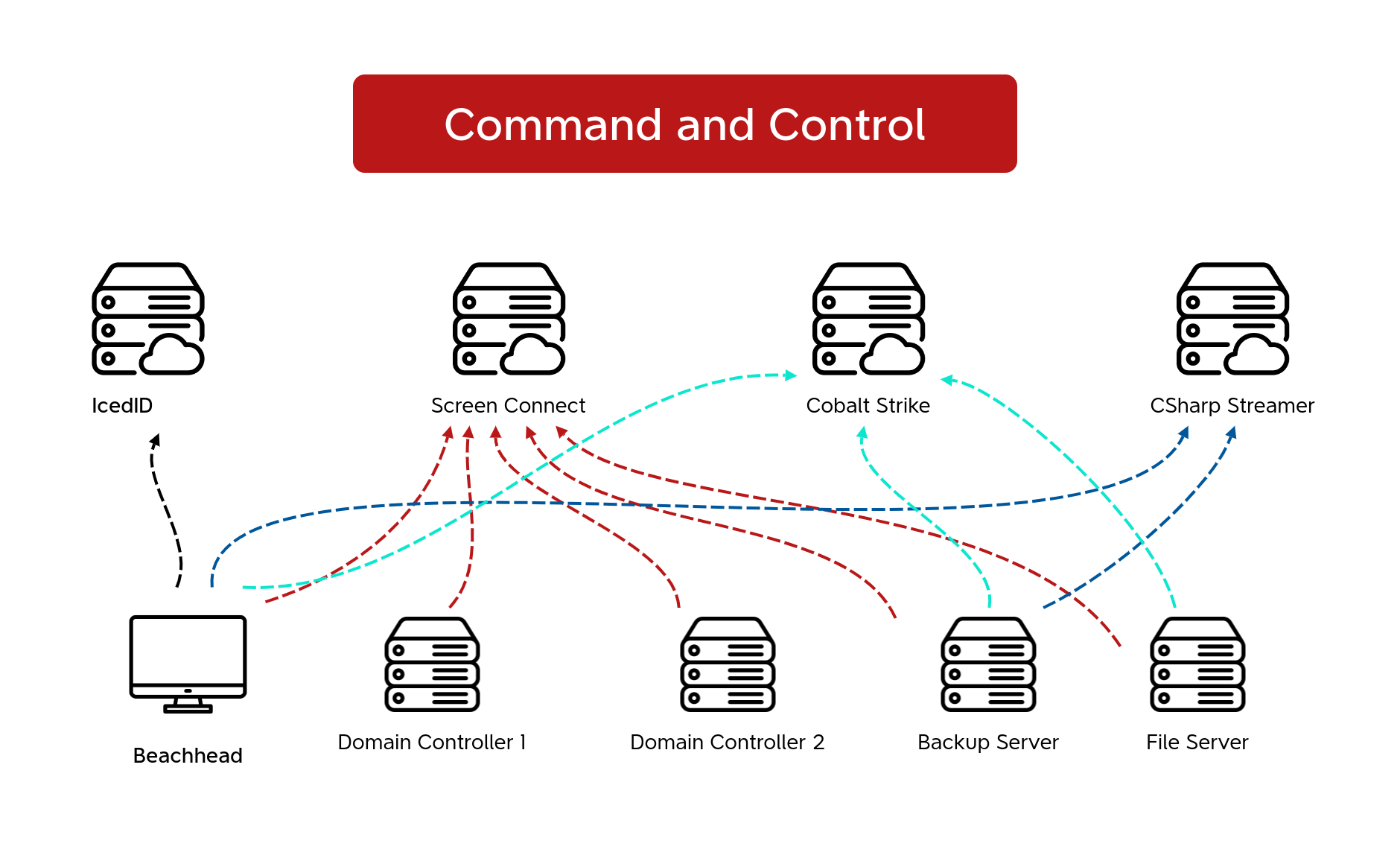
Potential CSharp Streamer RAT Loading .NET Executable Image
Detects potential CSharp Streamer RAT loading .NET executable image by using the default file name and path associated with the tool.
Sigma rule (View on GitHub)
1title: Potential CSharp Streamer RAT Loading .NET Executable Image
2id: 6f6afac3-8e7a-4e4b-9588-2608ffe08f82
3status: test
4description: |
5 Detects potential CSharp Streamer RAT loading .NET executable image by using the default file name and path associated with the tool.
6references:
7 - https://thedfirreport.com/2024/06/10/icedid-brings-screenconnect-and-csharp-streamer-to-alphv-ransomware-deployment/#detections
8 - https://cyber.wtf/2023/12/06/the-csharp-streamer-rat/
9author: Luca Di Bartolomeo
10date: 2024-06-22
11tags:
12 - attack.command-and-control
13 - attack.t1219.002
14 - detection.emerging-threats
15logsource:
16 category: image_load
17 product: windows
18detection:
19 selection:
20 ImageLoaded|re: '\\AppData\\Local\\Temp\\dat[0-9A-Z]{4}\.tmp'
21 condition: selection
22falsepositives:
23 - Unknown
24level: high
References
Related rules
- Potential SocGholish Second Stage C2 DNS Query
- Antivirus Exploitation Framework Detection
- Atera Agent Installation
- DNS Query To AzureWebsites.NET By Non-Browser Process
- DNS Query To Remote Access Software Domain From Non-Browser App