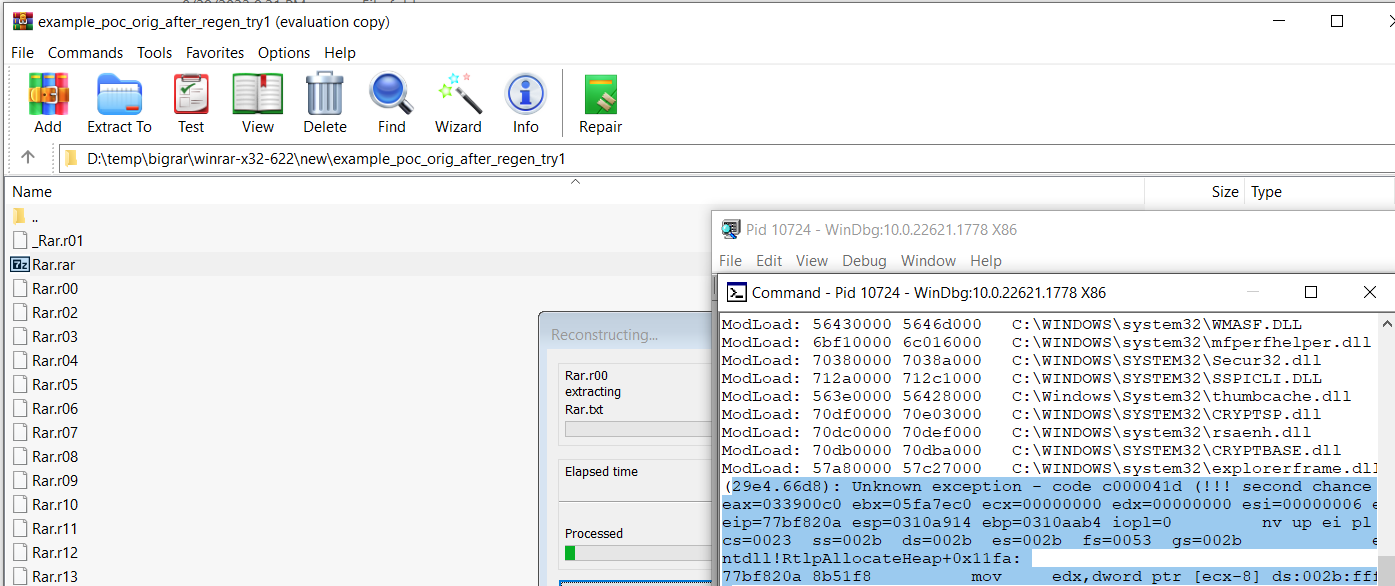
CVE-2023-40477 Potential Exploitation - .REV File Creation
Detects the creation of ".rev" files by WinRAR. Could be indicative of potential exploitation of CVE-2023-40477. Look for a suspicious execution shortly after creation or a WinRAR application crash.
Sigma rule (View on GitHub)
1title: CVE-2023-40477 Potential Exploitation - .REV File Creation
2id: c3bd6c55-d495-4c34-918e-e03e8828c074
3status: experimental
4description: Detects the creation of ".rev" files by WinRAR. Could be indicative of potential exploitation of CVE-2023-40477. Look for a suspicious execution shortly after creation or a WinRAR application crash.
5references:
6 - https://wildptr.io/winrar-cve-2023-40477-poc-new-vulnerability-winrar-security-research/
7 - https://github.com/wildptr-io/Winrar-CVE-2023-40477-POC
8 - https://www.rarlab.com/vuln_rev3_names.html
9author: Nasreddine Bencherchali (Nextron Systems)
10date: 2023/08/31
11tags:
12 - attack.execution
13 - cve.2023.40477
14 - detection.emerging_threats
15logsource:
16 category: file_event
17 product: windows
18detection:
19 selection:
20 Image|endswith:
21 - '\explorer.exe' # When extracted via context menu
22 - '\WinRAR.exe'
23 TargetFilename|endswith: '.rev'
24 condition: selection
25falsepositives:
26 - Legitimate extraction of multipart or recovery volumes ZIP files
27level: low
References
Related rules
- CVE-2023-40477 Potential Exploitation - WinRAR Application Crash
- CVE-2023-38331 Exploitation Attempt - Suspicious Double Extension File
- Potential CVE-2023-36874 Exploitation - Fake Wermgr Execution
- Potential CVE-2023-36874 Exploitation - Uncommon Report.Wer Location
- Potential BlackByte Ransomware Activity