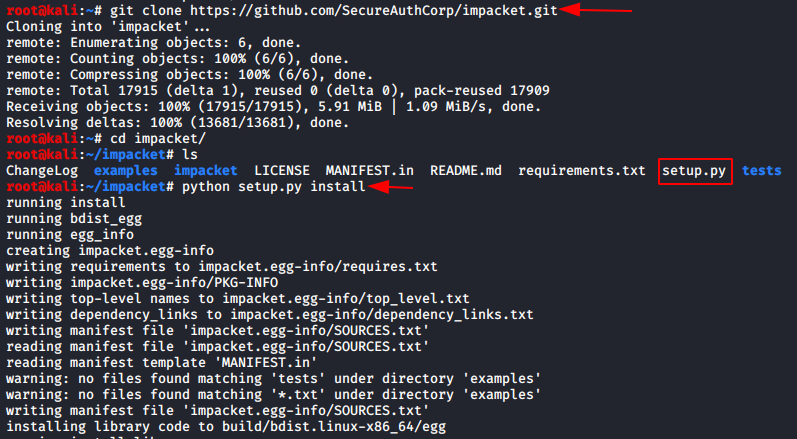
Possible Impacket AtExec Activity
Detect Impacket atexec.py usage in Windows task scheduler logs. If detected, these events will appear to be logged simultaneously and will all contain the same eight-letter task name.
Sigma rule (View on GitHub)
1title: Possible Impacket AtExec Activity
2id: eb2713cd-6e7d-4813-81d0-ced79de4c7da
3status: experimental
4description: Detect Impacket atexec.py usage in Windows task scheduler logs. If detected, these events will appear to be logged simultaneously and will all contain the same eight-letter task name.
5references:
6 - https://www.13cubed.com/downloads/impacket_exec_commands_cheat_sheet.pdf
7 - https://www.hackingarticles.in/impacket-guide-smb-msrpc/
8author: Micah Babinski
9date: 2023/01/05
10tags:
11 - attack.s0357
12 - attack.execution
13 - attack.t1053
14 - attack.t1053.002
15logsource:
16 product: windows
17 service: taskscheduler
18detection:
19 selection_task_registered:
20 EventID: 106
21 Message|re: '^.*registered\sTask\sScheduler\stask\s\"\\[A-Za-z]{8}\"$'
22 selection_created_task_process:
23 EventID: 129
24 Message|re: '^.*Task\sScheduler\slaunch\stask\s\"\\[A-Za-z]{8}\"\s,\sinstance\s\"cmd\.exe\".*$'
25 selection_action_started:
26 EventID: 200
27 Message|re: '^.*Task\sScheduler\slaunched\saction\s\"cmd\.exe\"\sin\sinstance\s\"\{.*\}\"\sof\stask\s"\\[A-Za-z]{8}\"\.$'
28 selection_registration_deleted:
29 EventID: 141
30 Message|re: '^.*deleted\sTask\sScheduler\stask\s"\\[A-Za-z]{8}\"$'
31 selection_action_completed:
32 EventID: 201
33 Message|re: '^Task\sScheduler\ssuccessfully\scompleted\stask\s"\\[A-Za-z]{8}\".*action\s\"cmd\.exe\"\swith\sreturn\scode\s\d\.$'
34 condition: 1 of selection*
35falsepositives:
36 - Unknown
37level: low
References
Related rules
- Impacket AtExec Suspicious Registry Modification
- Impacket AtExec Suspicious Temp File Creation
- Windows Scheduled Task Behaving Improperly or Suspiciously
- Windows Scheduled Task Create Shell
- Windows Scheduled Task Making Suspicious Network Connection