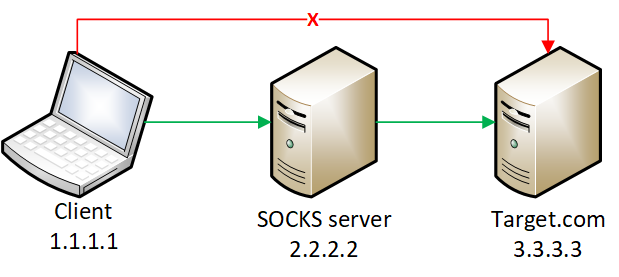
Potential Linux Tunneling and/or Port Forwarding via SSH Option
This rule detects the use of SSH options that may indicate tunneling or port forwarding on Linux systems. This behavior is commonly associated with malicious activity, such as establishing a port forward, proxy or an encrypted tunnel to exfiltrate data.
Elastic rule (View on GitHub)
1[metadata]
2creation_date = "2025/04/25"
3integration = ["endpoint", "crowdstrike", "sentinel_one_cloud_funnel"]
4maturity = "production"
5updated_date = "2026/02/20"
6
7[rule]
8author = ["Elastic"]
9description = """
10This rule detects the use of SSH options that may indicate tunneling or port forwarding on Linux systems. This behavior
11is commonly associated with malicious activity, such as establishing a port forward, proxy or an encrypted tunnel to
12exfiltrate data.
13"""
14from = "now-9m"
15index = [
16 "endgame-*",
17 "logs-crowdstrike.fdr*",
18 "logs-endpoint.events.process*",
19 "logs-sentinel_one_cloud_funnel.*",
20]
21language = "eql"
22license = "Elastic License v2"
23name = "Potential Linux Tunneling and/or Port Forwarding via SSH Option"
24note = """ ## Triage and analysis
25
26> **Disclaimer**:
27> This investigation guide was created using generative AI technology and has been reviewed to improve its accuracy and relevance. While every effort has been made to ensure its quality, we recommend validating the content and adapting it to suit your specific environment and operational needs.
28
29### Investigating Potential Linux Tunneling and/or Port Forwarding via SSH Option
30
31SSH is a secure protocol used for encrypted communication over networks, often employed for remote administration. Adversaries exploit SSH options like port forwarding to create tunnels, facilitating covert data exfiltration or unauthorized access. The detection rule identifies suspicious SSH commands indicative of tunneling by monitoring specific SSH options, helping to flag potential misuse for further investigation.
32
33### Possible investigation steps
34
35- Review the process command line details to identify the specific SSH options used, such as ProxyCommand, LocalForward, RemoteForward, DynamicForward, Tunnel, GatewayPorts, ExitOnForwardFailure, or ProxyJump, to understand the nature of the potential tunneling or port forwarding.
36- Examine the user account associated with the SSH process to determine if the activity aligns with their typical behavior or if it appears suspicious.
37- Check the source and destination IP addresses involved in the SSH connection to identify any unusual or unauthorized endpoints that may indicate malicious activity.
38- Investigate the timing and frequency of the SSH connections to assess whether they coincide with known business operations or if they suggest unauthorized access patterns.
39- Correlate the event with other security logs or alerts from the same host or network segment to identify any additional indicators of compromise or related suspicious activities.
40
41### False positive analysis
42
43- Legitimate administrative tasks using SSH options like ProxyCommand or LocalForward can trigger the rule. To manage this, create exceptions for known administrative scripts or users frequently using these options for valid purposes.
44- Automated backup or synchronization processes that use SSH tunneling for secure data transfer may be flagged. Identify these processes and exclude them by specifying the associated process names or user accounts.
45- Development or testing environments where developers use SSH tunneling for accessing remote services might cause alerts. Implement exceptions for specific IP addresses or user groups associated with these environments.
46- Monitoring or logging tools that utilize SSH for secure data collection can be mistaken for malicious activity. Whitelist these tools by their process names or command-line patterns to prevent false positives.
47- Internal network services that rely on SSH port forwarding for legitimate communication should be reviewed and excluded based on their known behavior and usage patterns.
48
49### Response and remediation
50
51- Immediately isolate the affected Linux system from the network to prevent further unauthorized access or data exfiltration.
52- Terminate any suspicious SSH sessions identified by the detection rule to halt potential tunneling or port forwarding activities.
53- Conduct a thorough review of SSH configuration files and logs on the affected system to identify unauthorized changes or access patterns.
54- Reset credentials for any accounts that were used in the suspicious SSH activity to prevent further unauthorized access.
55- Implement network segmentation to limit SSH access to only necessary systems and services, reducing the risk of lateral movement.
56- Escalate the incident to the security operations team for further investigation and to determine if additional systems are compromised.
57- Enhance monitoring and logging of SSH activities across the network to detect similar threats in the future, ensuring alerts are promptly reviewed and acted upon.
58"""
59references = [
60 "https://blog.bitsadmin.com/living-off-the-foreign-land-windows-as-offensive-platform",
61 "https://book.hacktricks.xyz/generic-methodologies-and-resources/tunneling-and-port-forwarding",
62]
63risk_score = 21
64rule_id = "ef395dff-be12-4a6e-8919-d87d627c2174"
65setup = """## Setup
66
67This rule requires data coming in from Elastic Defend.
68
69### Elastic Defend Integration Setup
70Elastic Defend is integrated into the Elastic Agent using Fleet. Upon configuration, the integration allows the Elastic Agent to monitor events on your host and send data to the Elastic Security app.
71
72#### Prerequisite Requirements:
73- Fleet is required for Elastic Defend.
74- To configure Fleet Server refer to the [documentation](https://www.elastic.co/guide/en/fleet/current/fleet-server.html).
75
76#### The following steps should be executed in order to add the Elastic Defend integration on a Linux System:
77- Go to the Kibana home page and click "Add integrations".
78- In the query bar, search for "Elastic Defend" and select the integration to see more details about it.
79- Click "Add Elastic Defend".
80- Configure the integration name and optionally add a description.
81- Select the type of environment you want to protect, either "Traditional Endpoints" or "Cloud Workloads".
82- Select a configuration preset. Each preset comes with different default settings for Elastic Agent, you can further customize these later by configuring the Elastic Defend integration policy. [Helper guide](https://www.elastic.co/guide/en/security/current/configure-endpoint-integration-policy.html).
83- We suggest selecting "Complete EDR (Endpoint Detection and Response)" as a configuration setting, that provides "All events; all preventions"
84- Enter a name for the agent policy in "New agent policy name". If other agent policies already exist, you can click the "Existing hosts" tab and select an existing policy instead.
85For more details on Elastic Agent configuration settings, refer to the [helper guide](https://www.elastic.co/guide/en/fleet/8.10/agent-policy.html).
86- Click "Save and Continue".
87- To complete the integration, select "Add Elastic Agent to your hosts" and continue to the next section to install the Elastic Agent on your hosts.
88For more details on Elastic Defend refer to the [helper guide](https://www.elastic.co/guide/en/security/current/install-endpoint.html).
89"""
90severity = "low"
91tags = [
92 "Domain: Endpoint",
93 "OS: Linux",
94 "Use Case: Threat Detection",
95 "Tactic: Command and Control",
96 "Data Source: Elastic Defend",
97 "Data Source: Elastic Endgame",
98 "Data Source: Crowdstrike",
99 "Data Source: SentinelOne",
100 "Resources: Investigation Guide",
101]
102timestamp_override = "event.ingested"
103type = "eql"
104query = '''
105process where host.os.type == "linux" and event.type == "start" and event.action in ("exec", "exec_event", "start", "ProcessRollup2") and
106process.name in ("ssh", "sshd") and process.args like "-o*" and
107process.command_line like~ (
108 "*ProxyCommand*", "*LocalForward*", "*RemoteForward*", "*DynamicForward*", "*Tunnel*", "*GatewayPorts*",
109 "*ExitOnForwardFailure*", "*ProxyCommand*", "*ProxyJump*"
110) and
111not (
112 ?process.parent.args == "/usr/bin/pvedaemon" or
113 ?process.parent.command_line in ("pvedaemon", "pve-ha-lrm") or
114 ?process.working_directory like "*ansible*" or
115 process.command_line like "*ansible*"
116)
117'''
118[[rule.threat]]
119framework = "MITRE ATT&CK"
120
121[[rule.threat.technique]]
122id = "T1572"
123name = "Protocol Tunneling"
124reference = "https://attack.mitre.org/techniques/T1572/"
125
126[rule.threat.tactic]
127id = "TA0011"
128name = "Command and Control"
129reference = "https://attack.mitre.org/tactics/TA0011/"
Triage and analysis
Disclaimer: This investigation guide was created using generative AI technology and has been reviewed to improve its accuracy and relevance. While every effort has been made to ensure its quality, we recommend validating the content and adapting it to suit your specific environment and operational needs.
Investigating Potential Linux Tunneling and/or Port Forwarding via SSH Option
SSH is a secure protocol used for encrypted communication over networks, often employed for remote administration. Adversaries exploit SSH options like port forwarding to create tunnels, facilitating covert data exfiltration or unauthorized access. The detection rule identifies suspicious SSH commands indicative of tunneling by monitoring specific SSH options, helping to flag potential misuse for further investigation.
Possible investigation steps
- Review the process command line details to identify the specific SSH options used, such as ProxyCommand, LocalForward, RemoteForward, DynamicForward, Tunnel, GatewayPorts, ExitOnForwardFailure, or ProxyJump, to understand the nature of the potential tunneling or port forwarding.
- Examine the user account associated with the SSH process to determine if the activity aligns with their typical behavior or if it appears suspicious.
- Check the source and destination IP addresses involved in the SSH connection to identify any unusual or unauthorized endpoints that may indicate malicious activity.
- Investigate the timing and frequency of the SSH connections to assess whether they coincide with known business operations or if they suggest unauthorized access patterns.
- Correlate the event with other security logs or alerts from the same host or network segment to identify any additional indicators of compromise or related suspicious activities.
False positive analysis
- Legitimate administrative tasks using SSH options like ProxyCommand or LocalForward can trigger the rule. To manage this, create exceptions for known administrative scripts or users frequently using these options for valid purposes.
- Automated backup or synchronization processes that use SSH tunneling for secure data transfer may be flagged. Identify these processes and exclude them by specifying the associated process names or user accounts.
- Development or testing environments where developers use SSH tunneling for accessing remote services might cause alerts. Implement exceptions for specific IP addresses or user groups associated with these environments.
- Monitoring or logging tools that utilize SSH for secure data collection can be mistaken for malicious activity. Whitelist these tools by their process names or command-line patterns to prevent false positives.
- Internal network services that rely on SSH port forwarding for legitimate communication should be reviewed and excluded based on their known behavior and usage patterns.
Response and remediation
- Immediately isolate the affected Linux system from the network to prevent further unauthorized access or data exfiltration.
- Terminate any suspicious SSH sessions identified by the detection rule to halt potential tunneling or port forwarding activities.
- Conduct a thorough review of SSH configuration files and logs on the affected system to identify unauthorized changes or access patterns.
- Reset credentials for any accounts that were used in the suspicious SSH activity to prevent further unauthorized access.
- Implement network segmentation to limit SSH access to only necessary systems and services, reducing the risk of lateral movement.
- Escalate the incident to the security operations team for further investigation and to determine if additional systems are compromised.
- Enhance monitoring and logging of SSH activities across the network to detect similar threats in the future, ensuring alerts are promptly reviewed and acted upon.
References
Related rules
- Potential Linux Tunneling and/or Port Forwarding
- Potential Traffic Tunneling using QEMU
- Kubectl Network Configuration Modification
- Curl or Wget Spawned via Node.js
- Simple HTTP Web Server Creation