Entra ID Federated Identity Credential Issuer Modified
Detects when the issuer URL of a federated identity credential is changed on an Entra ID application. Adversaries may modify the issuer to point to an attacker-controlled identity provider, enabling them to authenticate as the application's service principal and gain persistent access to Azure resources. This technique allows bypassing traditional authentication controls by federating trust with a malicious external identity provider.
Elastic rule (View on GitHub)
1[metadata]
2creation_date = "2025/07/14"
3integration = ["azure"]
4maturity = "production"
5updated_date = "2026/02/06"
6
7[rule]
8author = ["Elastic"]
9description = """
10Detects when the issuer URL of a federated identity credential is changed on an Entra ID application. Adversaries may
11modify the issuer to point to an attacker-controlled identity provider, enabling them to authenticate as the
12application's service principal and gain persistent access to Azure resources. This technique allows bypassing
13traditional authentication controls by federating trust with a malicious external identity provider.
14"""
15from = "now-9m"
16language = "esql"
17license = "Elastic License v2"
18name = "Entra ID Federated Identity Credential Issuer Modified"
19note = """## Triage and analysis
20
21### Investigating Entra ID Federated Identity Credential Issuer Modified
22
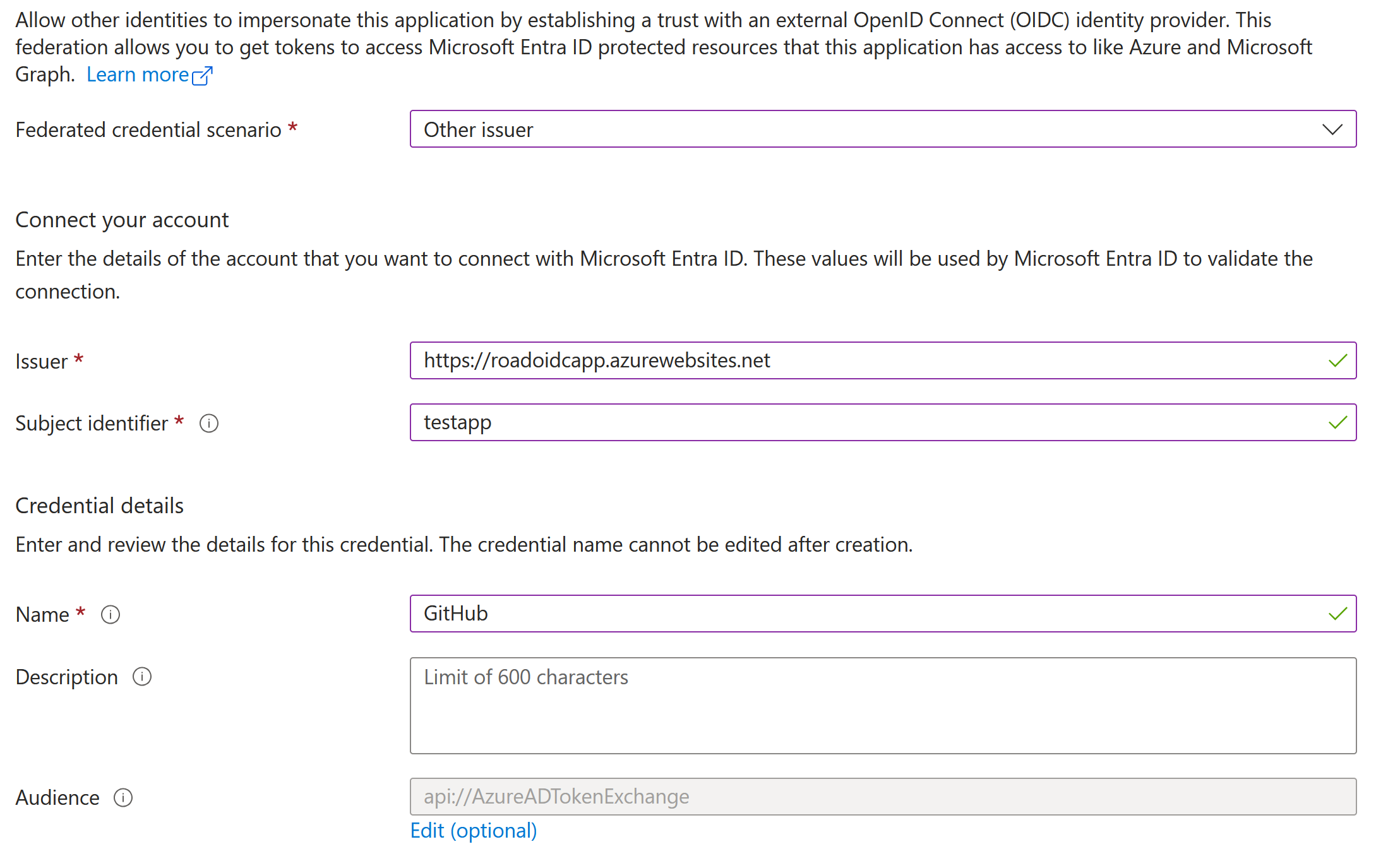
23This rule detects when the issuer URL within a federated identity credential is modified on an Entra ID application. Federated identity credentials allow applications to authenticate using tokens from external identity providers (like GitHub Actions, AWS, etc.) without managing secrets. Adversaries can abuse this by changing the issuer to an attacker-controlled identity provider, allowing them to generate valid tokens and authenticate as the application's service principal.
24
25This technique provides persistent access to Azure resources with the application's permissions and bypasses secret-based authentication controls.
26
27### Possible investigation steps
28
29- Review `azure.auditlogs.properties.initiated_by.user.userPrincipalName` and `ipAddress` to identify who made the change and from where.
30- Examine the `Esql.external_idp_old_issuer` and `Esql.external_idp_new_issuer` fields to determine if the new issuer is expected or potentially malicious.
31- Check if the new issuer domain is controlled by the organization or if it's an external/suspicious domain.
32- Review the application's assigned roles and permissions to understand the scope of access gained.
33- Use `azure.correlation_id` to pivot to related changes in the same session.
34- Check for subsequent Azure sign-in activity using the modified federated credential.
35- Investigate if the application has been used to access sensitive resources after the change.
36
37### False positive analysis
38
39- Legitimate migrations from one identity provider to another (e.g., GitHub to GitLab) may trigger this detection.
40- DevOps teams may update issuer URLs as part of CI/CD pipeline changes.
41- Validate any changes with the application owner or DevOps team before taking action.
42
43### Response and remediation
44
45- If the change is unauthorized, immediately remove or revert the federated identity credential.
46- Rotate any secrets or certificates associated with the application.
47- Review Azure sign-in logs and audit logs for any unauthorized activity using the application's identity.
48- Disable the application or service principal if compromise is confirmed.
49- Investigate how the unauthorized change occurred (e.g., compromised admin account, over-privileged service principal).
50- Implement conditional access policies and PIM (Privileged Identity Management) to protect application management operations.
51"""
52references = [
53 "https://dirkjanm.io/persisting-with-federated-credentials-entra-apps-managed-identities/",
54 "https://learn.microsoft.com/en-us/entra/workload-id/workload-identity-federation",
55]
56risk_score = 73
57rule_id = "498e4094-60e7-11f0-8847-f661ea17fbcd"
58setup = """### Microsft Entra ID Audit Logs
59This rule requires the Azure integration with Microsoft Entra ID Audit Logs data stream ingesting in your Elastic Stack deployment. For more information, refer to the [Microsoft Entra ID Audit Logs integration documentation](https://www.elastic.co/docs/reference/integrations/azure/adlogs).
60"""
61severity = "high"
62tags = [
63 "Domain: Cloud",
64 "Domain: Identity",
65 "Data Source: Azure",
66 "Data Source: Microsoft Entra ID",
67 "Data Source: Microsoft Entra ID Audit Logs",
68 "Use Case: Identity and Access Audit",
69 "Tactic: Persistence",
70 "Tactic: Privilege Escalation",
71 "Resources: Investigation Guide",
72]
73timestamp_override = "event.ingested"
74type = "esql"
75
76query = '''
77from logs-azure.auditlogs-* metadata _id, _version, _index
78| where event.action == "Update application"
79| where `azure.auditlogs.properties.target_resources.0.modified_properties.0.display_name` == "FederatedIdentityCredentials"
80| eval Esql.target_resources_old_value_clean = replace(`azure.auditlogs.properties.target_resources.0.modified_properties.0.old_value`, "\\\\", "")
81| eval Esql.target_resources_new_value_clean = replace(`azure.auditlogs.properties.target_resources.0.modified_properties.0.new_value`, "\\\\", "")
82| dissect Esql.target_resources_old_value_clean "%{}\"Issuer\":\"%{Esql.external_idp_old_issuer}\"%{}"
83| dissect Esql.target_resources_new_value_clean "%{}\"Issuer\":\"%{Esql.external_idp_new_issuer}\"%{}"
84| where Esql.external_idp_old_issuer is not null and Esql.external_idp_new_issuer is not null
85| where Esql.external_idp_old_issuer != Esql.external_idp_new_issuer
86| keep @timestamp, Esql.*, azure.*, event.*, cloud.*, related.*, tags, source.*, agent.*, client.*, _id, _version, _index, data_stream.namespace
87'''
88
89
90[[rule.threat]]
91framework = "MITRE ATT&CK"
92[[rule.threat.technique]]
93id = "T1098"
94name = "Account Manipulation"
95reference = "https://attack.mitre.org/techniques/T1098/"
96[[rule.threat.technique.subtechnique]]
97id = "T1098.001"
98name = "Additional Cloud Credentials"
99reference = "https://attack.mitre.org/techniques/T1098/001/"
100
101
102
103[rule.threat.tactic]
104id = "TA0003"
105name = "Persistence"
106reference = "https://attack.mitre.org/tactics/TA0003/"
107[[rule.threat]]
108framework = "MITRE ATT&CK"
109[[rule.threat.technique]]
110id = "T1484"
111name = "Domain or Tenant Policy Modification"
112reference = "https://attack.mitre.org/techniques/T1484/"
113[[rule.threat.technique.subtechnique]]
114id = "T1484.002"
115name = "Trust Modification"
116reference = "https://attack.mitre.org/techniques/T1484/002/"
117
118
119
120[rule.threat.tactic]
121id = "TA0004"
122name = "Privilege Escalation"
123reference = "https://attack.mitre.org/tactics/TA0004/"
Triage and analysis
Investigating Entra ID Federated Identity Credential Issuer Modified
This rule detects when the issuer URL within a federated identity credential is modified on an Entra ID application. Federated identity credentials allow applications to authenticate using tokens from external identity providers (like GitHub Actions, AWS, etc.) without managing secrets. Adversaries can abuse this by changing the issuer to an attacker-controlled identity provider, allowing them to generate valid tokens and authenticate as the application's service principal.
This technique provides persistent access to Azure resources with the application's permissions and bypasses secret-based authentication controls.
Possible investigation steps
- Review
azure.auditlogs.properties.initiated_by.user.userPrincipalNameandipAddressto identify who made the change and from where. - Examine the
Esql.external_idp_old_issuerandEsql.external_idp_new_issuerfields to determine if the new issuer is expected or potentially malicious. - Check if the new issuer domain is controlled by the organization or if it's an external/suspicious domain.
- Review the application's assigned roles and permissions to understand the scope of access gained.
- Use
azure.correlation_idto pivot to related changes in the same session. - Check for subsequent Azure sign-in activity using the modified federated credential.
- Investigate if the application has been used to access sensitive resources after the change.
False positive analysis
- Legitimate migrations from one identity provider to another (e.g., GitHub to GitLab) may trigger this detection.
- DevOps teams may update issuer URLs as part of CI/CD pipeline changes.
- Validate any changes with the application owner or DevOps team before taking action.
Response and remediation
- If the change is unauthorized, immediately remove or revert the federated identity credential.
- Rotate any secrets or certificates associated with the application.
- Review Azure sign-in logs and audit logs for any unauthorized activity using the application's identity.
- Disable the application or service principal if compromise is confirmed.
- Investigate how the unauthorized change occurred (e.g., compromised admin account, over-privileged service principal).
- Implement conditional access policies and PIM (Privileged Identity Management) to protect application management operations.
References
Related rules
- Entra ID Unusual Cloud Device Registration
- Entra ID Elevated Access to User Access Administrator
- Entra ID Global Administrator Role Assigned
- Entra ID MFA Disabled for User
- Entra ID Service Principal Federated Credential Authentication by Unusual Client