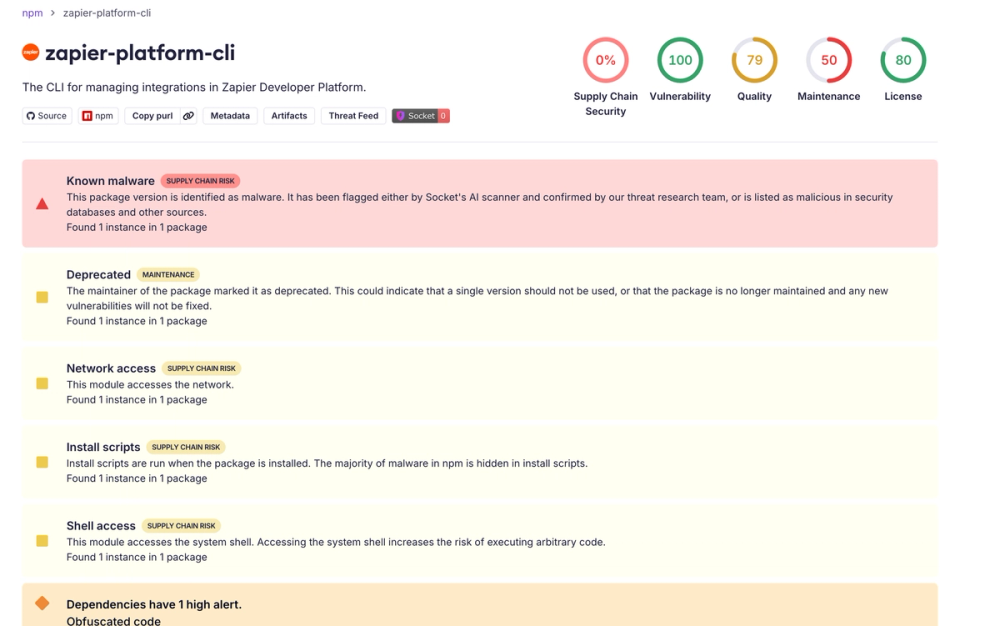
Credential Access via TruffleHog Execution
This rule detects the execution of TruffleHog, a tool used to search for high-entropy strings and secrets in code repositories, which may indicate an attempt to access credentials. This tool was abused by the Shai-Hulud worm to search for credentials in code repositories.
Elastic rule (View on GitHub)
1[metadata]
2creation_date = "2025/09/18"
3integration = ["endpoint", "windows", "system", "m365_defender", "sentinel_one_cloud_funnel", "crowdstrike", "auditd_manager"]
4maturity = "production"
5updated_date = "2025/11/26"
6
7[rule]
8author = ["Elastic"]
9description = """
10This rule detects the execution of TruffleHog, a tool used to search for high-entropy strings and secrets
11in code repositories, which may indicate an attempt to access credentials. This tool was abused by the Shai-Hulud
12worm to search for credentials in code repositories.
13"""
14false_positives = [
15 """
16 Trufflehog is a legitimate open-source tool used by security professionals and developers to search for sensitive
17 information, such as passwords, API keys, and other secrets, within code repositories. It is commonly employed
18 during security assessments and code reviews to identify potential vulnerabilities.
19 """,
20]
21from = "now-9m"
22index = [
23 "endgame-*",
24 "logs-crowdstrike.fdr*",
25 "logs-endpoint.events.process-*",
26 "logs-m365_defender.event-*",
27 "logs-sentinel_one_cloud_funnel.*",
28 "logs-system.security*",
29 "logs-windows.forwarded*",
30 "logs-windows.sysmon_operational-*",
31 "winlogbeat-*",
32 "auditbeat-*",
33 "logs-auditd_manager.auditd-*"
34]
35language = "eql"
36license = "Elastic License v2"
37name = "Credential Access via TruffleHog Execution"
38note = """## Triage and analysis
39
40> **Disclaimer**:
41> This investigation guide was created using generative AI technology and has been reviewed to improve its accuracy and relevance. While every effort has been made to ensure its quality, we recommend validating the content and adapting it to suit your specific environment and operational needs.
42
43### Investigating Credential Access via TruffleHog Execution
44
45This rule flags TruffleHog executed to scan the local filesystem with verified JSON results, a direct path to harvesting secrets from source code, configs, and build artifacts. Attackers gain shell access on a developer workstation or CI runner, clone or point to internal repositories, run 'trufflehog --results=verified --json filesystem .' to enumerate valid tokens, and then pivot using the recovered keys to pull private code or authenticate to cloud and CI/CD systems.
46
47### Possible investigation steps
48
49- Review binary path, code signature/hash, parent process chain, initiating user, and host role (developer workstation vs CI runner) to quickly decide if the execution matches an approved secret-scanning job or an ad‑hoc run.
50- Determine the working directory and target path used by the scan to identify which repositories or configuration directories were inspected and whether sensitive files (e.g., .env, deployment keys, build secrets) were in scope.
51- Pivot to same-session activity to spot credential use or exfiltration by correlating subsequent outbound connections to git remotes or cloud/CI APIs and launches of developer CLIs like git, gh, aws, az, gcloud, docker, kubectl, or vault.
52- Look for output artifacts and exfil channels by checking for creation or deletion of JSON reports or archives, clipboard access, or piping of results to curl/wget/netcat and whether those artifacts were emailed or uploaded externally.
53- Cross-check VCS and CI/CD audit logs for this identity and host for unusual pushes, pipeline changes, or new tokens issued shortly after the scan, which may indicate worm-like propagation or credential abuse.
54
55### False positive analysis
56
57- An approved secret-scanning task by a developer or security engineer runs trufflehog with --results=verified --json filesystem to audit local code and configuration, producing benign activity on a development host.
58- An internal automation or scheduled job invokes trufflehog to baseline filesystem secrets for compliance or hygiene checks, leading to expected process-start logs without credential abuse.
59
60### Response and remediation
61
62- Immediately isolate the host or CI runner, terminate the trufflehog process and its parent shell/script, and block egress to git remotes and cloud APIs from that asset.
63- Collect the verified findings from trufflehog output (stdout or JSON file), revoke and rotate any listed secrets (GitHub personal access tokens, AWS access keys, Azure service principal credentials, CI job tokens), and clear credential caches on the host.
64- Remove unauthorized trufflehog binaries/packages, helper scripts, and scheduled tasks; delete report files and scanned working directories (local repo clones, .env/config folders), and purge shell history containing exfil commands like curl/wget/netcat.
65- Restore the workstation or runner from a known-good image if tampering is suspected, re-enroll endpoint protection, reissue required developer or CI credentials with least privilege, and validate normal pulls to internal git and cloud services.
66- Escalate to full incident response if trufflehog ran under a service account, on a build server/CI runner, or if any discovered secret was used to authenticate to external git remotes (e.g., github.com), cloud APIs, or private registries in the same session.
67- Harden by blocking unapproved trufflehog execution via application control, moving approved secret scanning to a locked-down pipeline, enforcing short-lived PATs and key rotation, enabling egress filtering from developer hosts/runners, and deploying fleet-wide detections for "trufflehog --results=verified --json filesystem".
68"""
69references = [
70 "https://www.elastic.co/blog/shai-hulud-worm-npm-supply-chain-compromise",
71 "https://socket.dev/blog/shai-hulud-strikes-again-v2",
72]
73risk_score = 47
74rule_id = "47595dea-452b-4d37-b82d-6dd691325139"
75severity = "medium"
76tags = [
77 "Domain: Endpoint",
78 "OS: Linux",
79 "OS: Windows",
80 "OS: macOS",
81 "Use Case: Threat Detection",
82 "Tactic: Credential Access",
83 "Data Source: Elastic Endgame",
84 "Data Source: Elastic Defend",
85 "Data Source: Windows Security Event Logs",
86 "Data Source: Microsoft Defender for Endpoint",
87 "Data Source: Sysmon",
88 "Data Source: SentinelOne",
89 "Data Source: Crowdstrike",
90 "Data Source: Auditd Manager",
91 "Resources: Investigation Guide",
92]
93timestamp_override = "event.ingested"
94type = "eql"
95query = '''
96process where event.type == "start" and process.name : ("trufflehog.exe", "trufflehog") and
97process.args == "--json" and process.args == "filesystem"
98'''
99
100[[rule.threat]]
101framework = "MITRE ATT&CK"
102
103[[rule.threat.technique]]
104id = "T1003"
105name = "OS Credential Dumping"
106reference = "https://attack.mitre.org/techniques/T1003/"
107
108[[rule.threat.technique]]
109id = "T1555"
110name = "Credentials from Password Stores"
111reference = "https://attack.mitre.org/techniques/T1555/"
112
113[rule.threat.tactic]
114id = "TA0006"
115name = "Credential Access"
116reference = "https://attack.mitre.org/tactics/TA0006/"
Triage and analysis
Disclaimer: This investigation guide was created using generative AI technology and has been reviewed to improve its accuracy and relevance. While every effort has been made to ensure its quality, we recommend validating the content and adapting it to suit your specific environment and operational needs.
Investigating Credential Access via TruffleHog Execution
This rule flags TruffleHog executed to scan the local filesystem with verified JSON results, a direct path to harvesting secrets from source code, configs, and build artifacts. Attackers gain shell access on a developer workstation or CI runner, clone or point to internal repositories, run 'trufflehog --results=verified --json filesystem .' to enumerate valid tokens, and then pivot using the recovered keys to pull private code or authenticate to cloud and CI/CD systems.
Possible investigation steps
- Review binary path, code signature/hash, parent process chain, initiating user, and host role (developer workstation vs CI runner) to quickly decide if the execution matches an approved secret-scanning job or an ad‑hoc run.
- Determine the working directory and target path used by the scan to identify which repositories or configuration directories were inspected and whether sensitive files (e.g., .env, deployment keys, build secrets) were in scope.
- Pivot to same-session activity to spot credential use or exfiltration by correlating subsequent outbound connections to git remotes or cloud/CI APIs and launches of developer CLIs like git, gh, aws, az, gcloud, docker, kubectl, or vault.
- Look for output artifacts and exfil channels by checking for creation or deletion of JSON reports or archives, clipboard access, or piping of results to curl/wget/netcat and whether those artifacts were emailed or uploaded externally.
- Cross-check VCS and CI/CD audit logs for this identity and host for unusual pushes, pipeline changes, or new tokens issued shortly after the scan, which may indicate worm-like propagation or credential abuse.
False positive analysis
- An approved secret-scanning task by a developer or security engineer runs trufflehog with --results=verified --json filesystem to audit local code and configuration, producing benign activity on a development host.
- An internal automation or scheduled job invokes trufflehog to baseline filesystem secrets for compliance or hygiene checks, leading to expected process-start logs without credential abuse.
Response and remediation
- Immediately isolate the host or CI runner, terminate the trufflehog process and its parent shell/script, and block egress to git remotes and cloud APIs from that asset.
- Collect the verified findings from trufflehog output (stdout or JSON file), revoke and rotate any listed secrets (GitHub personal access tokens, AWS access keys, Azure service principal credentials, CI job tokens), and clear credential caches on the host.
- Remove unauthorized trufflehog binaries/packages, helper scripts, and scheduled tasks; delete report files and scanned working directories (local repo clones, .env/config folders), and purge shell history containing exfil commands like curl/wget/netcat.
- Restore the workstation or runner from a known-good image if tampering is suspected, re-enroll endpoint protection, reissue required developer or CI credentials with least privilege, and validate normal pulls to internal git and cloud services.
- Escalate to full incident response if trufflehog ran under a service account, on a build server/CI runner, or if any discovered secret was used to authenticate to external git remotes (e.g., github.com), cloud APIs, or private registries in the same session.
- Harden by blocking unapproved trufflehog execution via application control, moving approved secret scanning to a locked-down pipeline, enforcing short-lived PATs and key rotation, enabling egress filtering from developer hosts/runners, and deploying fleet-wide detections for "trufflehog --results=verified --json filesystem".
References
Related rules
- Potential Secret Scanning via Gitleaks
- Execution via GitHub Actions Runner
- Remote GitHub Actions Runner Registration
- Credential Acquisition via Registry Hive Dumping
- Microsoft IIS Connection Strings Decryption