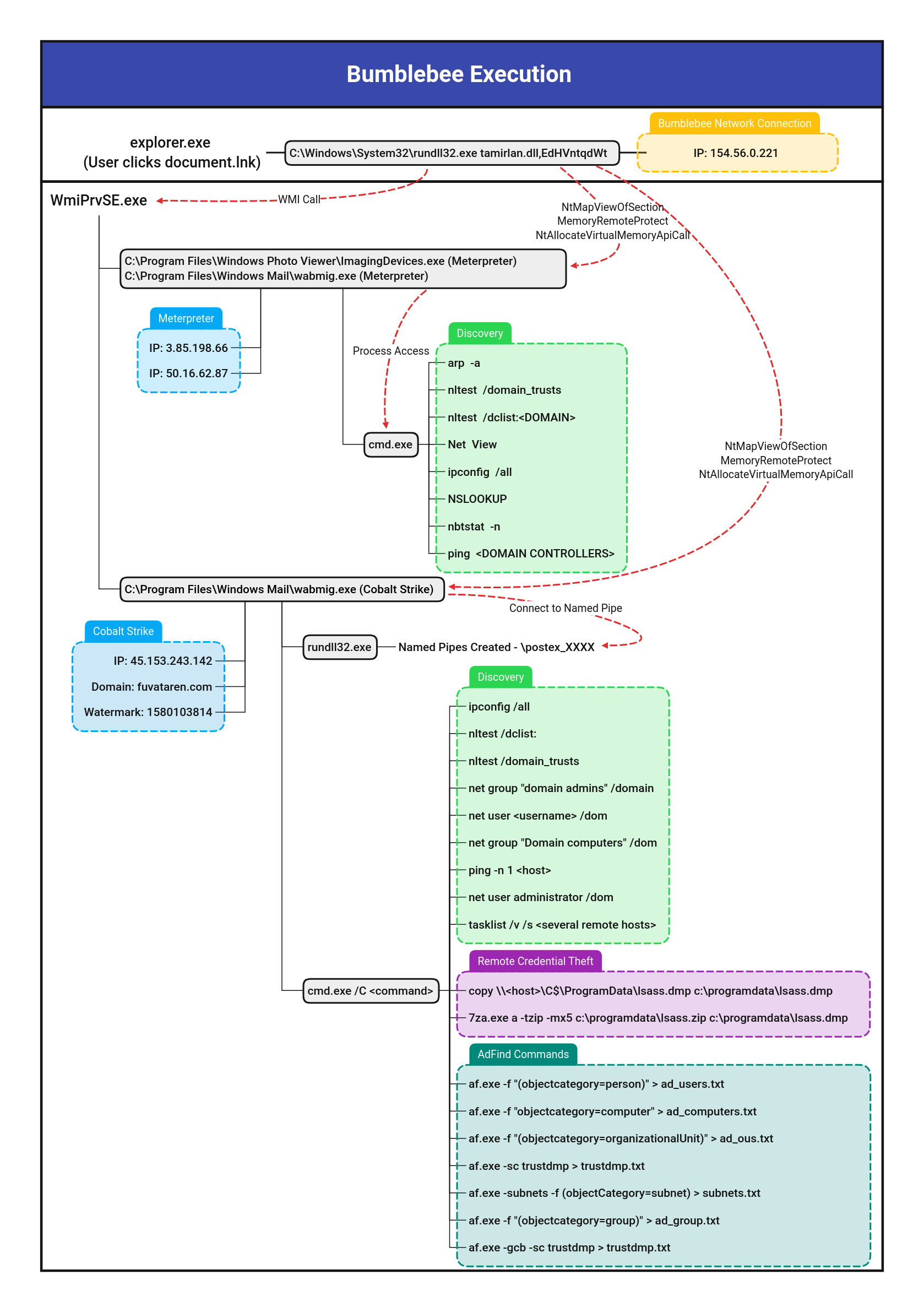
Bumblebee WmiPrvSE execution pattern
Detects Bumblebee WmiPrvSE parent process manipulation
Sigma rule (View on GitHub)
1title: Bumblebee WmiPrvSE execution pattern
2id: 1620db43-fde5-45f3-b4d9-45ca6e79e047
3status: experimental
4description: Detects Bumblebee WmiPrvSE parent process manipulation
5author: TheDFIRReport
6references:
7 - https://thedfirreport.com/2022/09/26/bumblebee-round-two/
8date: 2022/09/26
9logsource:
10 category: process_creation
11 product: windows
12detection:
13 selection_image:
14 Image|endswith:
15 - 'ImagingDevices.exe'
16 - 'wabmig.exe'
17 selection_parent:
18 ParentImage:endswith:
19 - 'WmiPrvSE.exe'
20 condition: selection_image and selection_parent
21falsepositives:
22 - Unknown
23level: high
24tags:
25 - attack.defense_evasion
26 - attack.t1036
yaml
References
Related rules
- Suspicious Use of Rcedit Utility to Alter Executable Metadata
- Command or Scripting Interpreter Creating EXE File
- File Creation of Executables in Temp Folders (Event 4663)
- Process Creation without .exe File Extension
- Svchost Not Matching Normal Execution Parameters