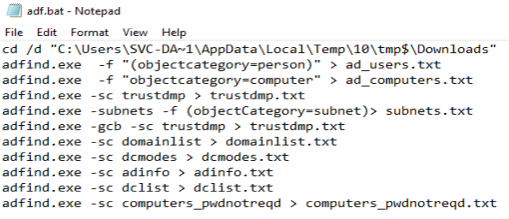
AdFind Discovery
AdFind has been seen in numerous intrusions. The threat actor(s) ran these commands.
Sigma rule (View on GitHub)
1title: AdFind Discovery
2id: 50046619-1037-49d7-91aa-54fc92923604
3description: AdFind has been seen in numerous intrusions. The threat actor(s) ran these commands.
4author: 'The DFIR Report'
5date: 2022-05-14
6modified: 2024-02-23
7references:
8 - https://thedfirreport.com/2020/05/08/adfind-recon/
9 - https://thedfirreport.com/?s=adfind
10logsource:
11 category: process_creation
12 product: windows
13detection:
14 selection:
15 CommandLine|contains:
16 - 'adfind -gcb -sc trustdmp'
17 - 'adfind -f "(objectcategory=group)"'
18 - 'adfind -f (objectcategory=group)'
19 - 'adfind -subnets -f (objectCategory=subnet)'
20 - 'adfind -sc trustdmp'
21 - 'adfind -f "(objectcategory=organizationalUnit)"'
22 - 'adfind -f (objectcategory=organizationalUnit)'
23 - 'adfind -f "objectcategory=computer"'
24 - 'adfind -f objectcategory=computer'
25 - 'adfind -f "(objectcategory=person)"'
26 - 'adfind -f (objectcategory=person)'
27 renamed:
28 CommandLine|contains:
29 - '-gcb -sc trustdmp'
30 - '-f "(objectcategory=group)"'
31 - '-f (objectcategory=group)'
32 - '-subnets -f (objectCategory=subnet)'
33 - '-sc trustdmp'
34 - '-f "(objectcategory=organizationalUnit)"'
35 - '-f (objectcategory=organizationalUnit)'
36 - '-f "objectcategory=computer"'
37 - '-f objectcategory=computer'
38 - '-f "(objectcategory=person)"'
39 - '-f (objectcategory=person)'
40 condition: selection or renamed
41falsepositives:
42 - Legitimate Administrator using tool for Active Directory querying.
43level: medium
44status: stable
45tags:
46 - attack.discovery
47 - attack.t1018
48 - attack.t1482
49 - attack.t1069.002
50 - attack.t1087.002
51 - attack.s0552
References
Related rules
- Domain User Enumeration Network Recon 01
- SocGholish NLTest Domain Trust Enumeration (RedCanary Threat Detection Report)
- Enumeration via the Global Catalog
- Invoke-ShareFinder Discovery Activity
- Invoke-ShareFinder Discovery Activity