JavaScript Execution Using MSDOS 8.3 File Notation
Detects script execution using MSDOS 8.3 File names
Sigma rule (View on GitHub)
1title: JavaScript Execution Using MSDOS 8.3 File Notation
2id: 81cfbbae-5e93-4934-84a2-e6a26f85c7bb
3related:
4 - id: dd6b39d9-d9be-4a3b-8fe0-fe3c6a5c1795
5 type: similar
6status: test
7description: Detects script execution using MSDOS 8.3 File names
8references:
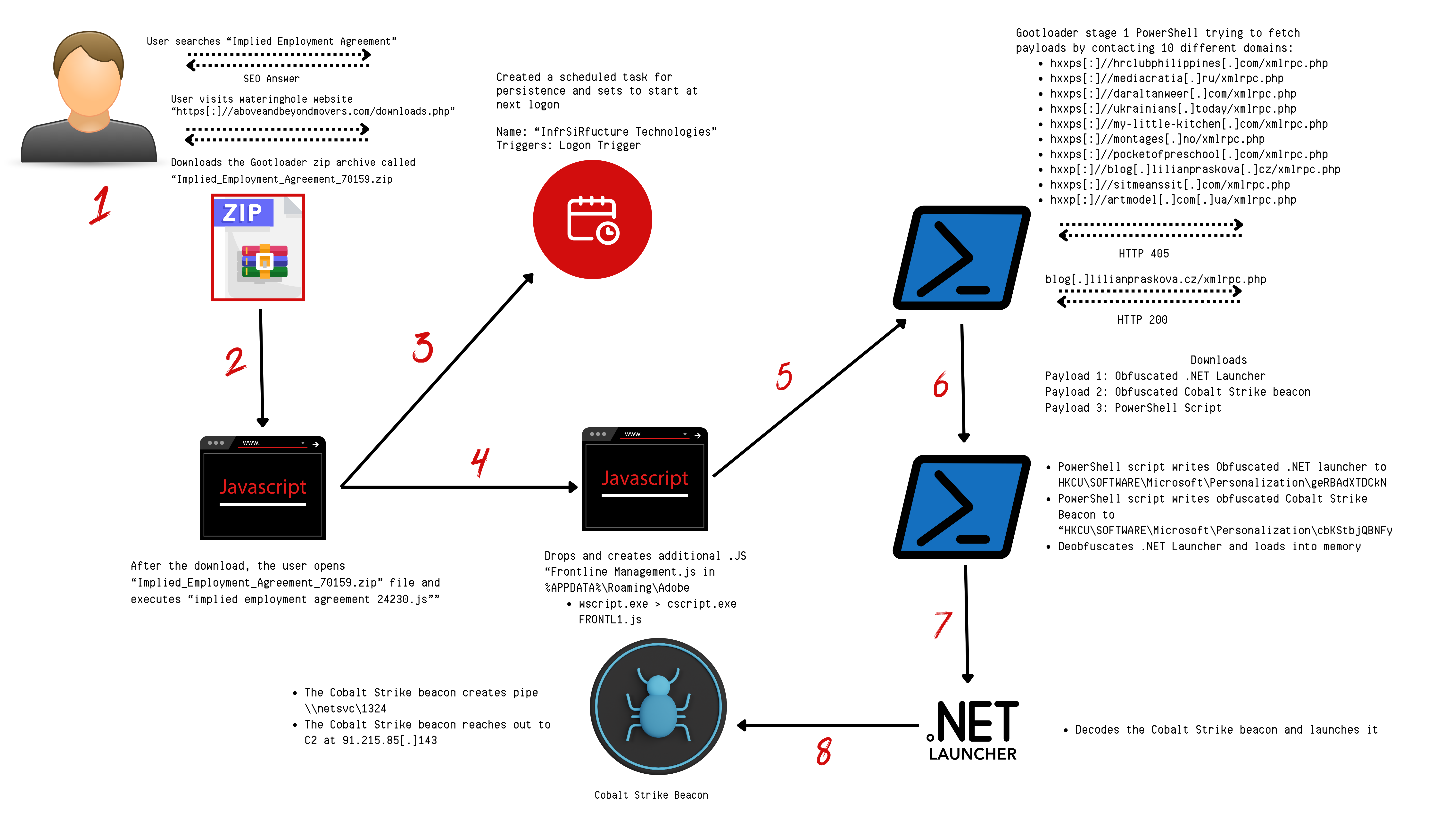
9 - https://thedfirreport.com/2024/02/26/seo-poisoning-to-domain-control-the-gootloader-saga-continues/
10author: _pete_0, TheDFIRReport
11date: 2024-02-13
12tags:
13 - attack.defense_evasion
14 - attack.t1059
15 - dist.public
16logsource:
17 category: process_creation
18 product: windows
19detection:
20 selection:
21 CommandLine|contains:
22 - '~1.js'
23 Image|endswith:
24 - '\wscript.exe'
25 - '\cscript.exe'
26 condition: selection
27falsepositives:
28 - Unknown
29level: medium
References
Related rules
- FlawedGrace spawning threat injection target
- Conhost Suspicious Command Execution
- Disable Windows Defender via Service
- Custom Cobalt Strike Command Execution
- Deleting Windows Defender scheduled tasks