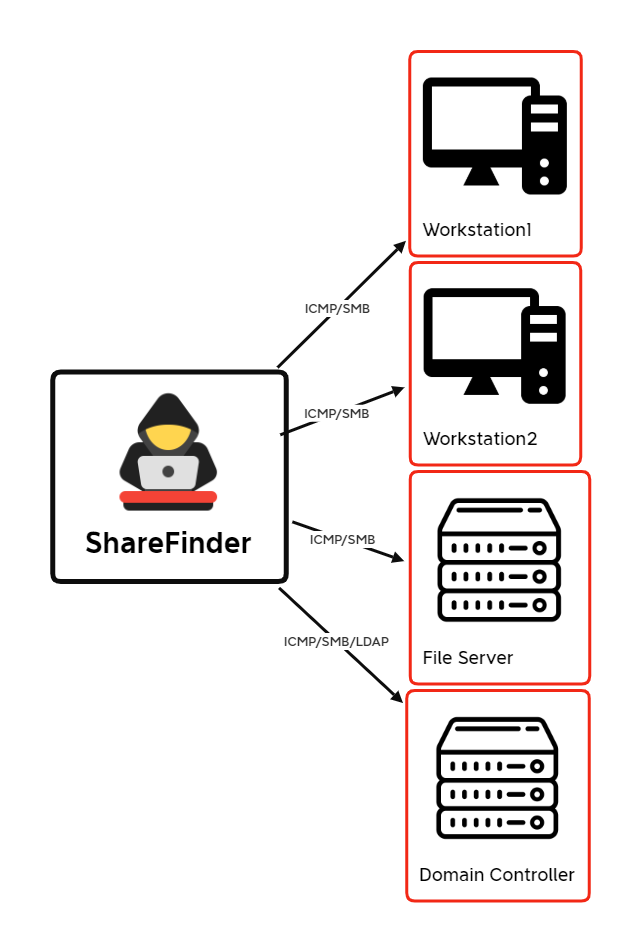
Invoke-ShareFinder Discovery Activity
Use of Invoke-ShareFinder detected via PowerShell Script Block logging
Sigma rule (View on GitHub)
1title: Invoke-ShareFinder Discovery Activity
2id: 5e93e240-5484-458a-9663-18157e01e897
3status: experimental
4description: |
5 Use of Invoke-ShareFinder detected via PowerShell Script Block logging
6references:
7 - https://thedfirreport.com/2023/01/23/sharefinder-how-threat-actors-discover-file-shares/
8 - https://powersploit.readthedocs.io/en/stable/Recon/README/
9
10author: TheDFIRReport
11date: 2023-01-23
12modified: 2024-02-23
13tags:
14 - attack.discovery
15 - attack.t1135
16logsource:
17 product: windows
18 service: powershell
19 definition: 'Requirements: Script Block Logging must be enabled'
20detection:
21 selection:
22 ScriptBlockText|contains: 'Invoke-ShareFinder'
23 condition: selection
24falsepositives:
25 - Unknown
26level: High
References
Related rules
- Invoke-ShareFinder Discovery Activity
- NetScan Share Enumeration Write Access Check
- AdFind Discovery
- List remote processes using tasklist
- Registry Query for WDigest