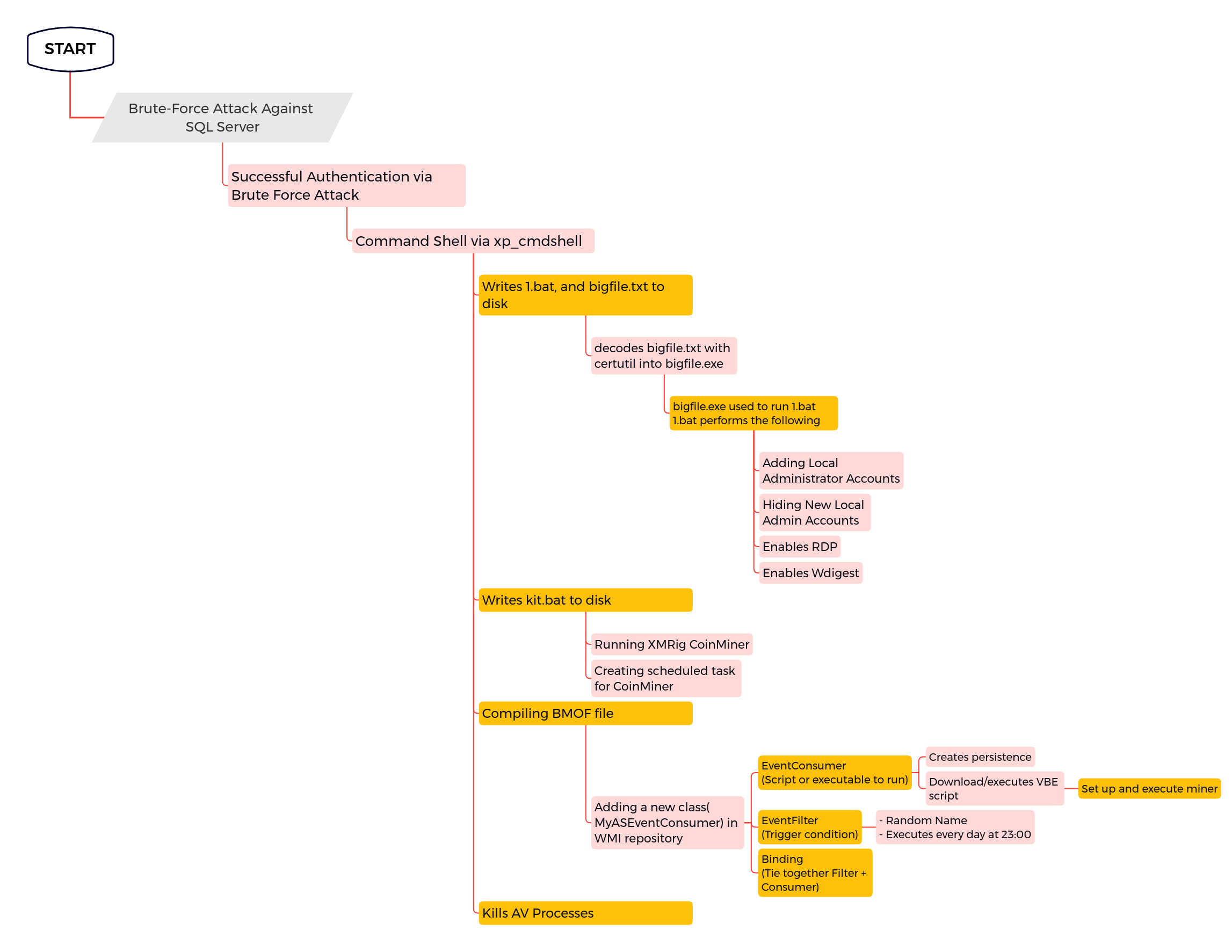
Hiding User Account Via SpecialAccounts Registry Key
Detects modifications to the registry key "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\Userlist" where the value is set to "0" in order to hide user account from being listed on the logon screen.
Sigma rule (View on GitHub)
1title: Hiding User Account Via SpecialAccounts Registry Key
2id: f8aebc67-a56d-4ec9-9fbe-7b0e8b7b4efd
3related:
4 - id: 8a58209c-7ae6-4027-afb0-307a78e4589a
5 type: obsolete
6 - id: 9ec9fb1b-e059-4489-9642-f270c207923d
7 type: similar
8status: test
9description: Detects modifications to the registry key "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\Userlist" where the value is set to "0" in order to hide user account from being listed on the logon screen.
10references:
11 - https://thedfirreport.com/2022/07/11/select-xmrig-from-sqlserver/
12 - https://github.com/redcanaryco/atomic-red-team/blob/40b77d63808dd4f4eafb83949805636735a1fd15/atomics/T1564.002/T1564.002.md#atomic-test-3---create-hidden-user-in-registry
13author: Nasreddine Bencherchali (Nextron Systems), frack113
14date: 2022-07-12
15modified: 2023-01-26
16tags:
17 - attack.defense-evasion
18 - attack.t1564.002
19logsource:
20 category: registry_set
21 product: windows
22detection:
23 selection:
24 TargetObject|contains: '\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\UserList'
25 Details: 'DWORD (0x00000000)'
26 condition: selection
27falsepositives:
28 - Unknown
29level: high
30regression_tests_path: regression_data/rules/windows/registry/registry_set/registry_set_special_accounts/info.yml
31simulation:
32 - type: atomic-red-team
33 name: Create Hidden User in Registry
34 technique: T1564.002
35 atomic_guid: 173126b7-afe4-45eb-8680-fa9f6400431c
References
Related rules
- Hiding User Account Via SpecialAccounts Registry Key - CommandLine
- Potential Suspicious Activity Using SeCEdit
- Hidden User Creation
- Add SafeBoot Keys Via Reg Utility
- Allow RDP Remote Assistance Feature