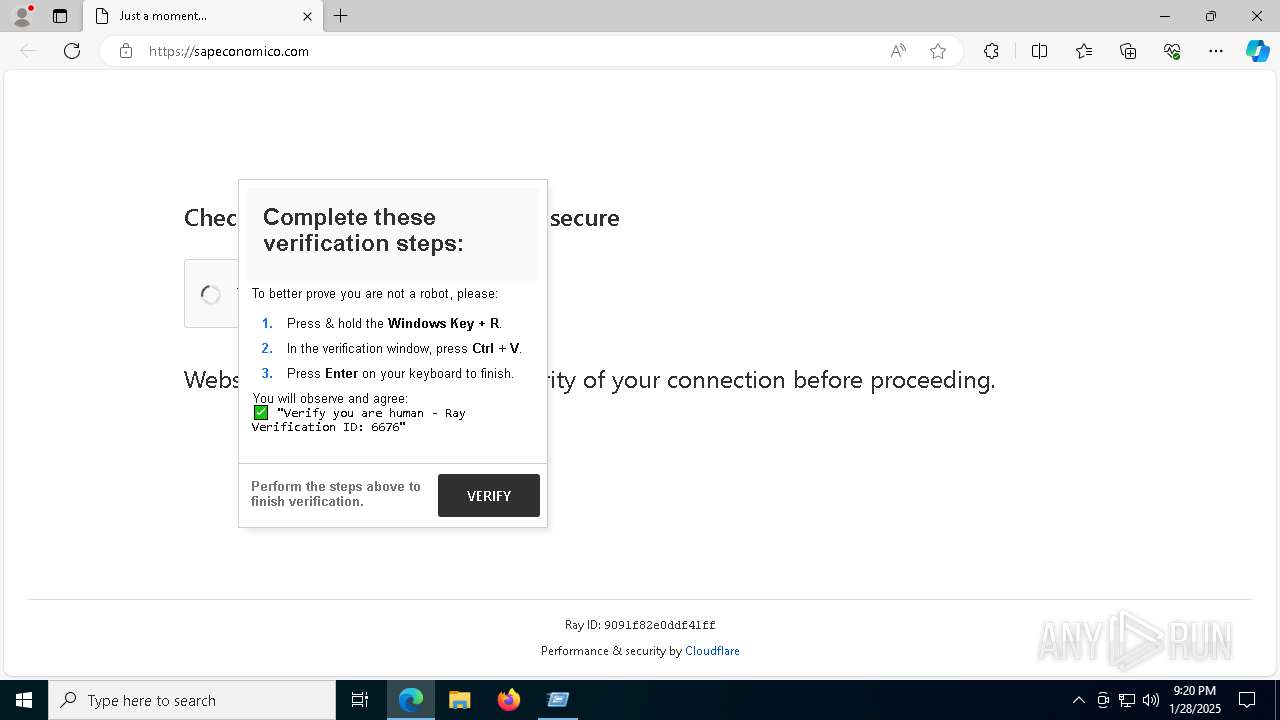
Potential ClickFix Execution Pattern - Registry
Detects potential ClickFix malware execution patterns by monitoring registry modifications in RunMRU keys containing HTTP/HTTPS links. ClickFix is known to be distributed through phishing campaigns and uses techniques like clipboard hijacking and fake CAPTCHA pages. Through the fakecaptcha pages, the adversary tricks users into opening the Run dialog box and pasting clipboard-hijacked content, such as one-liners that execute remotely hosted malicious files or scripts.
Sigma rule (View on GitHub)
1title: Potential ClickFix Execution Pattern - Registry
2id: f5fe36cf-f1ec-4c23-903d-09a3110f6bbb
3related:
4 - id: d487ed4a-fd24-436d-a0b2-f4e95f7b2635
5 type: similar
6status: experimental
7description: |
8 Detects potential ClickFix malware execution patterns by monitoring registry modifications in RunMRU keys containing HTTP/HTTPS links.
9 ClickFix is known to be distributed through phishing campaigns and uses techniques like clipboard hijacking and fake CAPTCHA pages.
10 Through the fakecaptcha pages, the adversary tricks users into opening the Run dialog box and pasting clipboard-hijacked content,
11 such as one-liners that execute remotely hosted malicious files or scripts.
12references:
13 - https://github.com/JohnHammond/recaptcha-phish
14 - https://www.zscaler.com/blogs/security-research/deepseek-lure-using-captchas-spread-malware
15 - https://www.threatdown.com/blog/clipboard-hijacker-tries-to-install-a-trojan/
16 - https://app.any.run/tasks/5c16b4db-4b36-4039-a0ed-9b09abff8be2
17 - https://www.esentire.com/security-advisories/netsupport-rat-clickfix-distribution
18 - https://medium.com/@boutnaru/the-windows-foreniscs-journey-run-mru-run-dialog-box-most-recently-used-57375a02d724
19 - https://unit42.paloaltonetworks.com/preventing-clickfix-attack-vector/
20 - https://medium.com/@poudelswachchhanda123/preventing-lnk-and-fakecaptcha-threats-a-system-hardening-approach-2f7b7ed2e493
21 - https://www.scpx.com.au/2025/11/16/decades-old-finger-protocol-abused-in-clickfix-malware-attacks/
22author: Swachchhanda Shrawan Poudel (Nextron Systems)
23date: 2025-03-25
24modified: 2025-11-19
25tags:
26 - attack.execution
27 - attack.t1204.001
28logsource:
29 category: registry_set
30 product: windows
31detection:
32 selection_registry:
33 TargetObject|contains: '\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\RunMRU\'
34 selection_details:
35 Details|contains:
36 - 'http://'
37 - 'https://'
38 selection_susp_pattern:
39 - Details|contains:
40 # Add more suspicious keywords
41 - 'account'
42 - 'anti-bot'
43 - 'botcheck'
44 - 'captcha'
45 - 'challenge'
46 - 'confirmation'
47 - 'fraud'
48 - 'human'
49 - 'identification'
50 - 'identificator'
51 - 'identity'
52 - 'robot'
53 - 'validation'
54 - 'verification'
55 - 'verify'
56 - Details|contains:
57 - '%comspec%'
58 - 'bitsadmin'
59 - 'certutil'
60 - 'cmd'
61 - 'cscript'
62 - 'curl'
63 - 'finger'
64 - 'mshta'
65 - 'powershell'
66 - 'pwsh'
67 - 'regsvr32'
68 - 'rundll32'
69 - 'schtasks'
70 - 'wget'
71 - 'wscript'
72 condition: all of selection_*
73falsepositives:
74 - Legitimate applications using RunMRU with HTTP links
75level: high
References
Related rules
- Suspicious ClickFix/FileFix Execution Pattern
- Suspicious Execution via macOS Script Editor
- Symlink Etc Passwd
- DNS Query by Finger Utility
- FileFix - Command Evidence in TypedPaths