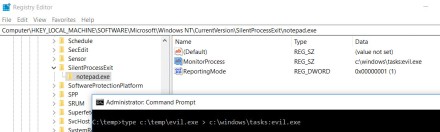
Potential Persistence Via GlobalFlags
Detects registry persistence technique using the GlobalFlags and SilentProcessExit keys
Sigma rule (View on GitHub)
1title: Potential Persistence Via GlobalFlags
2id: 36803969-5421-41ec-b92f-8500f79c23b0
3related:
4 - id: c81fe886-cac0-4913-a511-2822d72ff505
5 type: obsoletes
6status: test
7description: Detects registry persistence technique using the GlobalFlags and SilentProcessExit keys
8references:
9 - https://oddvar.moe/2018/04/10/persistence-using-globalflags-in-image-file-execution-options-hidden-from-autoruns-exe/
10 - https://www.deepinstinct.com/2021/02/16/lsass-memory-dumps-are-stealthier-than-ever-before-part-2/
11author: Karneades, Jonhnathan Ribeiro, Florian Roth
12date: 2018/04/11
13modified: 2023/06/05
14tags:
15 - attack.privilege_escalation
16 - attack.persistence
17 - attack.defense_evasion
18 - attack.t1546.012
19 - car.2013-01-002
20logsource:
21 category: registry_set
22 product: windows
23detection:
24 selection_global_flag:
25 TargetObject|contains|all:
26 - '\Microsoft\Windows NT\CurrentVersion\'
27 - '\Image File Execution Options\'
28 - '\GlobalFlag'
29 selection_silent_process:
30 TargetObject|contains|all:
31 - '\Microsoft\Windows NT\CurrentVersion\'
32 - '\SilentProcessExit\'
33 TargetObject|contains:
34 - '\ReportingMode'
35 - '\MonitorProcess'
36 condition: 1 of selection_*
37falsepositives:
38 - Unknown
39level: high
References
Related rules
- Powerup Write Hijack DLL
- Possible Privilege Escalation via Weak Service Permissions
- UAC Bypass With Fake DLL
- Potential Persistence Via PowerShell User Profile Using Add-Content
- Remote WMI ActiveScriptEventConsumers