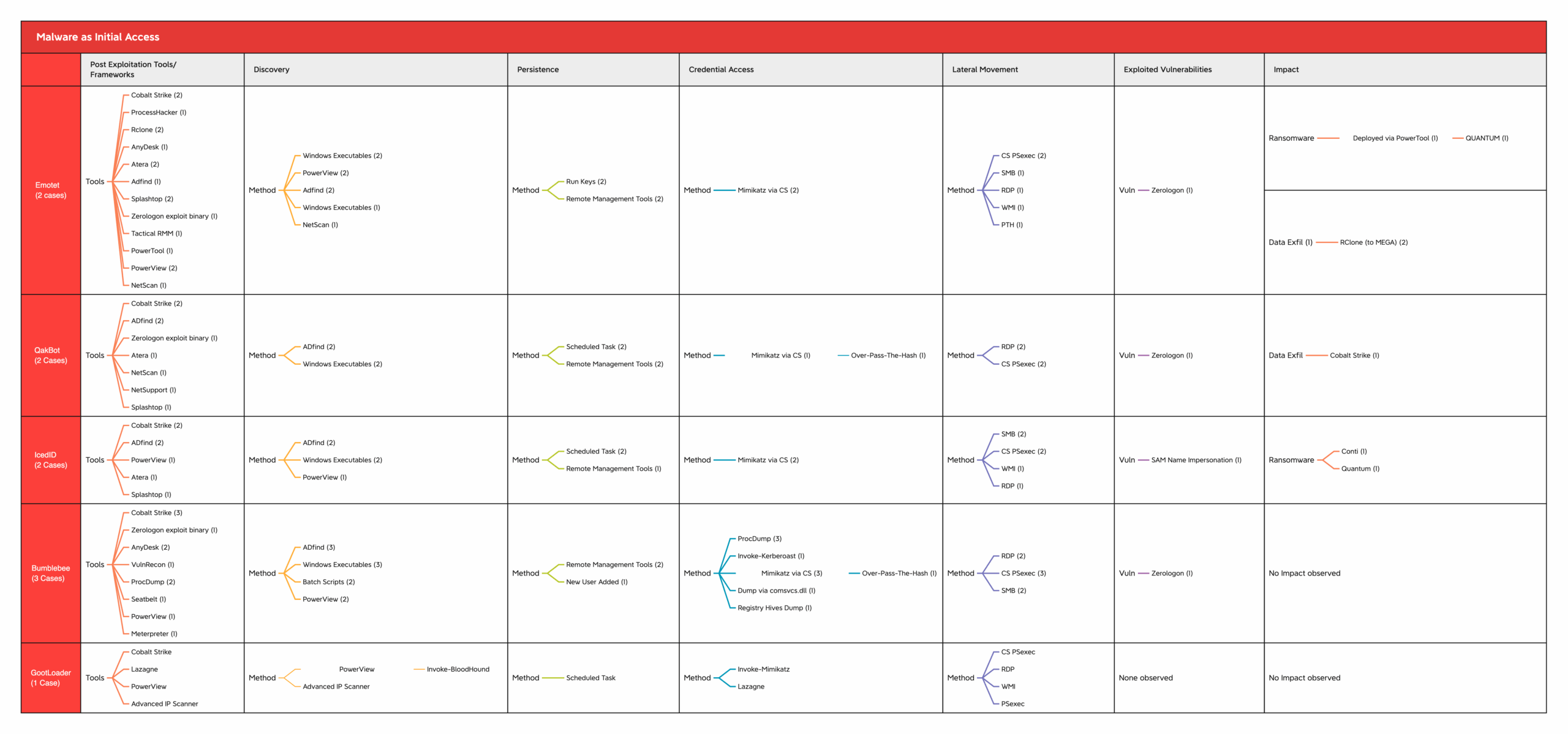
Potential Product Reconnaissance Via Wmic.EXE
Detects the execution of WMIC in order to get a list of firewall and antivirus products
Sigma rule (View on GitHub)
1title: Potential Product Reconnaissance Via Wmic.EXE
2id: 15434e33-5027-4914-88d5-3d4145ec25a9
3status: test
4description: Detects the execution of WMIC in order to get a list of firewall and antivirus products
5references:
6 - https://thedfirreport.com/2023/03/06/2022-year-in-review/
7 - https://www.yeahhub.com/list-installed-programs-version-path-windows/
8 - https://learn.microsoft.com/en-us/answers/questions/253555/software-list-inventory-wmic-product
9author: Nasreddine Bencherchali
10date: 2023-02-14
11modified: 2025-10-22
12tags:
13 - attack.execution
14 - attack.t1047
15logsource:
16 category: process_creation
17 product: windows
18detection:
19 selection_img:
20 - Image|endswith: '\wmic.exe'
21 - OriginalFileName: 'wmic.exe'
22 selection_cli:
23 CommandLine|contains: 'Product'
24 filter_main_call_operations:
25 # wmic /node:"#{node}" product where "name like '#{product}%%'" call uninstall
26 CommandLine|contains:
27 - ' uninstall'
28 - ' install'
29 condition: all of selection_* and not 1 of filter_main_*
30falsepositives:
31 - Unknown
32level: medium
References
Related rules
- WMIC Remote Command Execution
- Blue Mockingbird - Registry
- Blue Mockingbird
- HackTool - CrackMapExec Execution Patterns
- MITRE BZAR Indicators for Execution