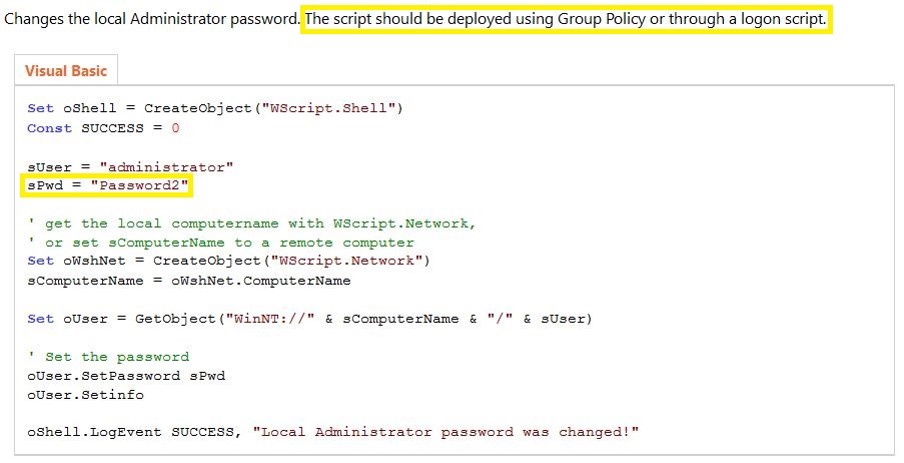
Suspicious SYSVOL Domain Group Policy Access
Detects Access to Domain Group Policies stored in SYSVOL
Sigma rule (View on GitHub)
1title: Suspicious SYSVOL Domain Group Policy Access
2id: 05f3c945-dcc8-4393-9f3d-af65077a8f86
3status: test
4description: Detects Access to Domain Group Policies stored in SYSVOL
5references:
6 - https://adsecurity.org/?p=2288
7 - https://www.hybrid-analysis.com/sample/f2943f5e45befa52fb12748ca7171d30096e1d4fc3c365561497c618341299d5?environmentId=100
8author: Markus Neis, Jonhnathan Ribeiro, oscd.community
9date: 2018/04/09
10modified: 2022/01/07
11tags:
12 - attack.credential_access
13 - attack.t1552.006
14logsource:
15 category: process_creation
16 product: windows
17detection:
18 selection:
19 CommandLine|contains|all:
20 - '\SYSVOL\'
21 - '\policies\'
22 condition: selection
23falsepositives:
24 - Administrative activity
25level: medium
References
Related rules
- Dumping Process via Sqldumper.exe
- Invocation of Active Directory Diagnostic Tool (ntdsutil.exe)
- WCE wceaux.dll Access
- Credentials In Files
- Kerberos Network Traffic RC4 Ticket Encryption