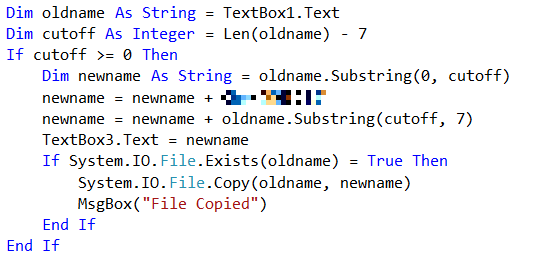
Potential Defense Evasion Via Right-to-Left Override
Detects the presence of the "u202+E" character, which causes a terminal, browser, or operating system to render text in a right-to-left sequence. This is used as an obfuscation and masquerading techniques.
Sigma rule (View on GitHub)
1title: Potential Defense Evasion Via Right-to-Left Override
2id: ad691d92-15f2-4181-9aa4-723c74f9ddc3
3related:
4 - id: e0552b19-5a83-4222-b141-b36184bb8d79
5 type: derived
6 - id: 584bca0f-3608-4402-80fd-4075ff6072e3
7 type: derived
8status: test
9description: |
10 Detects the presence of the "u202+E" character, which causes a terminal, browser, or operating system to render text in a right-to-left sequence.
11 This is used as an obfuscation and masquerading techniques.
12references:
13 - https://redcanary.com/blog/right-to-left-override/
14 - https://www.malwarebytes.com/blog/news/2014/01/the-rtlo-method
15 - https://unicode-explorer.com/c/202E
16 - https://tria.ge/241015-l98snsyeje/behavioral2
17author: Micah Babinski, @micahbabinski, Swachchhanda Shrawan Poudel (Nextron Systems)
18date: 2023-02-15
19modified: 2025-02-06
20tags:
21 - attack.defense-evasion
22 - attack.t1036.002
23logsource:
24 category: process_creation
25 product: windows
26detection:
27 selection:
28 CommandLine|contains:
29 - '\u202e' # Unicode RTLO character
30 - '[U+202E]'
31 condition: selection
32falsepositives:
33 - Commandlines that contains scriptures such as arabic or hebrew might make use of this character
34level: high
References
Related rules
- MMC Executing Files with Reversed Extensions Using RTLO Abuse
- Potential File Extension Spoofing Using Right-to-Left Override
- MMC Loading Script Engines DLLs
- Potentially Suspicious Child Processes Spawned by ConHost
- Uncommon Child Process Of Conhost.EXE