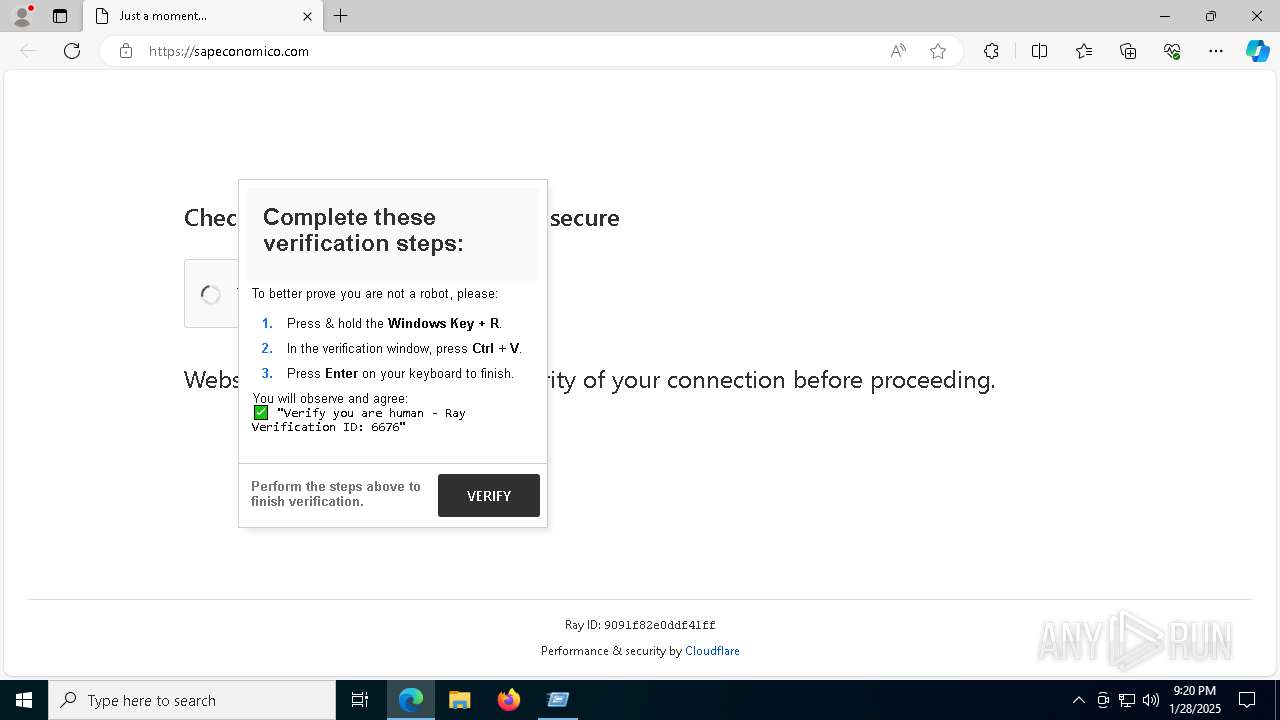
Suspicious ClickFix/FileFix Execution Pattern
Detects suspicious execution patterns where users are tricked into running malicious commands via clipboard manipulation, either through the Windows Run dialog (ClickFix) or File Explorer address bar (FileFix). Attackers leverage social engineering campaigns—such as fake CAPTCHA challenges or urgent alerts—encouraging victims to paste clipboard contents, often executing mshta.exe, powershell.exe, or similar commands to infect systems.
Sigma rule (View on GitHub)
1title: Suspicious ClickFix/FileFix Execution Pattern
2id: d487ed4a-fd24-436d-a0b2-f4e95f7b2635
3related:
4 - id: f5fe36cf-f1ec-4c23-903d-09a3110f6bbb
5 type: similar
6status: experimental
7description: |
8 Detects suspicious execution patterns where users are tricked into running malicious commands via clipboard manipulation, either through the Windows Run dialog (ClickFix) or File Explorer address bar (FileFix).
9 Attackers leverage social engineering campaigns—such as fake CAPTCHA challenges or urgent alerts—encouraging victims to paste clipboard contents, often executing mshta.exe, powershell.exe, or similar commands to infect systems.
10references:
11 - https://github.com/JohnHammond/recaptcha-phish
12 - https://www.zscaler.com/blogs/security-research/deepseek-lure-using-captchas-spread-malware
13 - https://www.threatdown.com/blog/clipboard-hijacker-tries-to-install-a-trojan/
14 - https://app.any.run/tasks/5c16b4db-4b36-4039-a0ed-9b09abff8be2
15 - https://www.esentire.com/security-advisories/netsupport-rat-clickfix-distribution
16 - https://www.scpx.com.au/2025/11/16/decades-old-finger-protocol-abused-in-clickfix-malware-attacks/ # filefix variant
17author: montysecurity, Swachchhanda Shrawan Poudel (Nextron Systems)
18date: 2025-11-19
19tags:
20 - attack.execution
21 - attack.t1204.001
22 - attack.t1204.004
23logsource:
24 category: process_creation
25 product: windows
26detection:
27 selection_parent:
28 ParentImage|endswith: '\explorer.exe'
29 CommandLine|contains: '#'
30 selection_cli_captcha:
31 CommandLine|contains:
32 - 'account'
33 - 'anti-bot'
34 - 'botcheck'
35 - 'captcha'
36 - 'challenge'
37 - 'confirmation'
38 - 'fraud'
39 - 'human'
40 - 'identification'
41 - 'identificator'
42 - 'identity'
43 - 'robot'
44 - 'validation'
45 - 'verification'
46 - 'verify'
47 condition: all of selection_*
48falsepositives:
49 - Unlikely
50level: high
References
Related rules
- Suspicious Space Characters in RunMRU Registry Path - ClickFix
- Suspicious Space Characters in TypedPaths Registry Path - FileFix
- Suspicious Execution via macOS Script Editor
- Symlink Etc Passwd
- Suspicious Usage of For Loop with Recursive Directory Search in CMD