Suspicious Scheduled Task Name As GUID
Detects creation of a scheduled task with a GUID like name
Sigma rule (View on GitHub)
1title: Suspicious Scheduled Task Name As GUID
2id: ff2fff64-4cd6-4a2b-ba7d-e28a30bbe66b
3status: test
4description: Detects creation of a scheduled task with a GUID like name
5references:
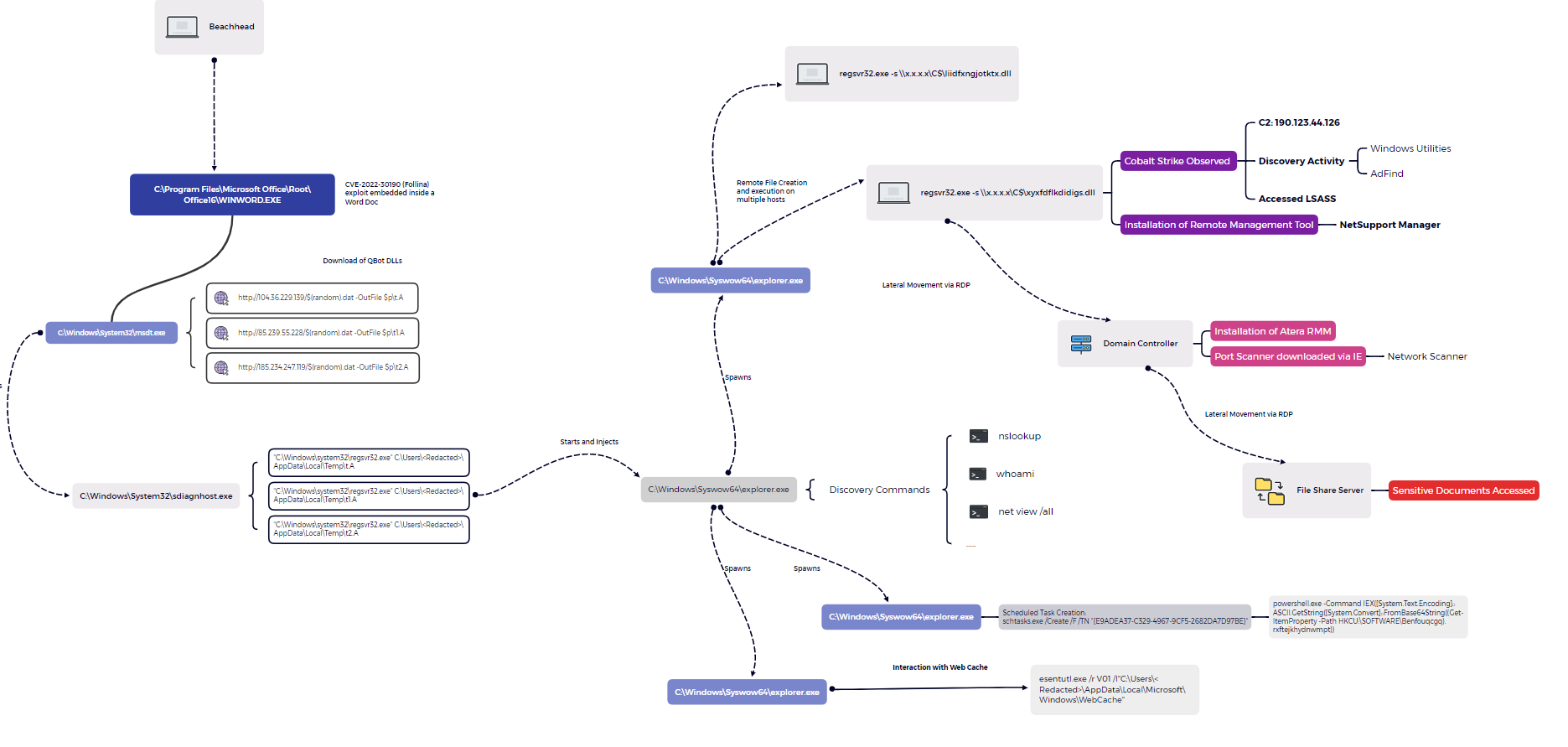
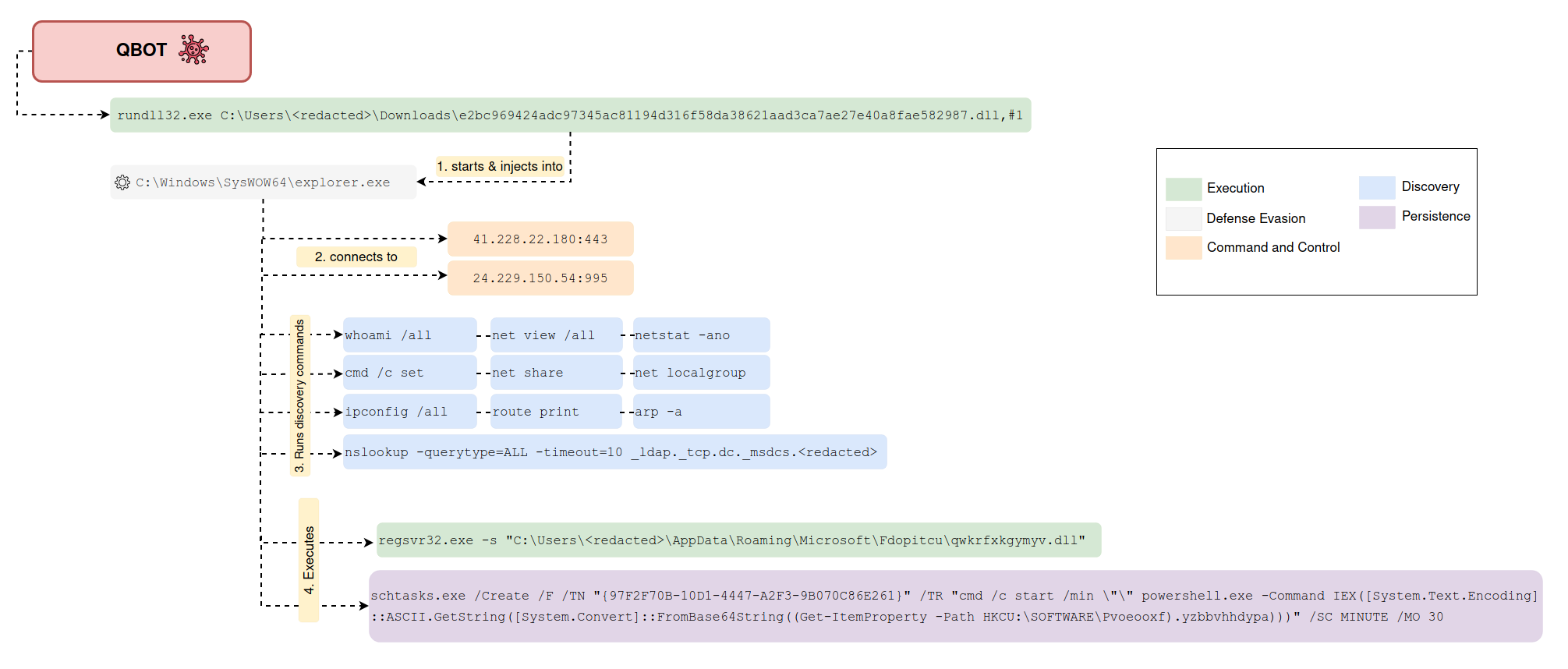
6 - https://thedfirreport.com/2022/10/31/follina-exploit-leads-to-domain-compromise/
7 - https://thedfirreport.com/2022/02/21/qbot-and-zerologon-lead-to-full-domain-compromise/
8author: Nasreddine Bencherchali (Nextron Systems)
9date: 2022-10-31
10tags:
11 - attack.privilege-escalation
12 - attack.persistence
13 - attack.execution
14 - attack.t1053.005
15logsource:
16 product: windows
17 category: process_creation
18detection:
19 selection_img:
20 Image|endswith: '\schtasks.exe'
21 CommandLine|contains: '/Create '
22 selection_tn:
23 CommandLine|contains:
24 # Can start with single or double quote
25 - '/TN "{'
26 - "/TN '{"
27 - "/TN {"
28 selection_end:
29 CommandLine|contains:
30 # Ending of the name to avoid possible FP in the rest of the commandline
31 - '}"'
32 - "}'"
33 - '} '
34 condition: all of selection_*
35falsepositives:
36 - Legitimate software naming their tasks as GUIDs
37level: medium
References
Related rules
- ChromeLoader Malware Execution
- Defrag Deactivation
- Kapeka Backdoor Persistence Activity
- OilRig APT Activity
- OilRig APT Registry Persistence