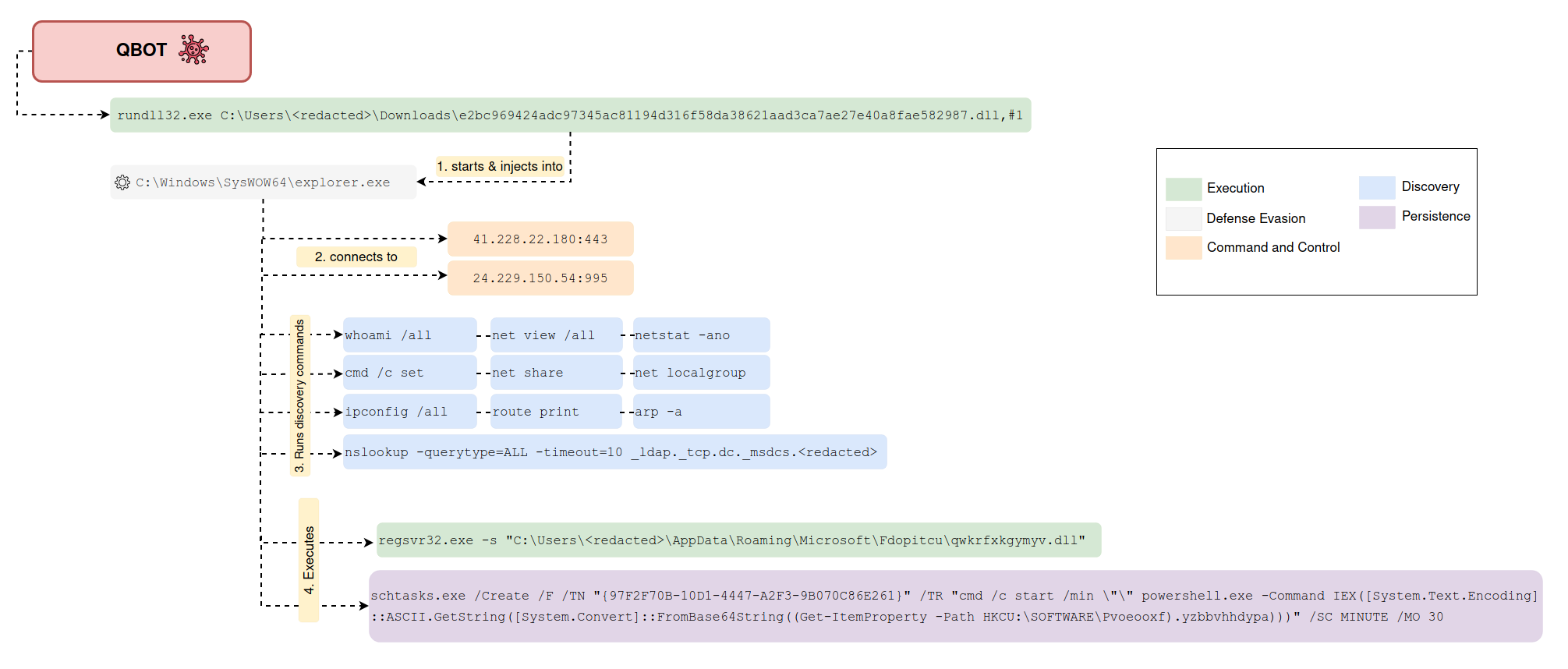
Suspicious Schtasks Execution AppData Folder
Detects the creation of a schtask that executes a file from C:\Users<USER>\AppData\Local
Sigma rule (View on GitHub)
1title: Suspicious Schtasks Execution AppData Folder
2id: c5c00f49-b3f9-45a6-997e-cfdecc6e1967
3status: test
4description: 'Detects the creation of a schtask that executes a file from C:\Users\<USER>\AppData\Local'
5references:
6 - https://thedfirreport.com/2022/02/21/qbot-and-zerologon-lead-to-full-domain-compromise/
7author: pH-T (Nextron Systems), Nasreddine Bencherchali (Nextron Systems)
8date: 2022-03-15
9modified: 2022-07-28
10tags:
11 - attack.privilege-escalation
12 - attack.execution
13 - attack.persistence
14 - attack.t1053.005
15 - attack.t1059.001
16logsource:
17 product: windows
18 category: process_creation
19detection:
20 selection:
21 Image|endswith: '\schtasks.exe'
22 CommandLine|contains|all:
23 - '/Create'
24 - '/RU'
25 - '/TR'
26 - 'C:\Users\'
27 - '\AppData\Local\'
28 CommandLine|contains:
29 - 'NT AUT' # This covers the usual NT AUTHORITY\SYSTEM
30 - ' SYSTEM ' # SYSTEM is a valid value for schtasks hence it gets it's own value with space
31 filter:
32 # FP from test set in SIGMA
33 ParentImage|contains|all:
34 - '\AppData\Local\Temp\'
35 - 'TeamViewer_.exe'
36 Image|endswith: '\schtasks.exe'
37 CommandLine|contains: '/TN TVInstallRestore'
38 condition: selection and not filter
39falsepositives:
40 - Unknown
41level: high
References
Related rules
- ChromeLoader Malware Execution
- Operation Wocao Activity
- Operation Wocao Activity - Security
- Potential Persistence Via Powershell Search Order Hijacking - Task
- Scheduled Task Executing Encoded Payload from Registry