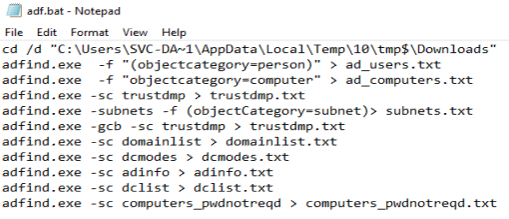
Renamed AdFind Execution
Detects the use of a renamed Adfind.exe. AdFind continues to be seen across majority of breaches. It is used to domain trust discovery to plan out subsequent steps in the attack chain.
Sigma rule (View on GitHub)
1title: Renamed AdFind Execution
2id: df55196f-f105-44d3-a675-e9dfb6cc2f2b
3status: test
4description: Detects the use of a renamed Adfind.exe. AdFind continues to be seen across majority of breaches. It is used to domain trust discovery to plan out subsequent steps in the attack chain.
5references:
6 - https://www.joeware.net/freetools/tools/adfind/
7 - https://thedfirreport.com/2020/05/08/adfind-recon/
8 - https://thedfirreport.com/2021/01/11/trickbot-still-alive-and-well/
9 - https://www.microsoft.com/security/blog/2021/01/20/deep-dive-into-the-solorigate-second-stage-activation-from-sunburst-to-teardrop-and-raindrop/
10 - https://social.technet.microsoft.com/wiki/contents/articles/7535.adfind-command-examples.aspx
11 - https://github.com/center-for-threat-informed-defense/adversary_emulation_library/blob/bf62ece1c679b07b5fb49c4bae947fe24c81811f/fin6/Emulation_Plan/Phase1.md
12author: Florian Roth (Nextron Systems)
13date: 2022-08-21
14modified: 2025-02-26
15tags:
16 - attack.discovery
17 - attack.t1018
18 - attack.t1087.002
19 - attack.t1482
20 - attack.t1069.002
21logsource:
22 category: process_creation
23 product: windows
24detection:
25 selection_1:
26 CommandLine|contains:
27 - 'domainlist'
28 - 'trustdmp'
29 - 'dcmodes'
30 - 'adinfo'
31 - ' dclist '
32 - 'computer_pwdnotreqd'
33 - 'objectcategory='
34 - '-subnets -f'
35 - 'name="Domain Admins"'
36 - '-sc u:'
37 - 'domainncs'
38 - 'dompol'
39 - ' oudmp '
40 - 'subnetdmp'
41 - 'gpodmp'
42 - 'fspdmp'
43 - 'users_noexpire'
44 - 'computers_active'
45 - 'computers_pwdnotreqd'
46 selection_2:
47 Hashes|contains:
48 - 'IMPHASH=BCA5675746D13A1F246E2DA3C2217492'
49 - 'IMPHASH=53E117A96057EAF19C41380D0E87F1C2'
50 - 'IMPHASH=d144de8117df2beceaba2201ad304764'
51 - 'IMPHASH=12ce1c0f3f5837ecc18a3782408fa975'
52 - 'IMPHASH=4fbf3f084fbbb2470b80b2013134df35'
53 - 'IMPHASH=49b639b4acbecc49d72a01f357aa4930'
54 - 'IMPHASH=680dad9e300346e05a85023965867201'
55 - 'IMPHASH=21aa085d54992511b9f115355e468782'
56 selection_3:
57 OriginalFileName: 'AdFind.exe'
58 filter:
59 Image|endswith: '\AdFind.exe'
60 condition: 1 of selection* and not filter
61falsepositives:
62 - Unknown
63level: high
64regression_tests_path: regression_data/rules/windows/process_creation/proc_creation_win_renamed_adfind/info.yml
References
Related rules
- PUA - AdFind Suspicious Execution
- ADExplorer Writing Complete AD Snapshot Into .dat File
- Active Directory Database Snapshot Via ADExplorer
- Suspicious Active Directory Database Snapshot Via ADExplorer
- Potential Active Directory Reconnaissance/Enumeration Via LDAP