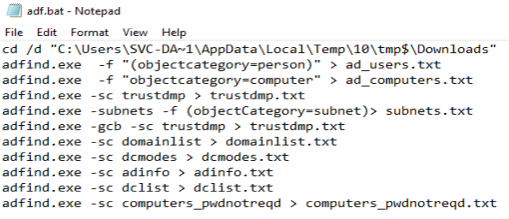
PUA - AdFind Suspicious Execution
Detects AdFind execution with common flags seen used during attacks
Sigma rule (View on GitHub)
1title: PUA - AdFind Suspicious Execution
2id: 9a132afa-654e-11eb-ae93-0242ac130002
3related:
4 - id: 455b9d50-15a1-4b99-853f-8d37655a4c1b
5 type: similar
6 - id: 75df3b17-8bcc-4565-b89b-c9898acef911
7 type: obsolete
8status: test
9description: Detects AdFind execution with common flags seen used during attacks
10references:
11 - https://www.joeware.net/freetools/tools/adfind/
12 - https://thedfirreport.com/2020/05/08/adfind-recon/
13 - https://thedfirreport.com/2021/01/11/trickbot-still-alive-and-well/
14 - https://www.microsoft.com/security/blog/2021/01/20/deep-dive-into-the-solorigate-second-stage-activation-from-sunburst-to-teardrop-and-raindrop/
15 - https://social.technet.microsoft.com/wiki/contents/articles/7535.adfind-command-examples.aspx
16 - https://github.com/center-for-threat-informed-defense/adversary_emulation_library/blob/bf62ece1c679b07b5fb49c4bae947fe24c81811f/fin6/Emulation_Plan/Phase1.md
17 - https://github.com/redcanaryco/atomic-red-team/blob/0f229c0e42bfe7ca736a14023836d65baa941ed2/atomics/T1087.002/T1087.002.md#atomic-test-7---adfind---enumerate-active-directory-user-objects
18author: Janantha Marasinghe (https://github.com/blueteam0ps), FPT.EagleEye Team, omkar72, oscd.community
19date: 2021-02-02
20modified: 2023-03-05
21tags:
22 - attack.discovery
23 - attack.t1018
24 - attack.t1087.002
25 - attack.t1482
26 - attack.t1069.002
27 - stp.1u
28logsource:
29 category: process_creation
30 product: windows
31detection:
32 selection:
33 CommandLine|contains:
34 - 'domainlist'
35 - 'trustdmp'
36 - 'dcmodes'
37 - 'adinfo'
38 - ' dclist '
39 - 'computer_pwdnotreqd'
40 - 'objectcategory='
41 - '-subnets -f'
42 - 'name="Domain Admins"'
43 - '-sc u:'
44 - 'domainncs'
45 - 'dompol'
46 - ' oudmp '
47 - 'subnetdmp'
48 - 'gpodmp'
49 - 'fspdmp'
50 - 'users_noexpire'
51 - 'computers_active'
52 - 'computers_pwdnotreqd'
53 condition: selection
54falsepositives:
55 - Legitimate admin activity
56level: high
References
Related rules
- Renamed AdFind Execution
- AdFind Discovery
- BloodHound Collection Files
- HackTool - Bloodhound/Sharphound Execution
- Malicious PowerShell Commandlets - PoshModule