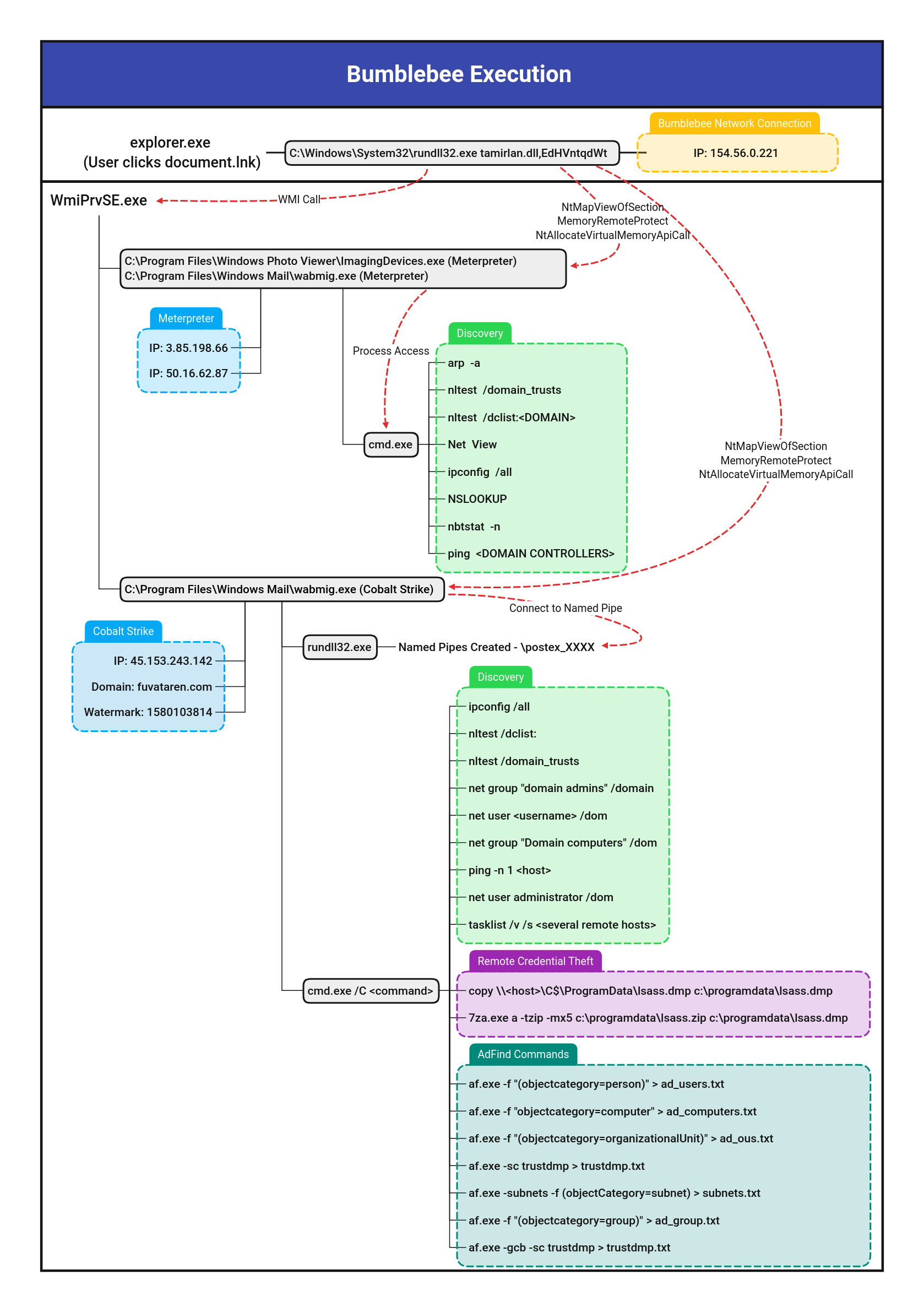
ImagingDevices Unusual Parent/Child Processes
Detects unusual parent or children of the ImagingDevices.exe (Windows Contacts) process as seen being used with Bumblebee activity
Sigma rule (View on GitHub)
1title: ImagingDevices Unusual Parent/Child Processes
2id: f11f2808-adb4-46c0-802a-8660db50fa99
3status: test
4description: Detects unusual parent or children of the ImagingDevices.exe (Windows Contacts) process as seen being used with Bumblebee activity
5references:
6 - https://thedfirreport.com/2022/09/26/bumblebee-round-two/
7author: Nasreddine Bencherchali (Nextron Systems)
8date: 2022/09/27
9modified: 2022/12/29
10tags:
11 - attack.defense_evasion
12 - attack.execution
13logsource:
14 category: process_creation
15 product: windows
16detection:
17 selection_parent:
18 ParentImage|endswith:
19 # Add more if known
20 - \WmiPrvSE.exe
21 - \svchost.exe
22 - \dllhost.exe
23 Image|endswith: '\ImagingDevices.exe'
24 selection_child:
25 # You can add specific suspicious child processes (such as cmd, powershell...) to increase the accuracy
26 ParentImage|endswith: '\ImagingDevices.exe'
27 condition: 1 of selection_*
28falsepositives:
29 - Unknown
30level: high
References
Related rules
- Invoke-Obfuscation Obfuscated IEX Invocation - PowerShell
- Invoke-Obfuscation Obfuscated IEX Invocation - PowerShell Module
- Invoke-Obfuscation Via Use MSHTA - PowerShell Module
- Lolbin Defaultpack.exe Use As Proxy
- Suspicious Execution via macOS Script Editor