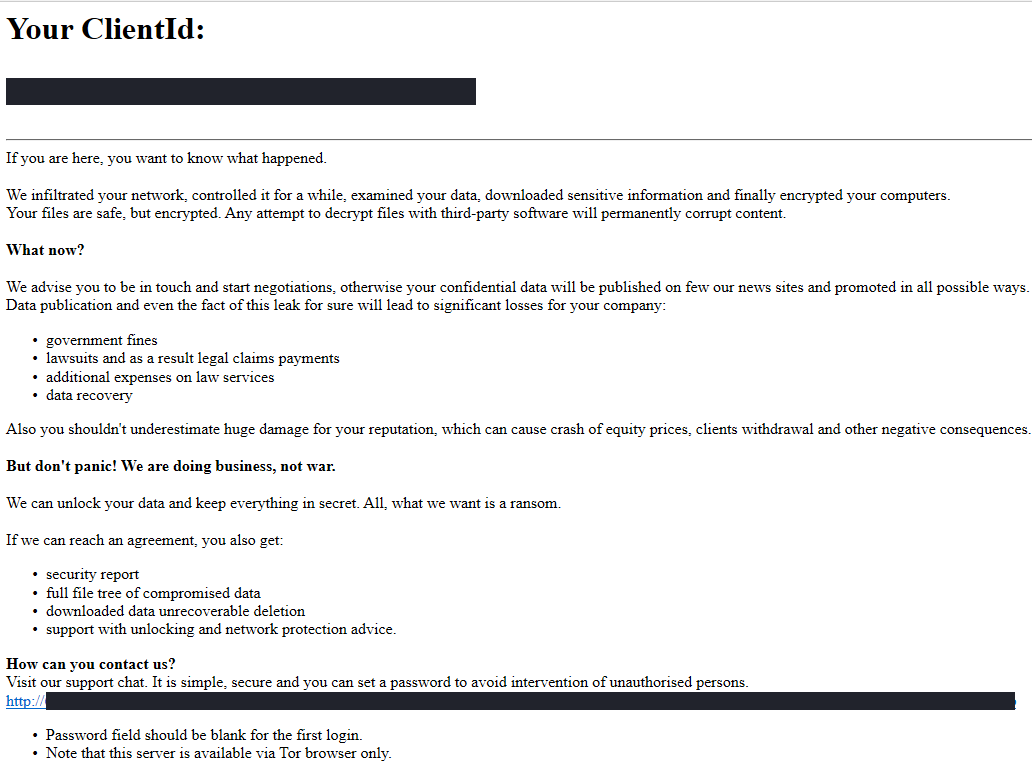
Windows Defender Context Menu Removed
Detects the use of reg.exe or PowerShell to delete the Windows Defender context menu handler registry keys. This action removes the "Scan with Microsoft Defender" option from the right-click menu for files, directories, and drives. Attackers may use this technique to hinder manual, on-demand scans and reduce the visibility of the security product.
Sigma rule (View on GitHub)
1title: Windows Defender Context Menu Removed
2id: b9e8c7d6-a5f4-4e3d-8b1a-9f0c8d7e6a5b
3related:
4 - id: 72a0369a-2576-4aaf-bfc9-6bb24a574ac6
5 type: similar
6status: experimental
7description: |
8 Detects the use of reg.exe or PowerShell to delete the Windows Defender context menu handler registry keys.
9 This action removes the "Scan with Microsoft Defender" option from the right-click menu for files, directories, and drives.
10 Attackers may use this technique to hinder manual, on-demand scans and reduce the visibility of the security product.
11references:
12 - https://research.splunk.com/endpoint/395ed5fe-ad13-4366-9405-a228427bdd91/
13 - https://winaero.com/how-to-delete-scan-with-windows-defender-from-context-menu-in-windows-10/
14 - https://thedfirreport.com/2021/10/18/icedid-to-xinglocker-ransomware-in-24-hours/
15 - https://blog.malwarebytes.com/malwarebytes-news/2021/02/lazyscripter-from-empire-to-double-rat/
16author: 'Matt Anderson (Huntress)'
17date: 2025-07-09
18tags:
19 - attack.defense-evasion
20 - attack.t1562.001
21logsource:
22 category: process_creation
23 product: windows
24detection:
25 selection_img:
26 - Image|endswith:
27 - '\powershell_ise.exe'
28 - '\powershell.exe'
29 - '\pwsh.exe'
30 - '\reg.exe'
31 - OriginalFileName:
32 - 'powershell_ise.EXE'
33 - 'PowerShell.EXE'
34 - 'pwsh.dll'
35 - 'reg.exe'
36 selection_action:
37 CommandLine|contains:
38 - 'del'
39 - 'Remove-Item'
40 - 'ri '
41 selection_reg_path:
42 CommandLine|contains: '\shellex\ContextMenuHandlers\EPP'
43 condition: all of selection_*
44falsepositives:
45 - May be part of a system customization or "debloating" script, but this is highly unusual in a managed corporate environment.
46level: high
References
Related rules
- Disabling Windows Defender WMI Autologger Session via Reg.exe
- PowerShell Defender Threat Severity Default Action Set to 'Allow' or 'NoAction'
- Windows Defender Threat Severity Default Action Modified
- Antivirus Filter Driver Disallowed On Dev Drive - Registry
- ESXi Syslog Configuration Change Via ESXCLI