Suspicious High IntegrityLevel Conhost Legacy Option
ForceV1 asks for information directly from the kernel space. Conhost connects to the console application. High IntegrityLevel means the process is running with elevated privileges, such as an Administrator context.
Sigma rule (View on GitHub)
1title: Suspicious High IntegrityLevel Conhost Legacy Option
2id: 3037d961-21e9-4732-b27a-637bcc7bf539
3status: test
4description: ForceV1 asks for information directly from the kernel space. Conhost connects to the console application. High IntegrityLevel means the process is running with elevated privileges, such as an Administrator context.
5references:
6 - https://cybercryptosec.medium.com/covid-19-cyber-infection-c615ead7c29
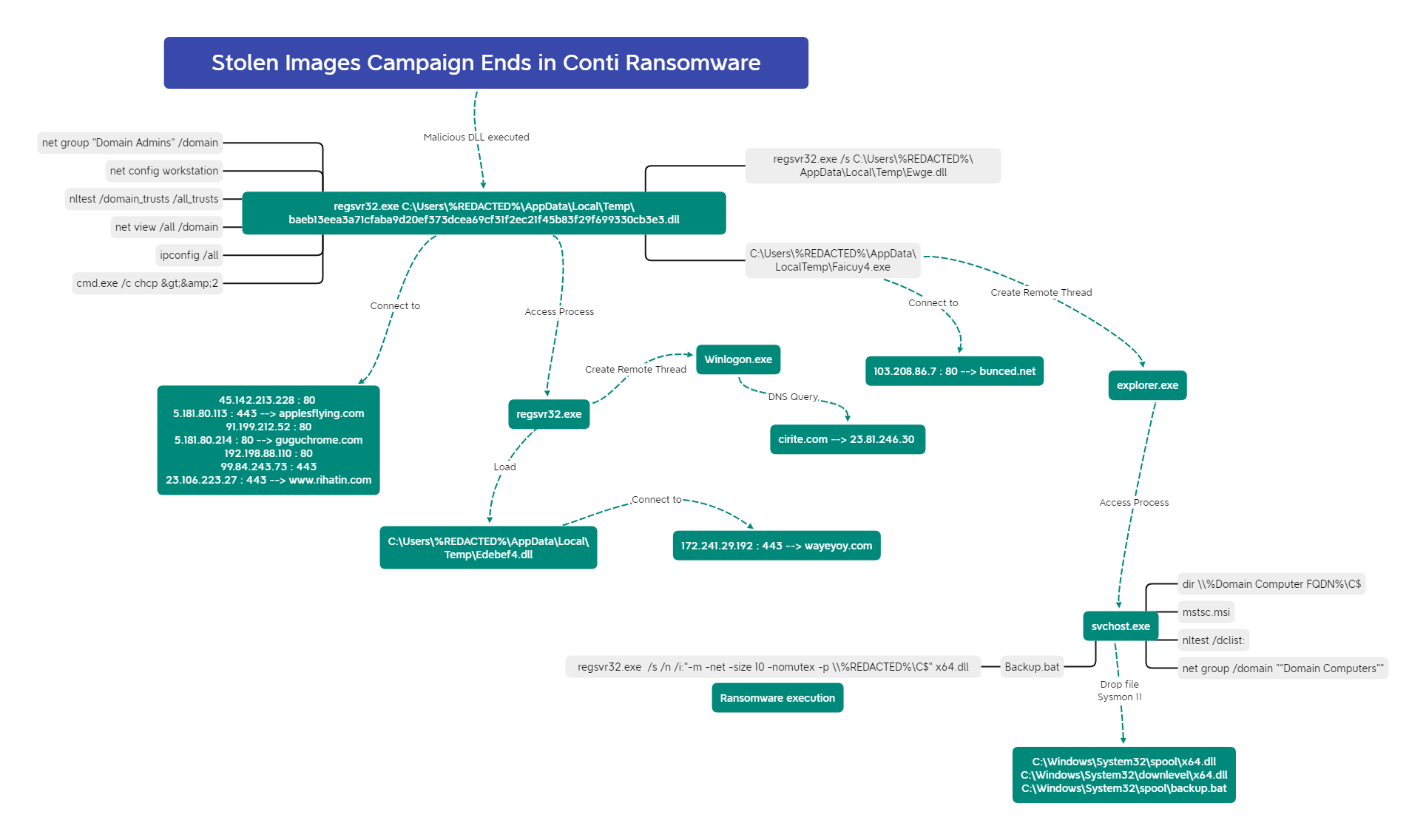
7 - https://thedfirreport.com/2022/04/04/stolen-images-campaign-ends-in-conti-ransomware/
8 - https://learn.microsoft.com/en-us/windows/win32/secauthz/mandatory-integrity-control
9author: frack113
10date: 2022/12/09
11tags:
12 - attack.defense_evasion
13 - attack.t1202
14logsource:
15 product: windows
16 category: process_creation
17detection:
18 selection:
19 IntegrityLevel: 'High'
20 CommandLine|contains|all:
21 - 'conhost.exe'
22 - '0xffffffff'
23 - '-ForceV1'
24 condition: selection
25falsepositives:
26 - Very Likely, including launching cmd.exe via Run As Administrator
27level: informational
References
Related rules
- Potential Binary Impersonating Sysinternals Tools
- Suspicious Cmdl32 Execution
- Troubleshooting Pack Cmdlet Execution
- Renamed CURL.EXE Execution
- Rundll32 Execution Without CommandLine Parameters