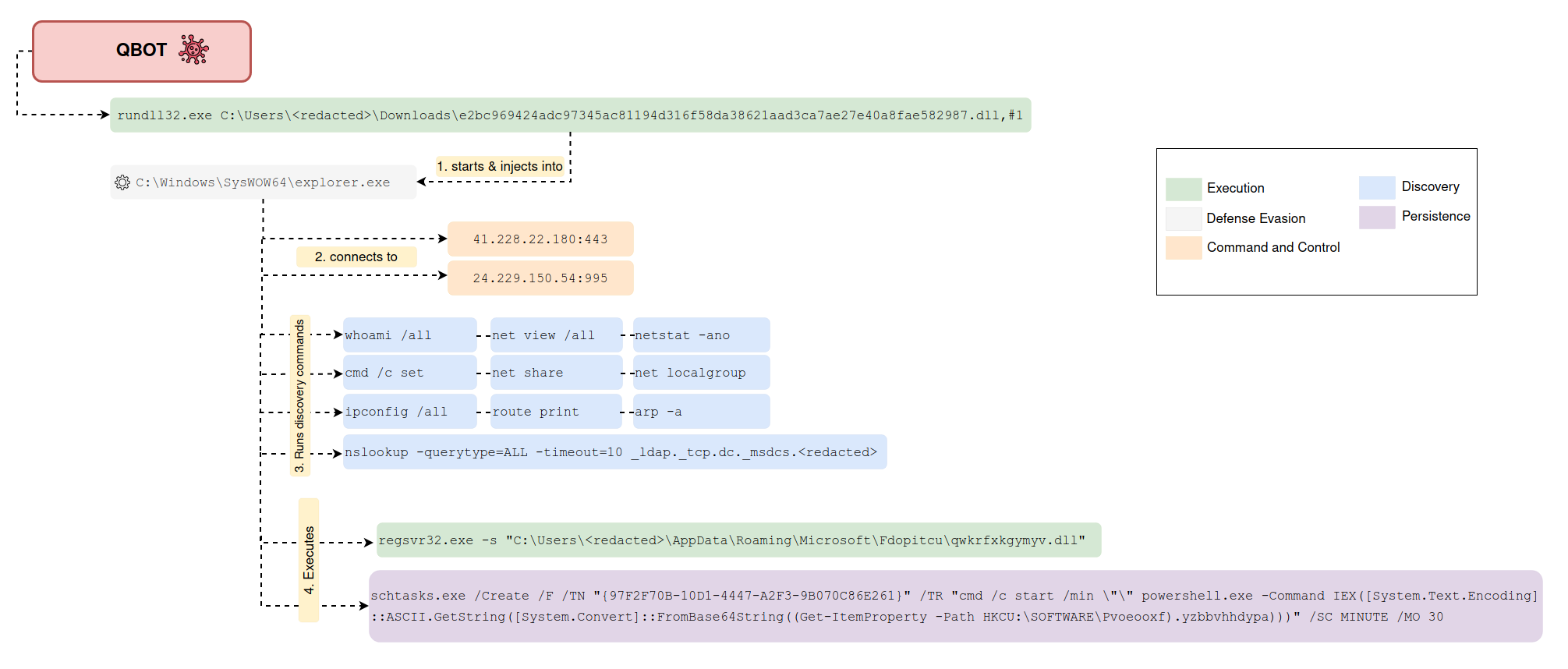
Suspicious Computer Machine Password by PowerShell
The Reset-ComputerMachinePassword cmdlet changes the computer account password that the computers use to authenticate to the domain controllers in the domain. You can use it to reset the password of the local computer.
Sigma rule (View on GitHub)
1title: Suspicious Computer Machine Password by PowerShell
2id: e3818659-5016-4811-a73c-dde4679169d2
3status: test
4description: |
5 The Reset-ComputerMachinePassword cmdlet changes the computer account password that the computers use to authenticate to the domain controllers in the domain.
6 You can use it to reset the password of the local computer.
7references:
8 - https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.management/reset-computermachinepassword?view=powershell-5.1
9 - https://thedfirreport.com/2022/02/21/qbot-and-zerologon-lead-to-full-domain-compromise/
10author: frack113
11date: 2022-02-21
12tags:
13 - attack.privilege-escalation
14 - attack.persistence
15 - attack.defense-evasion
16 - attack.initial-access
17 - attack.t1078
18logsource:
19 product: windows
20 category: ps_module
21 definition: 0ad03ef1-f21b-4a79-8ce8-e6900c54b65b
22detection:
23 selection:
24 ContextInfo|contains: 'Reset-ComputerMachinePassword'
25 condition: selection
26falsepositives:
27 - Administrator PowerShell scripts
28level: medium
References
Related rules
- AWS Key Pair Import Activity
- AWS Suspicious SAML Activity
- Account Created And Deleted Within A Close Time Frame
- Authentications To Important Apps Using Single Factor Authentication
- Azure Domain Federation Settings Modified