Malicious Named Pipe Created
Detects the creation of a named pipe seen used by known APTs or malware.
Sigma rule (View on GitHub)
1title: Malicious Named Pipe Created
2id: fe3ac066-98bb-432a-b1e7-a5229cb39d4a
3status: test
4description: Detects the creation of a named pipe seen used by known APTs or malware.
5references:
6 - https://securelist.com/wild-neutron-economic-espionage-threat-actor-returns-with-new-tricks/71275/
7 - https://securelist.com/faq-the-projectsauron-apt/75533/
8 - https://web.archive.org/web/20180725233601/https://www.pwc.co.uk/cyber-security/pdf/cloud-hopper-annex-b-final.pdf
9 - https://www.us-cert.gov/ncas/alerts/TA17-117A
10 - https://www.fireeye.com/blog/threat-research/2020/12/evasive-attacker-leverages-solarwinds-supply-chain-compromises-with-sunburst-backdoor.html
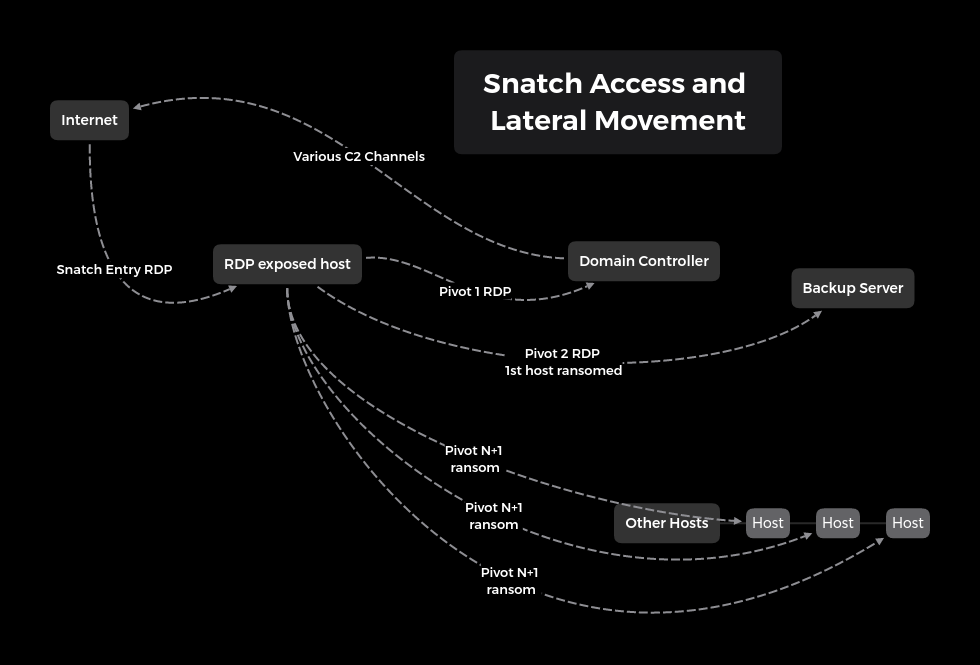
11 - https://thedfirreport.com/2020/06/21/snatch-ransomware/
12 - https://github.com/RiccardoAncarani/LiquidSnake
13 - https://www.accenture.com/us-en/blogs/cyber-defense/turla-belugasturgeon-compromises-government-entity
14 - https://us-cert.cisa.gov/ncas/analysis-reports/ar19-304a
15 - https://download.bitdefender.com/resources/files/News/CaseStudies/study/115/Bitdefender-Whitepaper-PAC-A4-en-EN1.pdf
16 - https://unit42.paloaltonetworks.com/emissary-panda-attacks-middle-east-government-sharepoint-servers/
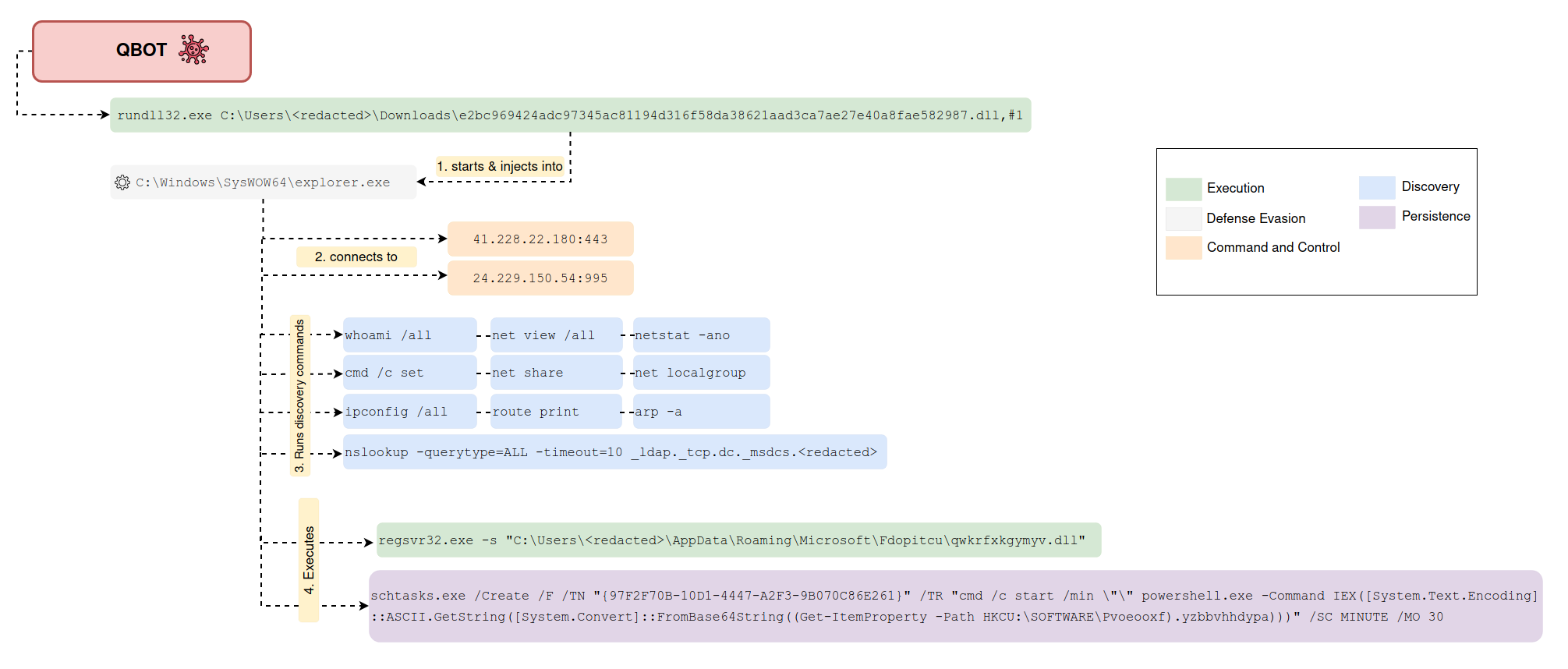
17 - https://thedfirreport.com/2022/02/21/qbot-and-zerologon-lead-to-full-domain-compromise/
18author: Florian Roth (Nextron Systems), blueteam0ps, elhoim
19date: 2017-11-06
20modified: 2023-08-07
21tags:
22 - attack.defense-evasion
23 - attack.privilege-escalation
24 - attack.t1055
25logsource:
26 product: windows
27 category: pipe_created
28 definition: 'Note that you have to configure logging for Named Pipe Events in Sysmon config (Event ID 17 and Event ID 18). The basic configuration is in popular sysmon configuration (https://github.com/SwiftOnSecurity/sysmon-config), but it is worth verifying. You can also use other repo, e.g. https://github.com/Neo23x0/sysmon-config, https://github.com/olafhartong/sysmon-modular. How to test detection? You can check powershell script from this site https://svch0st.medium.com/guide-to-named-pipes-and-hunting-for-cobalt-strike-pipes-dc46b2c5f575'
29detection:
30 selection:
31 PipeName:
32 - '\46a676ab7f179e511e30dd2dc41bd388' # Project Sauron
33 - '\583da945-62af-10e8-4902-a8f205c72b2e' # SolarWinds SUNBURST malware
34 - '\6e7645c4-32c5-4fe3-aabf-e94c2f4370e7' # LiquidSnake
35 - '\9f81f59bc58452127884ce513865ed20' # Project Sauron
36 - '\adschemerpc' # Turla HyperStack
37 - '\ahexec' # Sofacy group malware
38 - '\AnonymousPipe' # Hidden Cobra Hoplight
39 - '\bc31a7' # Pacifier
40 - '\bc367' # Pacifier
41 - '\bizkaz' # Snatch Ransomware
42 - '\csexecsvc' # CSEXEC default
43 - '\dce_3d' # Qbot
44 - '\e710f28d59aa529d6792ca6ff0ca1b34' # Project Sauron
45 - '\gruntsvc' # Covenant default
46 - '\isapi_dg' # Uroburos Malware
47 - '\isapi_dg2' # Uroburos Malware
48 - '\isapi_http' # Uroburos Malware
49 - '\jaccdpqnvbrrxlaf' # PoshC2 default
50 - '\lsassw' # Wild Neutron APT malware
51 - '\NamePipe_MoreWindows' # Cloud Hopper - RedLeaves
52 - '\pcheap_reuse' # Pipe used by Equation Group malware
53 - '\Posh*' # PoshC2 default
54 - '\rpchlp_3' # Project Sauron
55 - '\sdlrpc' # Cobra Trojan
56 - '\svcctl' # Crackmapexec smbexec default
57 - '\testPipe' # Emissary Panda Hyperbro
58 - '\winsession' # Wild Neutron APT malware
59 # - '\status_*' # CS default https://github.com/SigmaHQ/sigma/issues/253
60 condition: selection
61falsepositives:
62 - Unknown
63level: critical
References
Related rules
- APT PRIVATELOG Image Load Pattern
- CobaltStrike Named Pipe
- CobaltStrike Named Pipe Pattern Regex
- CobaltStrike Named Pipe Patterns
- Malware Shellcode in Verclsid Target Process