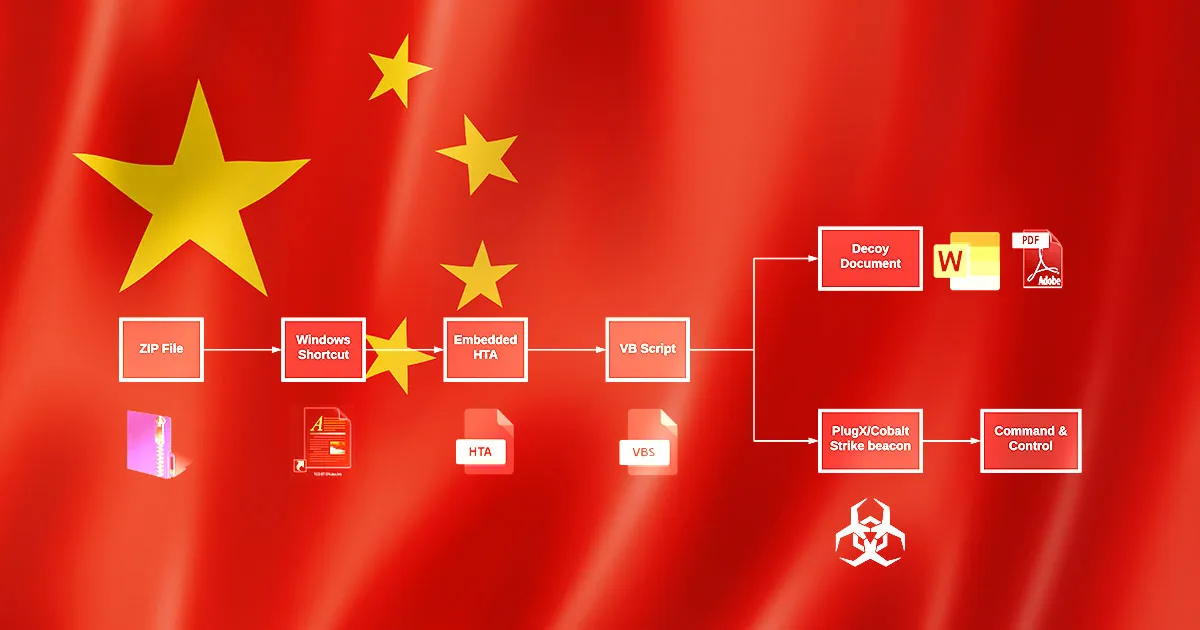
Suspicious Double Extension Files
Detects dropped files with double extensions, which is often used by malware as a method to abuse the fact that Windows hide default extensions by default.
Sigma rule (View on GitHub)
1title: Suspicious Double Extension Files
2id: b4926b47-a9d7-434c-b3a0-adc3fa0bd13e
3related:
4 - id: 1cdd9a09-06c9-4769-99ff-626e2b3991b8
5 type: derived
6 - id: 3215aa19-f060-4332-86d5-5602511f3ca8
7 type: similar
8status: test
9description: Detects dropped files with double extensions, which is often used by malware as a method to abuse the fact that Windows hide default extensions by default.
10references:
11 - https://www.crowdstrike.com/blog/meet-crowdstrikes-adversary-of-the-month-for-june-mustang-panda/
12 - https://www.anomali.com/blog/china-based-apt-mustang-panda-targets-minority-groups-public-and-private-sector-organizations
13 - https://www.cybereason.com/blog/research/a-bazar-of-tricks-following-team9s-development-cycles
14 - https://twitter.com/malwrhunterteam/status/1235135745611960321
15 - https://twitter.com/luc4m/status/1073181154126254080
16 - https://cloud.google.com/blog/topics/threat-intelligence/cybercriminals-weaponize-fake-ai-websites
17 - https://vipre.com/blog/svg-phishing-attacks-the-new-trick-in-the-cybercriminals-playbook/
18author: Nasreddine Bencherchali (Nextron Systems), frack113
19date: 2022-06-19
20modified: 2025-07-22
21tags:
22 - attack.defense-evasion
23 - attack.t1036.007
24logsource:
25 category: file_event
26 product: windows
27detection:
28 selection_gen:
29 TargetFilename|endswith:
30 - '.exe'
31 - '.iso'
32 - '.rar'
33 - '.svg'
34 - '.zip'
35 # - '.lnk' # legitimate links can happen just anywhere
36 TargetFilename|contains:
37 - '.doc.'
38 - '.docx.'
39 - '.gif.'
40 - '.jpeg.'
41 - '.jpg.'
42 - '.mp3.'
43 - '.mp4.'
44 - '.pdf.'
45 - '.png.'
46 - '.ppt.'
47 - '.pptx.'
48 - '.rtf.'
49 - '.svg.'
50 - '.txt.'
51 - '.xls.'
52 - '.xlsx.'
53 selection_exe:
54 TargetFilename|endswith:
55 - '.rar.exe'
56 - '.zip.exe'
57 # Note: If you wanna keep using the ".lnk" extension. You might uncomment this filter and add additional locations
58 # filter_main_lnk:
59 # TargetFilename|contains:
60 # - '\AppData\Roaming\Microsoft\Office\Recent\'
61 # - '\AppData\Roaming\Microsoft\Windows\Recent\'
62 condition: 1 of selection_*
63falsepositives:
64 - Unlikely
65level: high
References
Related rules
- Suspicious Parent Double Extension File Execution
- Disabling Windows Defender WMI Autologger Session via Reg.exe
- PowerShell Defender Threat Severity Default Action Set to 'Allow' or 'NoAction'
- Windows Defender Context Menu Removed
- Windows Defender Threat Severity Default Action Modified