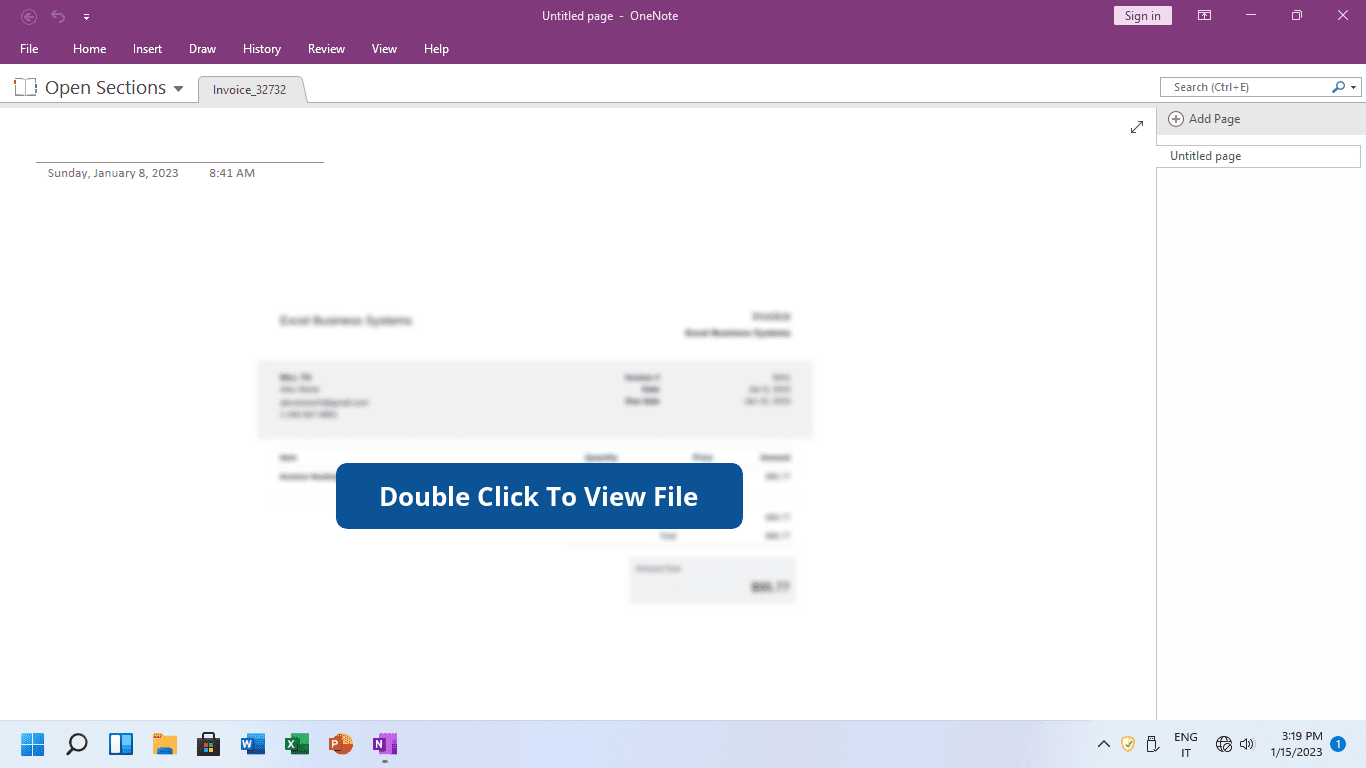
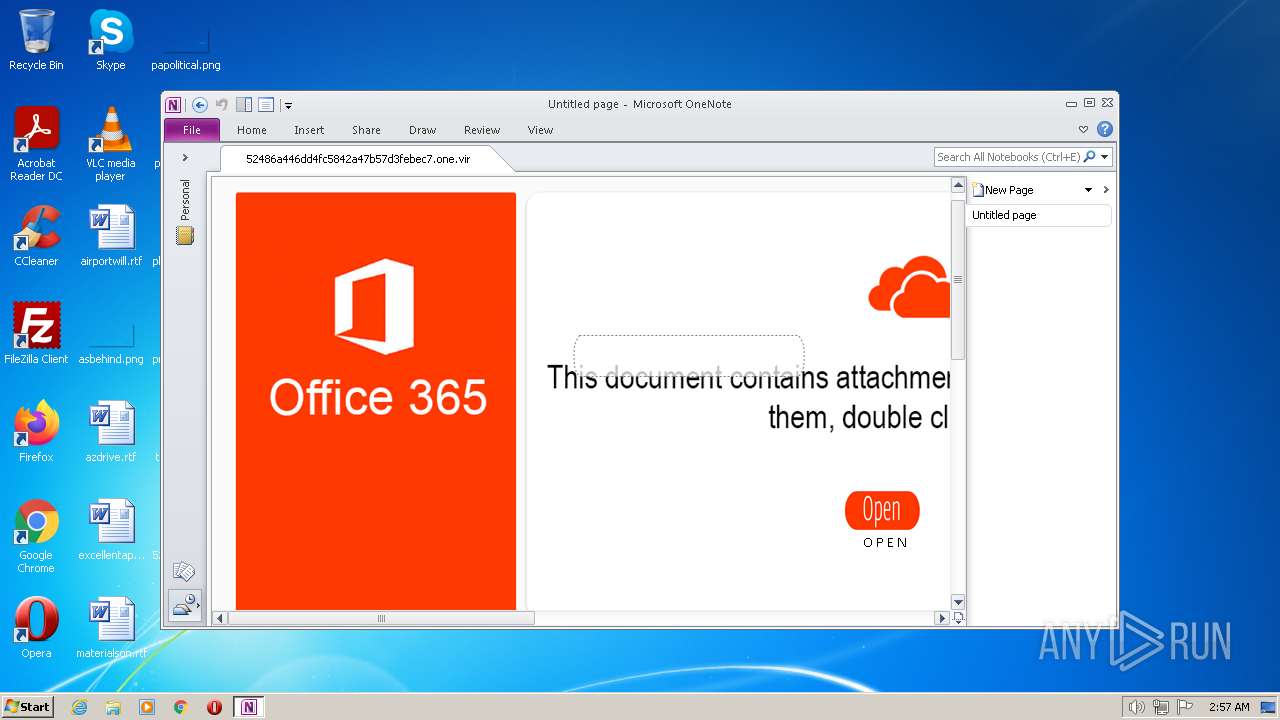
Suspicious File Created Via OneNote Application
Detects suspicious files created via the OneNote application. This could indicate a potential malicious ".one"/".onepkg" file was executed as seen being used in malware activity in the wild
Sigma rule (View on GitHub)
1title: Suspicious File Created Via OneNote Application
2id: fcc6d700-68d9-4241-9a1a-06874d621b06
3status: test
4description: Detects suspicious files created via the OneNote application. This could indicate a potential malicious ".one"/".onepkg" file was executed as seen being used in malware activity in the wild
5references:
6 - https://www.bleepingcomputer.com/news/security/hackers-now-use-microsoft-onenote-attachments-to-spread-malware/
7 - https://blog.osarmor.com/319/onenote-attachment-delivers-asyncrat-malware/
8 - https://twitter.com/MaD_c4t/status/1623414582382567424
9 - https://labs.withsecure.com/publications/detecting-onenote-abuse
10 - https://www.trustedsec.com/blog/new-attacks-old-tricks-how-onenote-malware-is-evolving/
11 - https://app.any.run/tasks/17f2d378-6d11-4d6f-8340-954b04f35e83/
12author: Nasreddine Bencherchali (Nextron Systems)
13date: 2023-02-09
14modified: 2023-02-27
15tags:
16 - attack.defense-evasion
17logsource:
18 category: file_event
19 product: windows
20detection:
21 selection:
22 Image|endswith:
23 - '\onenote.exe'
24 - '\onenotem.exe'
25 - '\onenoteim.exe'
26 TargetFilename|contains: '\AppData\Local\Temp\OneNote\'
27 TargetFilename|endswith:
28 # TODO: Add more suspicious extensions
29 - '.bat'
30 - '.chm'
31 - '.cmd'
32 - '.dll'
33 - '.exe'
34 - '.hta'
35 - '.htm'
36 - '.html'
37 - '.js'
38 - '.lnk'
39 - '.ps1'
40 - '.vbe'
41 - '.vbs'
42 - '.wsf'
43 condition: selection
44falsepositives:
45 - False positives should be very low with the extensions list cited. Especially if you don't heavily utilize OneNote.
46 - Occasional FPs might occur if OneNote is used internally to share different embedded documents
47level: high
References
Related rules
- AD Object WriteDAC Access
- AMSI Bypass Pattern Assembly GetType
- APT PRIVATELOG Image Load Pattern
- APT29 2018 Phishing Campaign CommandLine Indicators
- APT29 2018 Phishing Campaign File Indicators