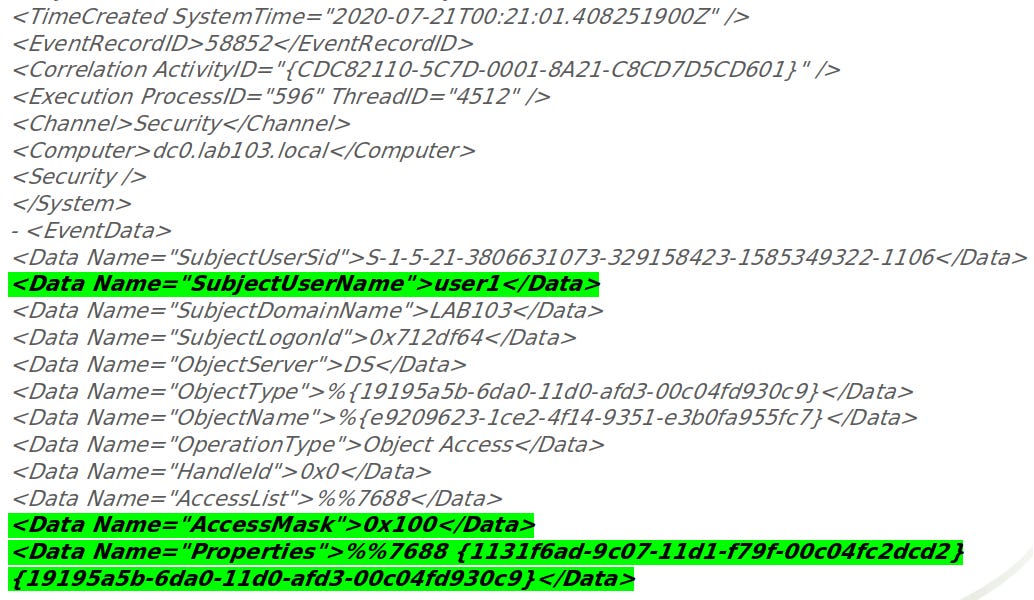
Mimikatz DC Sync
Detects Mimikatz DC sync security events
Sigma rule (View on GitHub)
1title: Mimikatz DC Sync
2id: 611eab06-a145-4dfa-a295-3ccc5c20f59a
3status: test
4description: Detects Mimikatz DC sync security events
5references:
6 - https://twitter.com/gentilkiwi/status/1003236624925413376
7 - https://gist.github.com/gentilkiwi/dcc132457408cf11ad2061340dcb53c2
8 - https://blog.blacklanternsecurity.com/p/detecting-dcsync?s=r
9 - https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-10/security/threat-protection/auditing/event-4662
10author: Benjamin Delpy, Florian Roth (Nextron Systems), Scott Dermott, Sorina Ionescu
11date: 2018-06-03
12modified: 2022-04-26
13tags:
14 - attack.credential-access
15 - attack.s0002
16 - attack.t1003.006
17logsource:
18 product: windows
19 service: security
20detection:
21 selection:
22 EventID: 4662
23 Properties|contains:
24 - 'Replicating Directory Changes All'
25 - '1131f6ad-9c07-11d1-f79f-00c04fc2dcd2'
26 - '1131f6aa-9c07-11d1-f79f-00c04fc2dcd2'
27 - '9923a32a-3607-11d2-b9be-0000f87a36b2'
28 - '89e95b76-444d-4c62-991a-0facbeda640c'
29 AccessMask: '0x100'
30 filter1:
31 SubjectDomainName: 'Window Manager'
32 filter2:
33 SubjectUserName|startswith:
34 - 'NT AUT'
35 - 'MSOL_'
36 filter3:
37 SubjectUserName|endswith: '$'
38 condition: selection and not 1 of filter*
39falsepositives:
40 - Valid DC Sync that is not covered by the filters; please report
41 - Local Domain Admin account used for Azure AD Connect
42level: high
References
Related rules
- Mimikatz Use
- Active Directory Replication from Non Machine Account
- Credential Dumping Attempt Via WerFault
- Credential Dumping Tools Service Execution - Security
- Credential Dumping Tools Service Execution - System