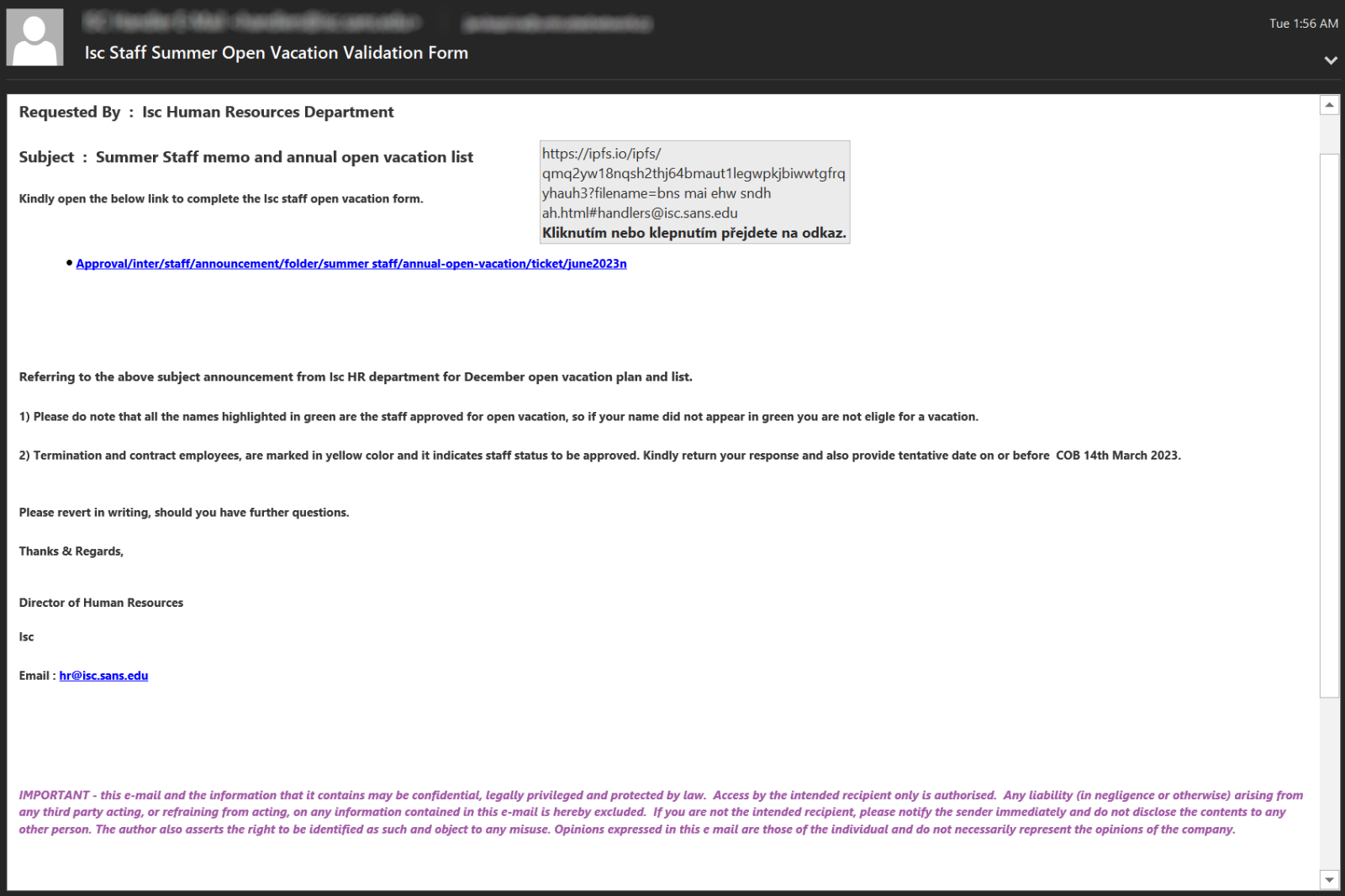
Suspicious Network Communication With IPFS
Detects connections to interplanetary file system (IPFS) containing a user's email address which mirrors behaviours observed in recent phishing campaigns leveraging IPFS to host credential harvesting webpages.
Sigma rule (View on GitHub)
1title: Suspicious Network Communication With IPFS
2id: eb6c2004-1cef-427f-8885-9042974e5eb6
3status: test
4description: Detects connections to interplanetary file system (IPFS) containing a user's email address which mirrors behaviours observed in recent phishing campaigns leveraging IPFS to host credential harvesting webpages.
5references:
6 - https://blog.talosintelligence.com/ipfs-abuse/
7 - https://github.com/Cisco-Talos/IOCs/tree/80caca039988252fbb3f27a2e89c2f2917f582e0/2022/11
8 - https://isc.sans.edu/diary/IPFS%20phishing%20and%20the%20need%20for%20correctly%20set%20HTTP%20security%20headers/29638
9author: Gavin Knapp
10date: 2023-03-16
11tags:
12 - attack.collection
13 - attack.credential-access
14 - attack.t1056
15logsource:
16 category: proxy
17detection:
18 selection:
19 cs-uri|re: '(?i)(ipfs\.io/|ipfs\.io\s).+\..+@.+\.[a-z]+'
20 condition: selection
21falsepositives:
22 - Legitimate use of IPFS being used in the organisation. However the cs-uri regex looking for a user email will likely negate this.
23level: low
References
Related rules
- DNS Query Request To OneLaunch Update Service
- APT31 Judgement Panda Activity
- Attempts of Kerberos Coercion Via DNS SPN Spoofing
- HackTool - ADCSPwn Execution
- HackTool - Impacket Tools Execution