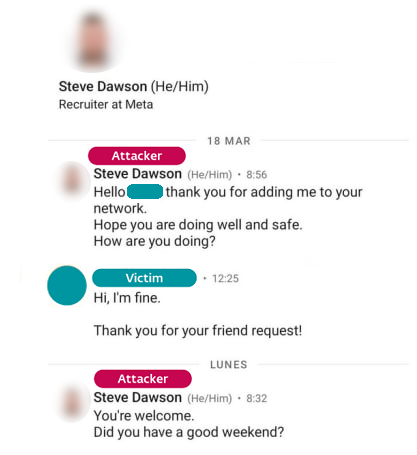
Lazarus APT DLL Sideloading Activity
Detects sideloading of trojanized DLLs used in Lazarus APT campaign in the case of a Spanish aerospace company
Sigma rule (View on GitHub)
1title: Lazarus APT DLL Sideloading Activity
2id: 24007168-a26b-4049-90d0-ce138e13a5cf
3status: test
4description: Detects sideloading of trojanized DLLs used in Lazarus APT campaign in the case of a Spanish aerospace company
5references:
6 - https://www.welivesecurity.com/en/eset-research/lazarus-luring-employees-trojanized-coding-challenges-case-spanish-aerospace-company/
7 - https://www.bleepingcomputer.com/news/security/lazarus-hackers-breach-aerospace-firm-with-new-lightlesscan-malware/
8author: Thurein Oo, Nasreddine Bencherchali (Nextron Systems)
9date: 2023-10-18
10tags:
11 - attack.defense-evasion
12 - attack.privilege-escalation
13 - attack.persistence
14 - attack.t1574.001
15 - attack.g0032
16 - detection.emerging-threats
17logsource:
18 product: windows
19 category: image_load
20detection:
21 selection_mscoree:
22 Image: 'C:\ProgramShared\PresentationHost.exe'
23 ImageLoaded: ':\ProgramShared\mscoree.dll'
24 selection_colorui:
25 Image: 'C:\ProgramData\Adobe\colorcpl.exe'
26 ImageLoaded: 'C:\ProgramData\Adobe\colorui.dll'
27 selection_mapistub:
28 Image: 'C:\ProgramData\Oracle\Java\fixmapi.exe'
29 ImageLoaded: 'C:\ProgramData\Oracle\Java\mapistub.dll'
30 selection_hid:
31 Image: 'C:\ProgramData\Adobe\ARM\tabcal.exe'
32 ImageLoaded: 'C:\ProgramData\Adobe\ARM\HID.dll'
33 condition: 1 of selection_*
34falsepositives:
35 - Unlikely
36level: high
References
Related rules
- APT27 - Emissary Panda Activity
- DLL Names Used By SVR For GraphicalProton Backdoor
- Diamond Sleet APT DLL Sideloading Indicators
- Pingback Backdoor Activity
- Pingback Backdoor DLL Loading Activity