OWASSRF Exploitation Attempt Using Public POC - Webserver
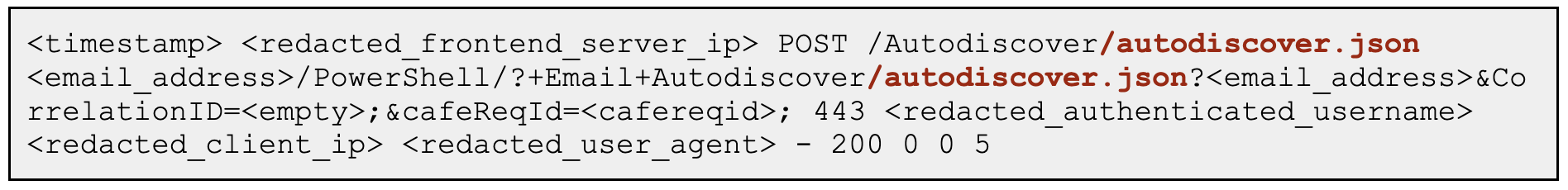
Detects exploitation attempt of the OWASSRF variant targeting exchange servers using publicly available POC. It uses the OWA endpoint to access the powershell backend endpoint
Sigma rule (View on GitHub)
1title: OWASSRF Exploitation Attempt Using Public POC - Webserver
2id: 92d78c63-5a5c-4c40-9b60-463810ffb082
3status: test
4description: Detects exploitation attempt of the OWASSRF variant targeting exchange servers using publicly available POC. It uses the OWA endpoint to access the powershell backend endpoint
5references:
6 - https://www.crowdstrike.com/blog/owassrf-exploit-analysis-and-recommendations/
7 - https://www.rapid7.com/blog/post/2022/12/21/cve-2022-41080-cve-2022-41082-rapid7-observed-exploitation-of-owassrf-in-exchange-for-rce/
8 - https://twitter.com/purp1ew0lf/status/1602989967776808961?s=12&t=OkZJl_ViICeiftVEsohRyw
9author: Nasreddine Bencherchali (Nextron Systems)
10date: 2022-12-22
11modified: 2023-01-02
12tags:
13 - attack.initial-access
14 - attack.t1190
15 - detection.emerging-threats
16logsource:
17 category: webserver
18detection:
19 selection:
20 # Look for the header: X-OWA-ExplicitLogonUser: owa/mastermailbox@outlook.com
21 cs-user-agent: 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.5195.54 Safari/537.36'
22 cs-method: 'POST'
23 sc-status: 200
24 cs-uri-query|contains|all:
25 - '/owa/mastermailbox'
26 - '/powershell'
27 condition: selection
28falsepositives:
29 - Unlikely
30level: critical
References
Related rules
- ADSelfService Exploitation
- Apache Spark Shell Command Injection - Weblogs
- Atlassian Bitbucket Command Injection Via Archive API
- CVE-2010-5278 Exploitation Attempt
- CVE-2020-0688 Exploitation Attempt