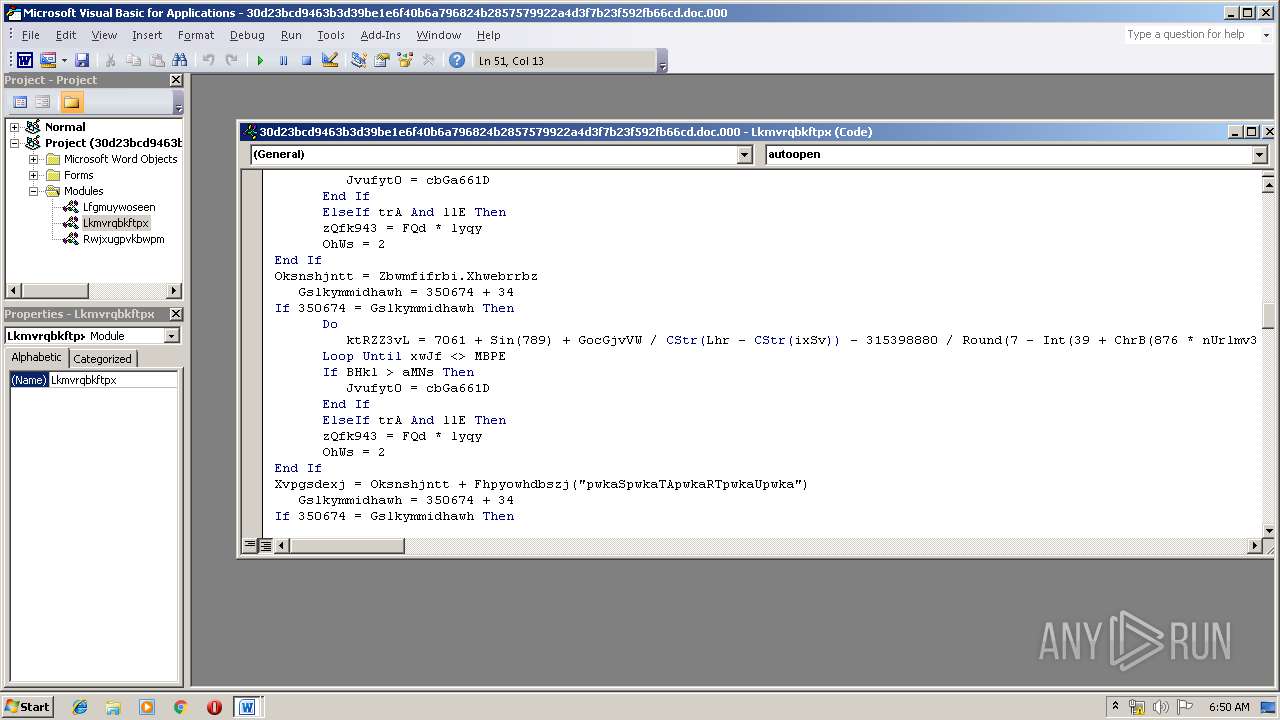
Potential Emotet Activity
Detects all Emotet like process executions that are not covered by the more generic rules
Sigma rule (View on GitHub)
1title: Potential Emotet Activity
2id: d02e8cf5-6099-48cf-9bfc-1eec2d0c7b18
3status: stable
4description: Detects all Emotet like process executions that are not covered by the more generic rules
5references:
6 - https://app.any.run/tasks/e13ab713-64cf-4b23-ad93-6dceaa5429ac/
7 - https://app.any.run/tasks/81f3c28c-c686-425d-8a2b-a98198d244e1/
8 - https://app.any.run/tasks/97f875e8-0e08-4328-815f-055e971ba754/
9 - https://app.any.run/tasks/84fc9b4a-ea2b-47b1-8aa6-9014402dfb56/
10author: Florian Roth (Nextron Systems)
11date: 2019-09-30
12modified: 2023-02-04
13tags:
14 - attack.execution
15 - attack.t1059.001
16 - attack.defense-evasion
17 - attack.t1027
18 - detection.emerging-threats
19logsource:
20 category: process_creation
21 product: windows
22detection:
23 selection:
24 CommandLine|contains:
25 - ' -e* PAA'
26 - 'JABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQ' # $env:userprofile
27 - 'QAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUA' # $env:userprofile
28 - 'kAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlA' # $env:userprofile
29 - 'IgAoACcAKgAnACkAOwAkA' # "('*');$
30 - 'IAKAAnACoAJwApADsAJA' # "('*');$
31 - 'iACgAJwAqACcAKQA7ACQA' # "('*');$
32 - 'JABGAGwAeAByAGgAYwBmAGQ'
33 - 'PQAkAGUAbgB2ADoAdABlAG0AcAArACgA' # =$env:temp+(
34 - '0AJABlAG4AdgA6AHQAZQBtAHAAKwAoA' # =$env:temp+(
35 - '9ACQAZQBuAHYAOgB0AGUAbQBwACsAKA' # =$env:temp+(
36 filter:
37 CommandLine|contains:
38 - 'fAAgAEMAbwBuAHYAZQByAHQAVABvAC0ASgBzAG8AbgAgAC0ARQByAHIAbwByAEEAYwB0AGkAbwBuACAAUwBpAGwAZQBuAHQAbAB5AEMAbwBuAHQAaQBuAHUAZQ'
39 - 'wAIABDAG8AbgB2AGUAcgB0AFQAbwAtAEoAcwBvAG4AIAAtAEUAcgByAG8AcgBBAGMAdABpAG8AbgAgAFMAaQBsAGUAbgB0AGwAeQBDAG8AbgB0AGkAbgB1AGUA'
40 - '8ACAAQwBvAG4AdgBlAHIAdABUAG8ALQBKAHMAbwBuACAALQBFAHIAcgBvAHIAQQBjAHQAaQBvAG4AIABTAGkAbABlAG4AdABsAHkAQwBvAG4AdABpAG4AdQBlA'
41 condition: selection and not filter
42falsepositives:
43 - Unlikely
44level: high
References
Related rules
- Turla Group Commands May 2020
- Operation Wocao Activity
- Operation Wocao Activity - Security
- PowerShell Base64 Encoded Reflective Assembly Load
- Suspicious Encoded And Obfuscated Reflection Assembly Load Function Call