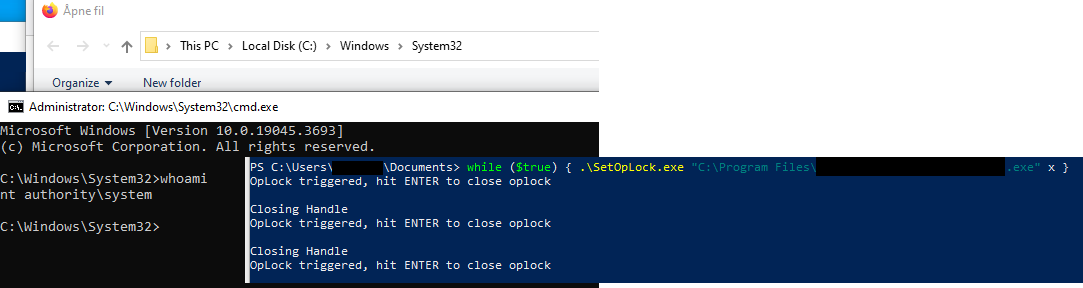
Potential Escalation via Vulnerable MSI Repair
Identifies when a browser process navigates to the Microsoft Help page followed by spawning an elevated process. This may indicate a successful exploitation for privilege escalation abusing a vulnerable Windows Installer repair setup.
Elastic rule (View on GitHub)
1[metadata]
2creation_date = "2024/09/12"
3integration = ["endpoint", "sentinel_one_cloud_funnel", "m365_defender", "windows"]
4maturity = "production"
5updated_date = "2025/03/20"
6
7[rule]
8author = ["Elastic"]
9description = """
10Identifies when a browser process navigates to the Microsoft Help page followed by spawning an elevated process. This
11may indicate a successful exploitation for privilege escalation abusing a vulnerable Windows Installer repair setup.
12"""
13from = "now-9m"
14index = [
15 "winlogbeat-*",
16 "endgame-*",
17 "logs-endpoint.events.process-*",
18 "logs-windows.sysmon_operational-*",
19 "logs-sentinel_one_cloud_funnel.*",
20 "logs-m365_defender.event-*",
21]
22language = "eql"
23license = "Elastic License v2"
24name = "Potential Escalation via Vulnerable MSI Repair"
25note = """## Triage and analysis
26
27> **Disclaimer**:
28> This investigation guide was created using generative AI technology and has been reviewed to improve its accuracy and relevance. While every effort has been made to ensure its quality, we recommend validating the content and adapting it to suit your specific environment and operational needs.
29
30### Investigating Potential Escalation via Vulnerable MSI Repair
31
32Windows Installer (MSI) is a service used for software installation and maintenance. Adversaries exploit vulnerabilities in MSI repair functions to gain elevated privileges. This detection rule identifies suspicious activity by monitoring browser processes accessing Microsoft Help pages, followed by elevated process creation, indicating potential privilege escalation attempts.
33
34### Possible investigation steps
35
36- Review the alert details to identify the specific browser process that accessed the Microsoft Help page, noting the process name and command line details.
37- Check the user domain associated with the process to confirm if it matches "NT AUTHORITY", "AUTORITE NT", or "AUTORIDADE NT", which may indicate a system-level account was used.
38- Investigate the parent process of the browser to determine if it was expected or if it shows signs of compromise or unusual behavior.
39- Examine the timeline of events to see if an elevated process was spawned shortly after the browser accessed the Microsoft Help page, indicating potential exploitation.
40- Correlate the event with other security logs or alerts from data sources like Elastic Endgame, Sysmon, or Microsoft Defender for Endpoint to gather additional context or evidence of malicious activity.
41- Assess the risk and impact of the elevated process by identifying its actions and any changes made to the system, such as modifications to critical files or registry keys.
42
43### False positive analysis
44
45- Legitimate software updates or installations may trigger the rule if they involve browser-based help documentation. To manage this, identify and whitelist known software update processes that frequently access Microsoft Help pages.
46- Automated scripts or administrative tools that use browsers to access Microsoft Help for legitimate purposes can cause false positives. Exclude these scripts or tools by specifying their unique command-line patterns or process names.
47- User-initiated troubleshooting or help-seeking behavior that involves accessing Microsoft Help pages might be misinterpreted as suspicious. Educate users on safe browsing practices and consider excluding specific user accounts or domains that are known to frequently engage in such activities.
48- Security tools or monitoring solutions that simulate browser activity for testing purposes may inadvertently trigger the rule. Identify these tools and create exceptions based on their process names or command-line arguments to prevent unnecessary alerts.
49
50### Response and remediation
51
52- Immediately isolate the affected system from the network to prevent further exploitation or lateral movement by the adversary.
53- Terminate any suspicious elevated processes that were spawned following the browser's navigation to the Microsoft Help page to halt potential privilege escalation activities.
54- Conduct a thorough review of the affected system's event logs and process creation history to identify any unauthorized changes or additional indicators of compromise.
55- Apply the latest security patches and updates to the Windows Installer service and any other vulnerable components to mitigate the exploited vulnerability.
56- Restore the affected system from a known good backup if unauthorized changes or persistent threats are detected that cannot be easily remediated.
57- Monitor the network for any signs of similar exploitation attempts or related suspicious activities, using enhanced detection rules and threat intelligence feeds.
58- Escalate the incident to the security operations center (SOC) or incident response team for further investigation and to ensure comprehensive remediation and recovery efforts."""
59references = [
60 "https://sec-consult.com/blog/detail/msi-installer-repair-to-system-a-detailed-journey/",
61 "https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2024-38014",
62]
63risk_score = 73
64rule_id = "043d80a3-c49e-43ef-9c72-1088f0c7b278"
65severity = "high"
66tags = [
67 "Domain: Endpoint",
68 "OS: Windows",
69 "Use Case: Threat Detection",
70 "Tactic: Privilege Escalation",
71 "Data Source: Elastic Endgame",
72 "Data Source: Elastic Defend",
73 "Data Source: Sysmon",
74 "Data Source: SentinelOne",
75 "Data Source: Microsoft Defender for Endpoint",
76 "Resources: Investigation Guide",
77]
78timestamp_override = "event.ingested"
79type = "eql"
80
81query = '''
82process where event.type == "start" and host.os.type == "windows" and
83 user.domain : ("NT AUTHORITY", "AUTORITE NT", "AUTORIDADE NT") and
84 process.parent.name : ("chrome.exe", "msedge.exe", "brave.exe", "whale.exe", "browser.exe", "dragon.exe", "vivaldi.exe",
85 "opera.exe", "iexplore", "firefox.exe", "waterfox.exe", "iexplore.exe", "tor.exe", "safari.exe") and
86 process.parent.command_line : "*go.microsoft.com*"
87'''
88
89
90[[rule.threat]]
91framework = "MITRE ATT&CK"
92[[rule.threat.technique]]
93id = "T1068"
94name = "Exploitation for Privilege Escalation"
95reference = "https://attack.mitre.org/techniques/T1068/"
96
97
98[rule.threat.tactic]
99id = "TA0004"
100name = "Privilege Escalation"
101reference = "https://attack.mitre.org/tactics/TA0004/"
102[[rule.threat]]
103framework = "MITRE ATT&CK"
104[[rule.threat.technique]]
105id = "T1218"
106name = "System Binary Proxy Execution"
107reference = "https://attack.mitre.org/techniques/T1218/"
108[[rule.threat.technique.subtechnique]]
109id = "T1218.007"
110name = "Msiexec"
111reference = "https://attack.mitre.org/techniques/T1218/007/"
112
113
114
115[rule.threat.tactic]
116id = "TA0005"
117name = "Defense Evasion"
118reference = "https://attack.mitre.org/tactics/TA0005/"
Triage and analysis
Disclaimer: This investigation guide was created using generative AI technology and has been reviewed to improve its accuracy and relevance. While every effort has been made to ensure its quality, we recommend validating the content and adapting it to suit your specific environment and operational needs.
Investigating Potential Escalation via Vulnerable MSI Repair
Windows Installer (MSI) is a service used for software installation and maintenance. Adversaries exploit vulnerabilities in MSI repair functions to gain elevated privileges. This detection rule identifies suspicious activity by monitoring browser processes accessing Microsoft Help pages, followed by elevated process creation, indicating potential privilege escalation attempts.
Possible investigation steps
- Review the alert details to identify the specific browser process that accessed the Microsoft Help page, noting the process name and command line details.
- Check the user domain associated with the process to confirm if it matches "NT AUTHORITY", "AUTORITE NT", or "AUTORIDADE NT", which may indicate a system-level account was used.
- Investigate the parent process of the browser to determine if it was expected or if it shows signs of compromise or unusual behavior.
- Examine the timeline of events to see if an elevated process was spawned shortly after the browser accessed the Microsoft Help page, indicating potential exploitation.
- Correlate the event with other security logs or alerts from data sources like Elastic Endgame, Sysmon, or Microsoft Defender for Endpoint to gather additional context or evidence of malicious activity.
- Assess the risk and impact of the elevated process by identifying its actions and any changes made to the system, such as modifications to critical files or registry keys.
False positive analysis
- Legitimate software updates or installations may trigger the rule if they involve browser-based help documentation. To manage this, identify and whitelist known software update processes that frequently access Microsoft Help pages.
- Automated scripts or administrative tools that use browsers to access Microsoft Help for legitimate purposes can cause false positives. Exclude these scripts or tools by specifying their unique command-line patterns or process names.
- User-initiated troubleshooting or help-seeking behavior that involves accessing Microsoft Help pages might be misinterpreted as suspicious. Educate users on safe browsing practices and consider excluding specific user accounts or domains that are known to frequently engage in such activities.
- Security tools or monitoring solutions that simulate browser activity for testing purposes may inadvertently trigger the rule. Identify these tools and create exceptions based on their process names or command-line arguments to prevent unnecessary alerts.
Response and remediation
- Immediately isolate the affected system from the network to prevent further exploitation or lateral movement by the adversary.
- Terminate any suspicious elevated processes that were spawned following the browser's navigation to the Microsoft Help page to halt potential privilege escalation activities.
- Conduct a thorough review of the affected system's event logs and process creation history to identify any unauthorized changes or additional indicators of compromise.
- Apply the latest security patches and updates to the Windows Installer service and any other vulnerable components to mitigate the exploited vulnerability.
- Restore the affected system from a known good backup if unauthorized changes or persistent threats are detected that cannot be easily remediated.
- Monitor the network for any signs of similar exploitation attempts or related suspicious activities, using enhanced detection rules and threat intelligence feeds.
- Escalate the incident to the security operations center (SOC) or incident response team for further investigation and to ensure comprehensive remediation and recovery efforts.
References
Related rules
- Conhost Spawned By Suspicious Parent Process
- Creation or Modification of a new GPO Scheduled Task or Service
- Persistence via TelemetryController Scheduled Task Hijack
- Persistence via Update Orchestrator Service Hijack
- Privilege Escalation via Named Pipe Impersonation