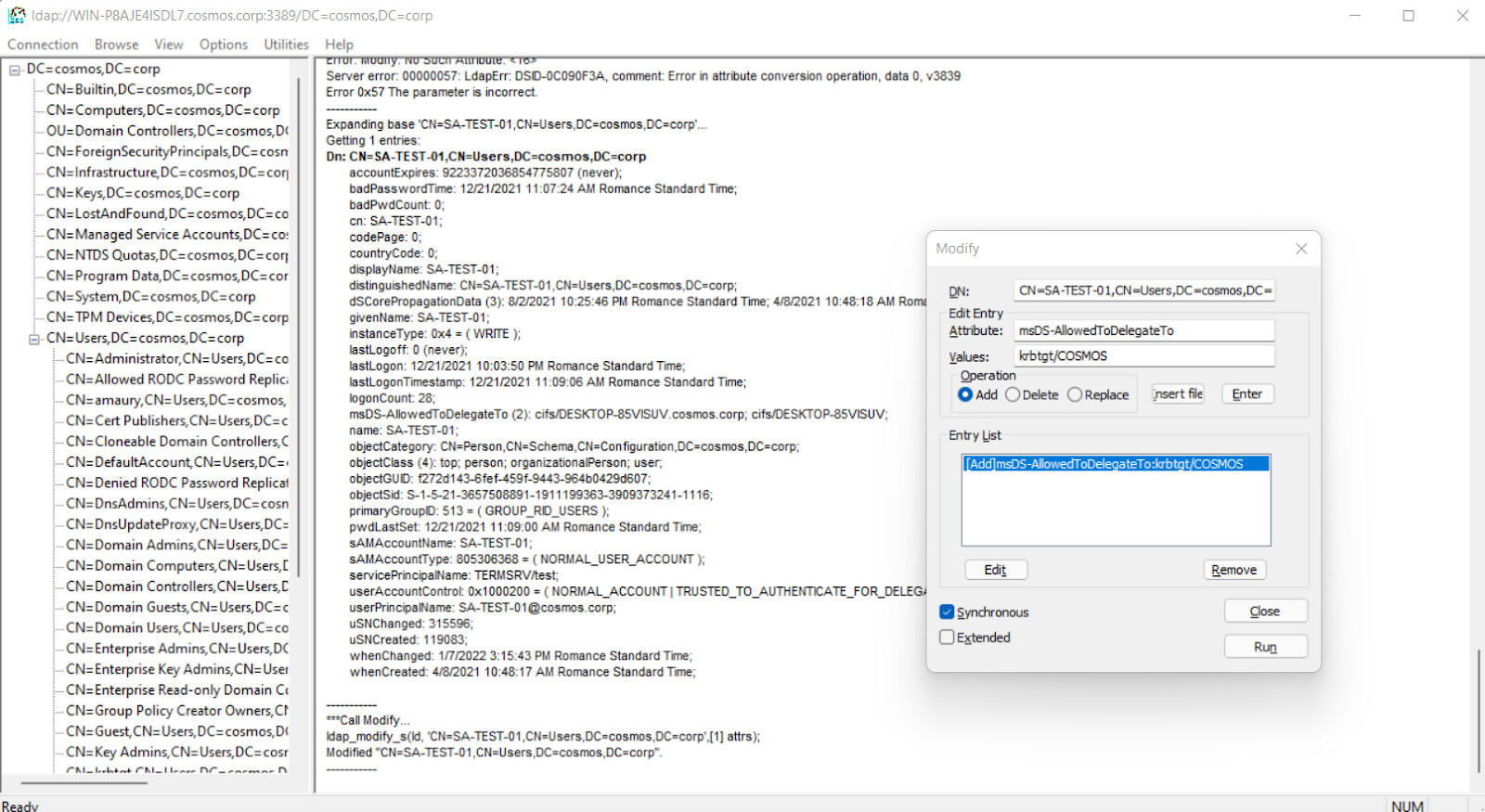
KRBTGT Delegation Backdoor
Identifies the modification of the msDS-AllowedToDelegateTo attribute to KRBTGT. Attackers can use this technique to maintain persistence to the domain by having the ability to request tickets for the KRBTGT service.
Elastic rule (View on GitHub)
1[metadata]
2creation_date = "2022/01/27"
3integration = ["system", "windows"]
4maturity = "production"
5updated_date = "2025/11/14"
6
7[rule]
8author = ["Elastic"]
9description = """
10Identifies the modification of the msDS-AllowedToDelegateTo attribute to KRBTGT. Attackers can use this technique to
11maintain persistence to the domain by having the ability to request tickets for the KRBTGT service.
12"""
13from = "now-9m"
14index = ["logs-system.security*", "logs-windows.forwarded*", "winlogbeat-*"]
15language = "eql"
16license = "Elastic License v2"
17name = "KRBTGT Delegation Backdoor"
18note = """## Triage and analysis
19
20> **Disclaimer**:
21> This investigation guide was created using generative AI technology and has been reviewed to improve its accuracy and relevance. While every effort has been made to ensure its quality, we recommend validating the content and adapting it to suit your specific environment and operational needs.
22
23### Investigating KRBTGT Delegation Backdoor
24
25In Active Directory, the KRBTGT account is crucial for Kerberos ticket granting. Adversaries may exploit this by altering the msDS-AllowedToDelegateTo attribute, enabling unauthorized ticket requests and persistent domain access. The detection rule identifies such modifications by monitoring specific event actions and codes, flagging high-risk changes to the KRBTGT delegation settings.
26
27### Possible investigation steps
28
29- Review the event logs for the specific event code 4738 to identify the user account that was modified and verify if the msDS-AllowedToDelegateTo attribute includes the KRBTGT service.
30- Investigate the user account that performed the modification by checking their recent activities and login history to determine if the action was authorized or suspicious.
31- Examine the timeline of the modification event to correlate it with any other unusual activities or alerts in the network around the same time.
32- Check for any other modifications to sensitive attributes or accounts in Active Directory that might indicate a broader compromise.
33- Assess the potential impact on the domain by evaluating the access level and permissions of the modified account and any associated systems or services.
34- Consult with the IT security team to determine if there are any known maintenance activities or changes that could explain the modification, ensuring it was not a legitimate administrative action.
35
36### False positive analysis
37
38- Routine administrative tasks involving legitimate changes to the msDS-AllowedToDelegateTo attribute for service accounts may trigger alerts. Review the context of the change and verify with the IT team if it aligns with scheduled maintenance or updates.
39- Automated scripts or tools used for Active Directory management might modify delegation settings as part of their operations. Identify these scripts and exclude their activity from triggering alerts by creating exceptions based on the script's signature or the account used.
40- Changes made by trusted third-party applications that require delegation for functionality can be mistaken for malicious activity. Document these applications and adjust the detection rule to exclude their known and expected behavior.
41- Regular audits or compliance checks that involve modifications to delegation settings should be accounted for. Coordinate with audit teams to schedule these activities and temporarily adjust monitoring rules to prevent false positives during these periods.
42
43### Response and remediation
44
45- Immediately isolate the affected system from the network to prevent further unauthorized access or ticket requests using the KRBTGT account.
46- Revert any unauthorized changes to the msDS-AllowedToDelegateTo attribute for the KRBTGT account by restoring it to its previous state using a known good backup or manually resetting the attribute.
47- Reset the KRBTGT account password twice to invalidate any existing Kerberos tickets that may have been issued using the compromised delegation settings.
48- Conduct a thorough review of recent changes to user accounts and delegation settings in Active Directory to identify any other potential unauthorized modifications.
49- Escalate the incident to the security operations center (SOC) or incident response team for further investigation and to determine the scope of the compromise.
50- Implement enhanced monitoring for changes to critical accounts and attributes in Active Directory, focusing on the KRBTGT account and similar high-value targets.
51- Review and update access controls and delegation permissions to ensure that only authorized personnel have the ability to modify sensitive attributes like msDS-AllowedToDelegateTo."""
52references = [
53 "https://skyblue.team/posts/delegate-krbtgt",
54 "https://github.com/atc-project/atomic-threat-coverage/blob/master/Atomic_Threat_Coverage/Logging_Policies/LP_0026_windows_audit_user_account_management.md",
55]
56risk_score = 73
57rule_id = "e052c845-48d0-4f46-8a13-7d0aba05df82"
58setup = """## Setup
59
60The 'Audit User Account Management' logging policy must be configured for (Success, Failure).
61Steps to implement the logging policy with Advanced Audit Configuration:
Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policies Configuration > Audit Policies > Account Management > Audit User Account Management (Success,Failure)
1"""
2severity = "high"
3tags = [
4 "Domain: Endpoint",
5 "OS: Windows",
6 "Use Case: Threat Detection",
7 "Tactic: Persistence",
8 "Use Case: Active Directory Monitoring",
9 "Data Source: Active Directory",
10 "Data Source: Windows Security Event Logs",
11 "Resources: Investigation Guide",
12]
13timestamp_override = "event.ingested"
14type = "eql"
15
16query = '''
17iam where host.os.type == "windows" and event.code == "4738" and winlog.event_data.AllowedToDelegateTo : "*krbtgt*"
18'''
19
20
21[[rule.threat]]
22framework = "MITRE ATT&CK"
23[[rule.threat.technique]]
24id = "T1098"
25name = "Account Manipulation"
26reference = "https://attack.mitre.org/techniques/T1098/"
27
28
29[rule.threat.tactic]
30id = "TA0003"
31name = "Persistence"
32reference = "https://attack.mitre.org/tactics/TA0003/"
33[[rule.threat]]
34framework = "MITRE ATT&CK"
35[[rule.threat.technique]]
36id = "T1558"
37name = "Steal or Forge Kerberos Tickets"
38reference = "https://attack.mitre.org/techniques/T1558/"
39
40
41[rule.threat.tactic]
42id = "TA0006"
43name = "Credential Access"
44reference = "https://attack.mitre.org/tactics/TA0006/"
Triage and analysis
Disclaimer: This investigation guide was created using generative AI technology and has been reviewed to improve its accuracy and relevance. While every effort has been made to ensure its quality, we recommend validating the content and adapting it to suit your specific environment and operational needs.
Investigating KRBTGT Delegation Backdoor
In Active Directory, the KRBTGT account is crucial for Kerberos ticket granting. Adversaries may exploit this by altering the msDS-AllowedToDelegateTo attribute, enabling unauthorized ticket requests and persistent domain access. The detection rule identifies such modifications by monitoring specific event actions and codes, flagging high-risk changes to the KRBTGT delegation settings.
Possible investigation steps
- Review the event logs for the specific event code 4738 to identify the user account that was modified and verify if the msDS-AllowedToDelegateTo attribute includes the KRBTGT service.
- Investigate the user account that performed the modification by checking their recent activities and login history to determine if the action was authorized or suspicious.
- Examine the timeline of the modification event to correlate it with any other unusual activities or alerts in the network around the same time.
- Check for any other modifications to sensitive attributes or accounts in Active Directory that might indicate a broader compromise.
- Assess the potential impact on the domain by evaluating the access level and permissions of the modified account and any associated systems or services.
- Consult with the IT security team to determine if there are any known maintenance activities or changes that could explain the modification, ensuring it was not a legitimate administrative action.
False positive analysis
- Routine administrative tasks involving legitimate changes to the msDS-AllowedToDelegateTo attribute for service accounts may trigger alerts. Review the context of the change and verify with the IT team if it aligns with scheduled maintenance or updates.
- Automated scripts or tools used for Active Directory management might modify delegation settings as part of their operations. Identify these scripts and exclude their activity from triggering alerts by creating exceptions based on the script's signature or the account used.
- Changes made by trusted third-party applications that require delegation for functionality can be mistaken for malicious activity. Document these applications and adjust the detection rule to exclude their known and expected behavior.
- Regular audits or compliance checks that involve modifications to delegation settings should be accounted for. Coordinate with audit teams to schedule these activities and temporarily adjust monitoring rules to prevent false positives during these periods.
Response and remediation
- Immediately isolate the affected system from the network to prevent further unauthorized access or ticket requests using the KRBTGT account.
- Revert any unauthorized changes to the msDS-AllowedToDelegateTo attribute for the KRBTGT account by restoring it to its previous state using a known good backup or manually resetting the attribute.
- Reset the KRBTGT account password twice to invalidate any existing Kerberos tickets that may have been issued using the compromised delegation settings.
- Conduct a thorough review of recent changes to user accounts and delegation settings in Active Directory to identify any other potential unauthorized modifications.
- Escalate the incident to the security operations center (SOC) or incident response team for further investigation and to determine the scope of the compromise.
- Implement enhanced monitoring for changes to critical accounts and attributes in Active Directory, focusing on the KRBTGT account and similar high-value targets.
- Review and update access controls and delegation permissions to ensure that only authorized personnel have the ability to modify sensitive attributes like msDS-AllowedToDelegateTo.
References
Related rules
- AdminSDHolder Backdoor
- AdminSDHolder SDProp Exclusion Added
- Potential Privileged Escalation via SamAccountName Spoofing
- Sensitive Privilege SeEnableDelegationPrivilege assigned to a User
- User Added to Privileged Group in Active Directory