Potential Remote Desktop Shadowing Activity
Identifies the modification of the Remote Desktop Protocol (RDP) Shadow registry or the execution of processes indicative of an active RDP shadowing session. An adversary may abuse the RDP Shadowing feature to spy on or control other users active RDP sessions.
Elastic rule (View on GitHub)
1[metadata]
2creation_date = "2021/04/12"
3integration = ["endpoint", "windows", "m365_defender", "sentinel_one_cloud_funnel"]
4maturity = "production"
5updated_date = "2025/09/11"
6
7[rule]
8author = ["Elastic"]
9description = """
10Identifies the modification of the Remote Desktop Protocol (RDP) Shadow registry or the execution of processes
11indicative of an active RDP shadowing session. An adversary may abuse the RDP Shadowing feature to spy on or control
12other users active RDP sessions.
13"""
14from = "now-9m"
15index = [
16 "logs-endpoint.events.process-*",
17 "logs-endpoint.events.registry-*",
18 "winlogbeat-*",
19 "logs-windows.sysmon_operational-*",
20 "endgame-*",
21 "logs-m365_defender.event-*",
22 "logs-sentinel_one_cloud_funnel.*",
23]
24language = "eql"
25license = "Elastic License v2"
26name = "Potential Remote Desktop Shadowing Activity"
27note = """## Triage and analysis
28
29> **Disclaimer**:
30> This investigation guide was created using generative AI technology and has been reviewed to improve its accuracy and relevance. While every effort has been made to ensure its quality, we recommend validating the content and adapting it to suit your specific environment and operational needs.
31
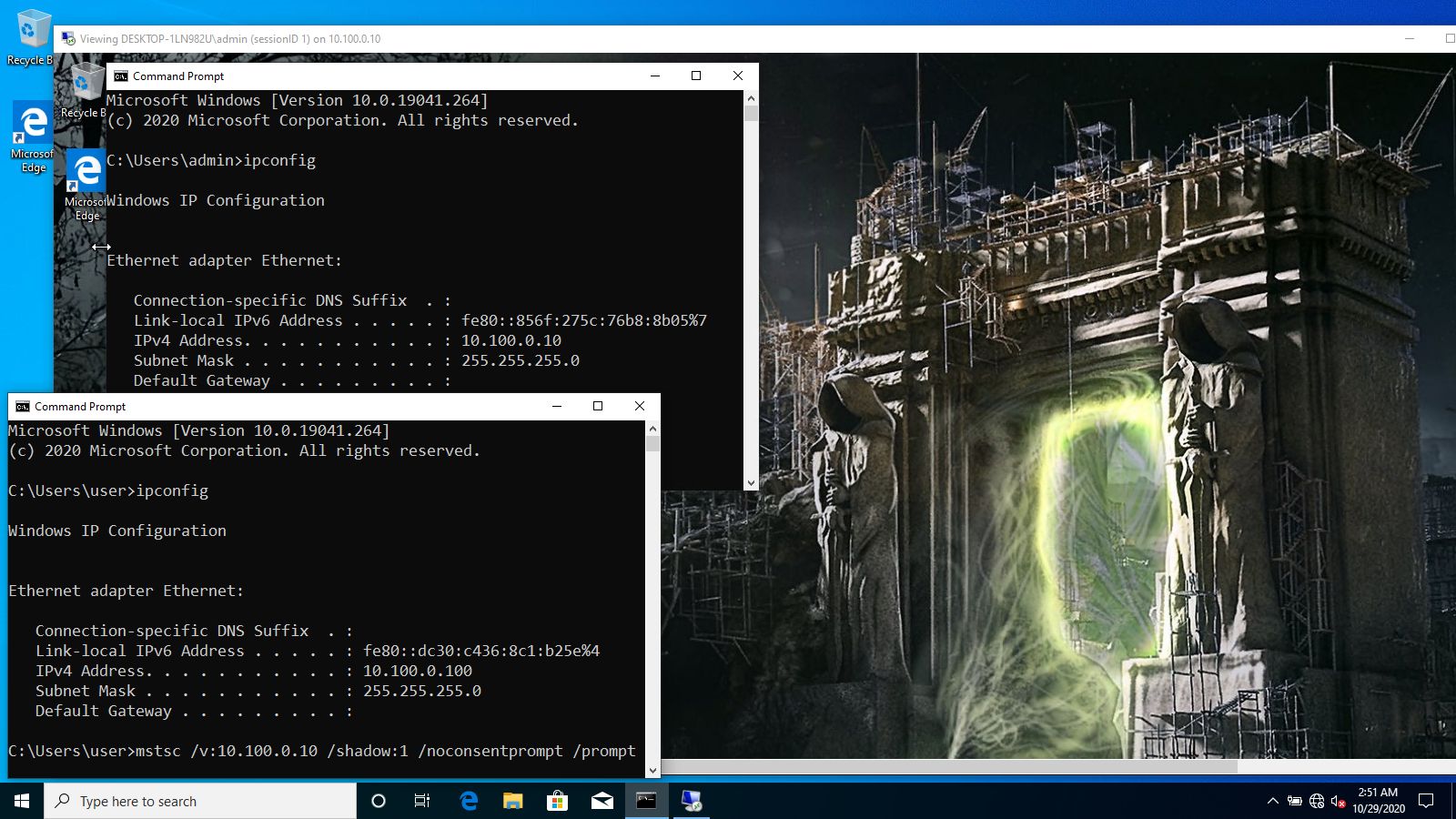
32### Investigating Potential Remote Desktop Shadowing Activity
33
34Remote Desktop Shadowing allows administrators to view or control active RDP sessions, aiding in support and troubleshooting. However, adversaries can exploit this feature to monitor or hijack user sessions without consent. The detection rule identifies suspicious modifications to RDP Shadow registry settings and the execution of specific processes linked to shadowing, signaling potential misuse.
35
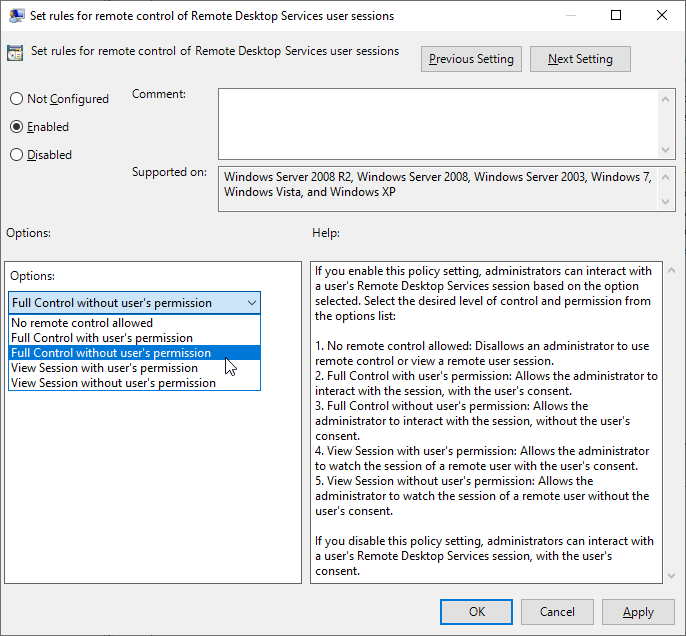
36### Possible investigation steps
37
38- Review the registry event details to confirm if there was a modification to the RDP Shadow registry path, specifically checking for changes in "HKLM\\Software\\Policies\\Microsoft\\Windows NT\\Terminal Services\\Shadow".
39- Investigate the process events to identify if "RdpSaUacHelper.exe" or "RdpSaProxy.exe" were started by "svchost.exe", which could indicate unauthorized shadowing activity.
40- Check for any instances of "mstsc.exe" being executed with the "/shadow:*" argument, as this could signify an attempt to shadow an RDP session.
41- Correlate the identified processes and registry changes with user activity logs to determine if the actions were authorized or expected as part of legitimate administrative tasks.
42- Analyze network logs for any unusual remote connections or lateral movement patterns that coincide with the timing of the detected shadowing activity.
43- Consult endpoint security solutions like Microsoft Defender for Endpoint or SentinelOne for additional context or alerts related to the same host or user account involved in the shadowing activity.
44
45### False positive analysis
46
47- Legitimate administrative activities may trigger alerts when IT staff use RDP Shadowing for support. To manage this, create exceptions for known IT administrator accounts or specific IP addresses.
48- Scheduled maintenance or automated scripts that modify RDP Shadow registry settings can be mistaken for malicious activity. Identify and exclude these processes or scripts from the detection rule.
49- Security software or monitoring tools that interact with RDP sessions might mimic shadowing behavior. Verify these tools and whitelist their processes to prevent false alerts.
50- Training sessions or remote support tools that use RDP Shadowing features can generate alerts. Document and exclude these activities by identifying their unique process names or arguments.
51
52### Response and remediation
53
54- Immediately isolate the affected system from the network to prevent further unauthorized access or lateral movement.
55- Terminate any suspicious processes identified in the alert, such as RdpSaUacHelper.exe, RdpSaProxy.exe, or mstsc.exe with shadowing arguments, to stop potential session hijacking.
56- Revert any unauthorized changes to the RDP Shadow registry settings to their default or secure state to prevent further exploitation.
57- Conduct a thorough review of user accounts and permissions on the affected system to ensure no unauthorized changes have been made, and reset passwords for any compromised accounts.
58- Escalate the incident to the security operations center (SOC) or incident response team for further investigation and to determine if additional systems are affected.
59- Implement enhanced monitoring and logging for RDP activities across the network to detect and respond to similar threats more quickly in the future.
60- Review and update RDP access policies and configurations to ensure they align with best practices, such as enforcing multi-factor authentication and limiting RDP access to only necessary users and systems."""
61references = [
62 "https://blog.bitsadmin.com/spying-on-users-using-rdp-shadowing",
63 "https://swarm.ptsecurity.com/remote-desktop-services-shadowing/",
64]
65risk_score = 73
66rule_id = "c57f8579-e2a5-4804-847f-f2732edc5156"
67severity = "high"
68tags = [
69 "Domain: Endpoint",
70 "OS: Windows",
71 "Use Case: Threat Detection",
72 "Tactic: Lateral Movement",
73 "Data Source: Elastic Endgame",
74 "Data Source: Elastic Defend",
75 "Data Source: Sysmon",
76 "Data Source: Microsoft Defender for Endpoint",
77 "Data Source: SentinelOne",
78 "Resources: Investigation Guide",
79]
80timestamp_override = "event.ingested"
81type = "eql"
82
83query = '''
84/* Identifies the modification of RDP Shadow registry or
85 the execution of processes indicative of active shadow RDP session */
86
87any where host.os.type == "windows" and
88(
89 (event.category == "registry" and event.type == "change" and
90 registry.value : "Shadow" and
91 registry.path : (
92 "*\\Software\\Policies\\Microsoft\\Windows NT\\Terminal Services\\Shadow"
93 ) and
94 registry.data.strings : ("1", "0x00000001", "2", "0x00000002", "3", "0x00000003", "4", "0x00000004")
95
96 ) or
97 (event.category == "process" and event.type == "start" and
98 (process.name : ("RdpSaUacHelper.exe", "RdpSaProxy.exe") and process.parent.name : "svchost.exe") or
99 (?process.pe.original_file_name : "mstsc.exe" and process.args : "/shadow:*")
100 )
101)
102'''
103
104
105[[rule.threat]]
106framework = "MITRE ATT&CK"
107[[rule.threat.technique]]
108id = "T1021"
109name = "Remote Services"
110reference = "https://attack.mitre.org/techniques/T1021/"
111[[rule.threat.technique.subtechnique]]
112id = "T1021.001"
113name = "Remote Desktop Protocol"
114reference = "https://attack.mitre.org/techniques/T1021/001/"
115
116
117
118[rule.threat.tactic]
119id = "TA0008"
120name = "Lateral Movement"
121reference = "https://attack.mitre.org/tactics/TA0008/"
Triage and analysis
Disclaimer: This investigation guide was created using generative AI technology and has been reviewed to improve its accuracy and relevance. While every effort has been made to ensure its quality, we recommend validating the content and adapting it to suit your specific environment and operational needs.
Investigating Potential Remote Desktop Shadowing Activity
Remote Desktop Shadowing allows administrators to view or control active RDP sessions, aiding in support and troubleshooting. However, adversaries can exploit this feature to monitor or hijack user sessions without consent. The detection rule identifies suspicious modifications to RDP Shadow registry settings and the execution of specific processes linked to shadowing, signaling potential misuse.
Possible investigation steps
- Review the registry event details to confirm if there was a modification to the RDP Shadow registry path, specifically checking for changes in "HKLM\Software\Policies\Microsoft\Windows NT\Terminal Services\Shadow".
- Investigate the process events to identify if "RdpSaUacHelper.exe" or "RdpSaProxy.exe" were started by "svchost.exe", which could indicate unauthorized shadowing activity.
- Check for any instances of "mstsc.exe" being executed with the "/shadow:*" argument, as this could signify an attempt to shadow an RDP session.
- Correlate the identified processes and registry changes with user activity logs to determine if the actions were authorized or expected as part of legitimate administrative tasks.
- Analyze network logs for any unusual remote connections or lateral movement patterns that coincide with the timing of the detected shadowing activity.
- Consult endpoint security solutions like Microsoft Defender for Endpoint or SentinelOne for additional context or alerts related to the same host or user account involved in the shadowing activity.
False positive analysis
- Legitimate administrative activities may trigger alerts when IT staff use RDP Shadowing for support. To manage this, create exceptions for known IT administrator accounts or specific IP addresses.
- Scheduled maintenance or automated scripts that modify RDP Shadow registry settings can be mistaken for malicious activity. Identify and exclude these processes or scripts from the detection rule.
- Security software or monitoring tools that interact with RDP sessions might mimic shadowing behavior. Verify these tools and whitelist their processes to prevent false alerts.
- Training sessions or remote support tools that use RDP Shadowing features can generate alerts. Document and exclude these activities by identifying their unique process names or arguments.
Response and remediation
- Immediately isolate the affected system from the network to prevent further unauthorized access or lateral movement.
- Terminate any suspicious processes identified in the alert, such as RdpSaUacHelper.exe, RdpSaProxy.exe, or mstsc.exe with shadowing arguments, to stop potential session hijacking.
- Revert any unauthorized changes to the RDP Shadow registry settings to their default or secure state to prevent further exploitation.
- Conduct a thorough review of user accounts and permissions on the affected system to ensure no unauthorized changes have been made, and reset passwords for any compromised accounts.
- Escalate the incident to the security operations center (SOC) or incident response team for further investigation and to determine if additional systems are affected.
- Implement enhanced monitoring and logging for RDP activities across the network to detect and respond to similar threats more quickly in the future.
- Review and update RDP access policies and configurations to ensure they align with best practices, such as enforcing multi-factor authentication and limiting RDP access to only necessary users and systems.
References
Related rules
- Unusual Child Process of dns.exe
- Microsoft Exchange Server UM Spawning Suspicious Processes
- NullSessionPipe Registry Modification
- RDP Enabled via Registry
- Local Account TokenFilter Policy Disabled