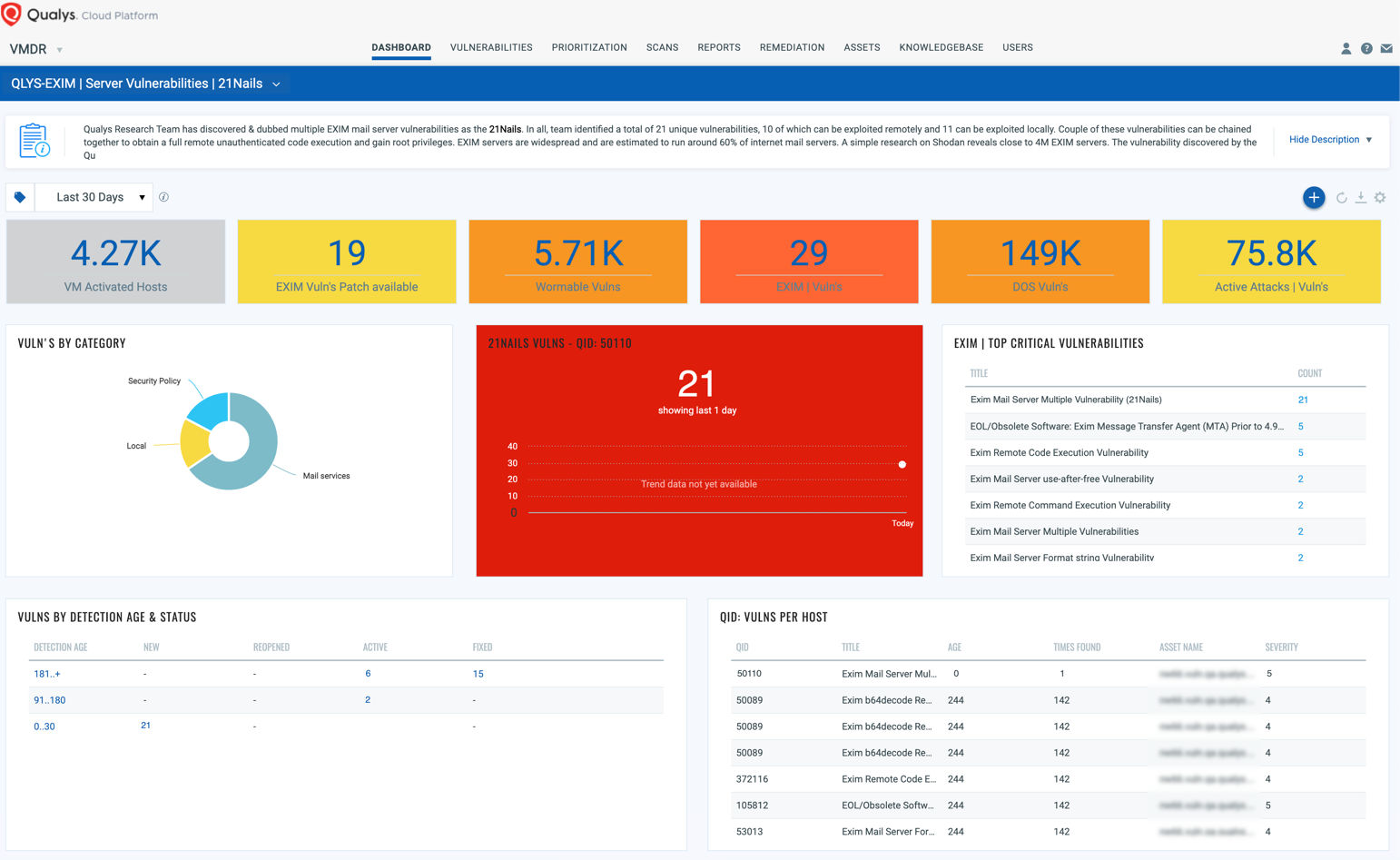
Unusual Exim4 Child Process
This rule detects the execution of unusual commands via a descendant process of exim4. Attackers may use descendant processes of exim4 to evade detection and establish persistence or execute post-exploitation commands on a target system.
Elastic rule (View on GitHub)
1[metadata]
2creation_date = "2025/04/30"
3integration = ["endpoint"]
4maturity = "production"
5updated_date = "2025/12/23"
6
7[rule]
8author = ["Elastic"]
9description = """
10This rule detects the execution of unusual commands via a descendant process of exim4. Attackers may use descendant
11processes of exim4 to evade detection and establish persistence or execute post-exploitation commands on a target system.
12"""
13from = "now-9m"
14index = ["logs-endpoint.events.process*"]
15language = "kuery"
16license = "Elastic License v2"
17name = "Unusual Exim4 Child Process"
18note = """ ## Triage and analysis
19
20> **Disclaimer**:
21> This investigation guide was created using generative AI technology and has been reviewed to improve its accuracy and relevance. While every effort has been made to ensure its quality, we recommend validating the content and adapting it to suit your specific environment and operational needs.
22
23### Investigating Unusual Exim4 Child Process
24
25Exim4 is a widely used mail transfer agent on Linux systems, responsible for routing and delivering email. Adversaries may exploit Exim4 by spawning unexpected child processes to execute malicious commands, thereby evading detection and maintaining persistence. The detection rule identifies suspicious child processes initiated by Exim4, excluding known legitimate processes, to flag potential misuse.
26
27### Possible investigation steps
28
29- Review the alert details to identify the specific unusual child process name and command line arguments that were executed under the parent process exim4.
30- Examine the process tree to understand the hierarchy and context of the spawned process, including any sibling or child processes that may indicate further malicious activity.
31- Check the user account associated with the exim4 process to determine if it aligns with expected usage patterns or if it might be compromised.
32- Investigate the source and destination of any network connections initiated by the unusual child process to identify potential data exfiltration or command and control activity.
33- Analyze system logs around the time of the alert to identify any related events or anomalies that could provide additional context or evidence of compromise.
34- Correlate the findings with other alerts or incidents in the environment to determine if this activity is part of a broader attack campaign.
35
36### False positive analysis
37
38- Development tools like cmake, gcc, and cppcheck may trigger false positives if they are used in environments where Exim4 is installed. To mitigate this, ensure these tools are included in the exclusion list if they are part of regular development activities.
39- System maintenance scripts that utilize commands such as readlink, grep, and stat might be flagged. Review these scripts and add them to the exclusion list if they are verified as part of routine system operations.
40- Automated deployment or configuration management tools that invoke systemctl or update-exim4.conf can be mistaken for suspicious activity. Confirm these processes are legitimate and add them to the exclusion list to prevent unnecessary alerts.
41- If Exim4 is used in conjunction with SSH services, processes like sshd may appear as child processes. Verify the legitimacy of these connections and exclude them if they are part of expected behavior.
42- Regularly review and update the exclusion list to reflect changes in system operations or new legitimate processes that may arise, ensuring the rule remains effective without generating excessive false positives.
43
44### Response and remediation
45
46- Immediately isolate the affected system from the network to prevent further malicious activity and lateral movement.
47- Terminate any suspicious child processes of Exim4 that are not recognized as legitimate, using process management tools like `kill` or `pkill`.
48- Conduct a thorough review of the Exim4 configuration files and scripts to identify unauthorized modifications or additions, and restore them from a known good backup if necessary.
49- Scan the system for additional indicators of compromise, such as unauthorized user accounts or scheduled tasks, and remove any malicious artifacts found.
50- Apply security patches and updates to Exim4 and the operating system to mitigate known vulnerabilities that could be exploited by attackers.
51- Monitor the system for any recurrence of unusual Exim4 child processes and adjust logging and alerting to capture detailed information for further analysis.
52- Escalate the incident to the security operations team for a comprehensive investigation and to determine if other systems in the network may be affected.
53"""
54references = [
55 "https://www.qualys.com/2021/05/04/21nails/21nails.txt",
56 "https://blog.qualys.com/vulnerabilities-threat-research/2021/05/04/21nails-multiple-vulnerabilities-in-exim-mail-server"
57]
58risk_score = 21
59rule_id = "6eb862bb-013d-4d4f-a14b-341433ca1a1f"
60severity = "low"
61tags = [
62 "Domain: Endpoint",
63 "OS: Linux",
64 "Use Case: Threat Detection",
65 "Tactic: Persistence",
66 "Data Source: Elastic Defend",
67 "Resources: Investigation Guide",
68]
69timestamp_override = "event.ingested"
70type = "new_terms"
71query = '''
72host.os.type:linux and event.type:start and event.action:exec and process.parent.name:exim4 and
73not process.name:(
74 exim4 or start-stop-daemon or run-parts or systemctl or update-exim4.conf or install or plymouth or
75 readlink or grep or stat or cmake or gcc or cppcheck or sort or sshd
76)
77'''
78
79[[rule.threat]]
80framework = "MITRE ATT&CK"
81
82[[rule.threat.technique]]
83id = "T1037"
84name = "Boot or Logon Initialization Scripts"
85reference = "https://attack.mitre.org/techniques/T1037/"
86
87[[rule.threat.technique]]
88id = "T1554"
89name = "Compromise Host Software Binary"
90reference = "https://attack.mitre.org/techniques/T1554/"
91
92[rule.threat.tactic]
93id = "TA0003"
94name = "Persistence"
95reference = "https://attack.mitre.org/tactics/TA0003/"
96
97[rule.new_terms]
98field = "new_terms_fields"
99value = ["process.executable"]
100
101[[rule.new_terms.history_window_start]]
102field = "history_window_start"
103value = "now-5d"
Triage and analysis
Disclaimer: This investigation guide was created using generative AI technology and has been reviewed to improve its accuracy and relevance. While every effort has been made to ensure its quality, we recommend validating the content and adapting it to suit your specific environment and operational needs.
Investigating Unusual Exim4 Child Process
Exim4 is a widely used mail transfer agent on Linux systems, responsible for routing and delivering email. Adversaries may exploit Exim4 by spawning unexpected child processes to execute malicious commands, thereby evading detection and maintaining persistence. The detection rule identifies suspicious child processes initiated by Exim4, excluding known legitimate processes, to flag potential misuse.
Possible investigation steps
- Review the alert details to identify the specific unusual child process name and command line arguments that were executed under the parent process exim4.
- Examine the process tree to understand the hierarchy and context of the spawned process, including any sibling or child processes that may indicate further malicious activity.
- Check the user account associated with the exim4 process to determine if it aligns with expected usage patterns or if it might be compromised.
- Investigate the source and destination of any network connections initiated by the unusual child process to identify potential data exfiltration or command and control activity.
- Analyze system logs around the time of the alert to identify any related events or anomalies that could provide additional context or evidence of compromise.
- Correlate the findings with other alerts or incidents in the environment to determine if this activity is part of a broader attack campaign.
False positive analysis
- Development tools like cmake, gcc, and cppcheck may trigger false positives if they are used in environments where Exim4 is installed. To mitigate this, ensure these tools are included in the exclusion list if they are part of regular development activities.
- System maintenance scripts that utilize commands such as readlink, grep, and stat might be flagged. Review these scripts and add them to the exclusion list if they are verified as part of routine system operations.
- Automated deployment or configuration management tools that invoke systemctl or update-exim4.conf can be mistaken for suspicious activity. Confirm these processes are legitimate and add them to the exclusion list to prevent unnecessary alerts.
- If Exim4 is used in conjunction with SSH services, processes like sshd may appear as child processes. Verify the legitimacy of these connections and exclude them if they are part of expected behavior.
- Regularly review and update the exclusion list to reflect changes in system operations or new legitimate processes that may arise, ensuring the rule remains effective without generating excessive false positives.
Response and remediation
- Immediately isolate the affected system from the network to prevent further malicious activity and lateral movement.
- Terminate any suspicious child processes of Exim4 that are not recognized as legitimate, using process management tools like
killorpkill. - Conduct a thorough review of the Exim4 configuration files and scripts to identify unauthorized modifications or additions, and restore them from a known good backup if necessary.
- Scan the system for additional indicators of compromise, such as unauthorized user accounts or scheduled tasks, and remove any malicious artifacts found.
- Apply security patches and updates to Exim4 and the operating system to mitigate known vulnerabilities that could be exploited by attackers.
- Monitor the system for any recurrence of unusual Exim4 child processes and adjust logging and alerting to capture detailed information for further analysis.
- Escalate the incident to the security operations team for a comprehensive investigation and to determine if other systems in the network may be affected.
References
Related rules
- Initramfs Unpacking via unmkinitramfs
- Linux User Account Credential Modification
- Network Connections Initiated Through XDG Autostart Entry
- Potential Execution via SSH Backdoor
- Systemd Generator Created