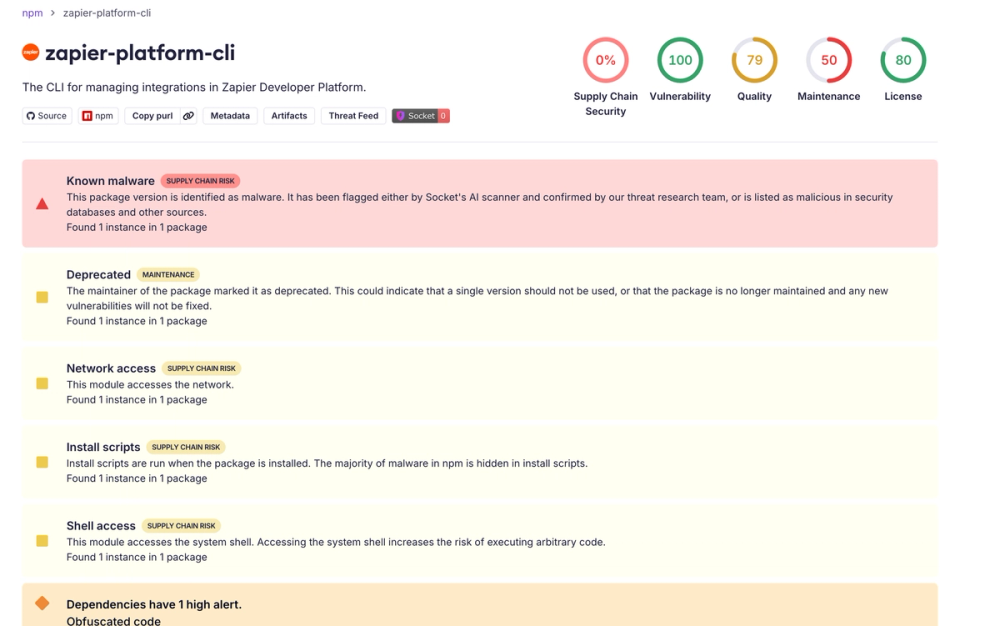
Remote GitHub Actions Runner Registration
This rule detects the configuration of a GitHub Actions self-hosted runner using the Runner.Listener binary. When a machine is registered to a remote repository, its owner gains the ability to execute arbitrary workflow commands on that host. Unexpected or unauthorized runner registration may indicate adversarial activity aimed at establishing remote code execution via malicious GitHub workflows.
Elastic rule (View on GitHub)
1[metadata]
2creation_date = "2025/11/26"
3integration = ["endpoint", "windows", "system", "m365_defender", "sentinel_one_cloud_funnel", "crowdstrike", "auditd_manager"]
4maturity = "production"
5updated_date = "2025/11/26"
6
7[rule]
8author = ["Elastic"]
9description = """
10This rule detects the configuration of a GitHub Actions self-hosted runner using the Runner.Listener binary.
11When a machine is registered to a remote repository, its owner gains the ability to execute arbitrary workflow commands on that host.
12Unexpected or unauthorized runner registration may indicate adversarial activity aimed at establishing remote code execution
13via malicious GitHub workflows.
14"""
15false_positives = [
16 "Authorized github repository with no malicious workflow actions.",
17]
18from = "now-9m"
19index = [
20 "endgame-*",
21 "logs-crowdstrike.fdr*",
22 "logs-endpoint.events.process-*",
23 "logs-m365_defender.event-*",
24 "logs-sentinel_one_cloud_funnel.*",
25 "logs-system.security*",
26 "logs-windows.forwarded*",
27 "logs-windows.sysmon_operational-*",
28 "winlogbeat-*",
29 "auditbeat-*",
30 "logs-auditd_manager.auditd-*"
31]
32language = "eql"
33license = "Elastic License v2"
34name = "Remote GitHub Actions Runner Registration"
35note = """## Triage and analysis
36
37### Investigating Remote GitHub Actions Runner Registration
38
39Unexpected or unauthorized Github actions runner registration may indicate adversarial activity aimed at establishing remote code execution via malicious GitHub workflows.
40
41### Possible investigation steps
42
43- Review the remote repository details and reputation.
44- Examine the remote repository for any suspicious workflows run commands in the `.github/workflows` folder.
45- Examine the execution context like process tree, associated network and file activities.
46- Verify if there is adjascent any sensitive file access or collection.
47- Correlate with other alerts and investiguate if this activity is related to a supply chain attack.
48
49### False positive analysis
50
51- Authorized configuration changes.
52
53### Response and remediation
54
55- Immediately isolate the affected system from the network to prevent further unauthorized command execution and potential lateral movement.
56- Terminate any suspicious child processes that were initiated by the registered Github actions runner.
57- Conduct a thorough review of the affected system's logs and configurations to identify any unauthorized changes or additional indicators of compromise.
58- Restore the system from a known good backup if any unauthorized changes or malicious activities are confirmed.
59- Implement application whitelisting to prevent unauthorized execution.
60- Escalate the incident to the security operations center (SOC) or incident response team for further investigation and to assess the potential impact on the broader network."""
61references = [
62 "https://www.elastic.co/blog/shai-hulud-worm-npm-supply-chain-compromise",
63 "https://socket.dev/blog/shai-hulud-strikes-again-v2",
64]
65risk_score = 47
66rule_id = "57e118c1-19eb-4c20-93a6-8a6c30a5b48b"
67severity = "medium"
68tags = [
69 "Domain: Endpoint",
70 "OS: Linux",
71 "OS: Windows",
72 "OS: macOS",
73 "Use Case: Threat Detection",
74 "Tactic: Execution",
75 "Tactic: Initial Access",
76 "Data Source: Elastic Endgame",
77 "Data Source: Elastic Defend",
78 "Data Source: Windows Security Event Logs",
79 "Data Source: Microsoft Defender for Endpoint",
80 "Data Source: Sysmon",
81 "Data Source: SentinelOne",
82 "Data Source: Crowdstrike",
83 "Data Source: Auditd Manager",
84 "Resources: Investigation Guide",
85]
86timestamp_override = "event.ingested"
87type = "eql"
88
89query = '''
90process where event.type == "start" and event.action in ("exec", "exec_event", "start", "ProcessRollup2", "executed", "process_started") and
91 process.name in ("Runner.Listener", "Runner.Listener.exe") and
92 process.args == "configure" and process.args == "--url" and process.args == "--token"
93'''
94
95
96[[rule.threat]]
97framework = "MITRE ATT&CK"
98[[rule.threat.technique]]
99id = "T1059"
100name = "Command and Scripting Interpreter"
101reference = "https://attack.mitre.org/techniques/T1059/"
102
103
104
105[rule.threat.tactic]
106id = "TA0002"
107name = "Execution"
108reference = "https://attack.mitre.org/tactics/TA0002/"
109[[rule.threat]]
110framework = "MITRE ATT&CK"
111[[rule.threat.technique]]
112id = "T1195"
113name = "Supply Chain Compromise"
114reference = "https://attack.mitre.org/techniques/T1195/"
115[[rule.threat.technique.subtechnique]]
116id = "T1195.002"
117name = "Compromise Software Supply Chain"
118reference = "https://attack.mitre.org/techniques/T1195/002/"
119
120
121
122[rule.threat.tactic]
123id = "TA0001"
124name = "Initial Access"
125reference = "https://attack.mitre.org/tactics/TA0001/"
Triage and analysis
Investigating Remote GitHub Actions Runner Registration
Unexpected or unauthorized Github actions runner registration may indicate adversarial activity aimed at establishing remote code execution via malicious GitHub workflows.
Possible investigation steps
- Review the remote repository details and reputation.
- Examine the remote repository for any suspicious workflows run commands in the
.github/workflowsfolder. - Examine the execution context like process tree, associated network and file activities.
- Verify if there is adjascent any sensitive file access or collection.
- Correlate with other alerts and investiguate if this activity is related to a supply chain attack.
False positive analysis
- Authorized configuration changes.
Response and remediation
- Immediately isolate the affected system from the network to prevent further unauthorized command execution and potential lateral movement.
- Terminate any suspicious child processes that were initiated by the registered Github actions runner.
- Conduct a thorough review of the affected system's logs and configurations to identify any unauthorized changes or additional indicators of compromise.
- Restore the system from a known good backup if any unauthorized changes or malicious activities are confirmed.
- Implement application whitelisting to prevent unauthorized execution.
- Escalate the incident to the security operations center (SOC) or incident response team for further investigation and to assess the potential impact on the broader network.
References
Related rules
- Execution via GitHub Actions Runner
- Credential Access via TruffleHog Execution
- Potential Secret Scanning via Gitleaks
- ScreenConnect Server Spawning Suspicious Processes
- Command Execution via SolarWinds Process