Execution of ZeroLogon PoC executable
Detects the execution of the commonly used ZeroLogon PoC executable.
Sigma rule (View on GitHub)
1title: Execution of ZeroLogon PoC executable
2id: fe0c3029-c6df-4f0b-9b82-e4ca4b9659f0
3status: experimental
4description: Detects the execution of the commonly used ZeroLogon PoC executable.
5author: 'Kostastsale, TheDFIRReport'
6references:
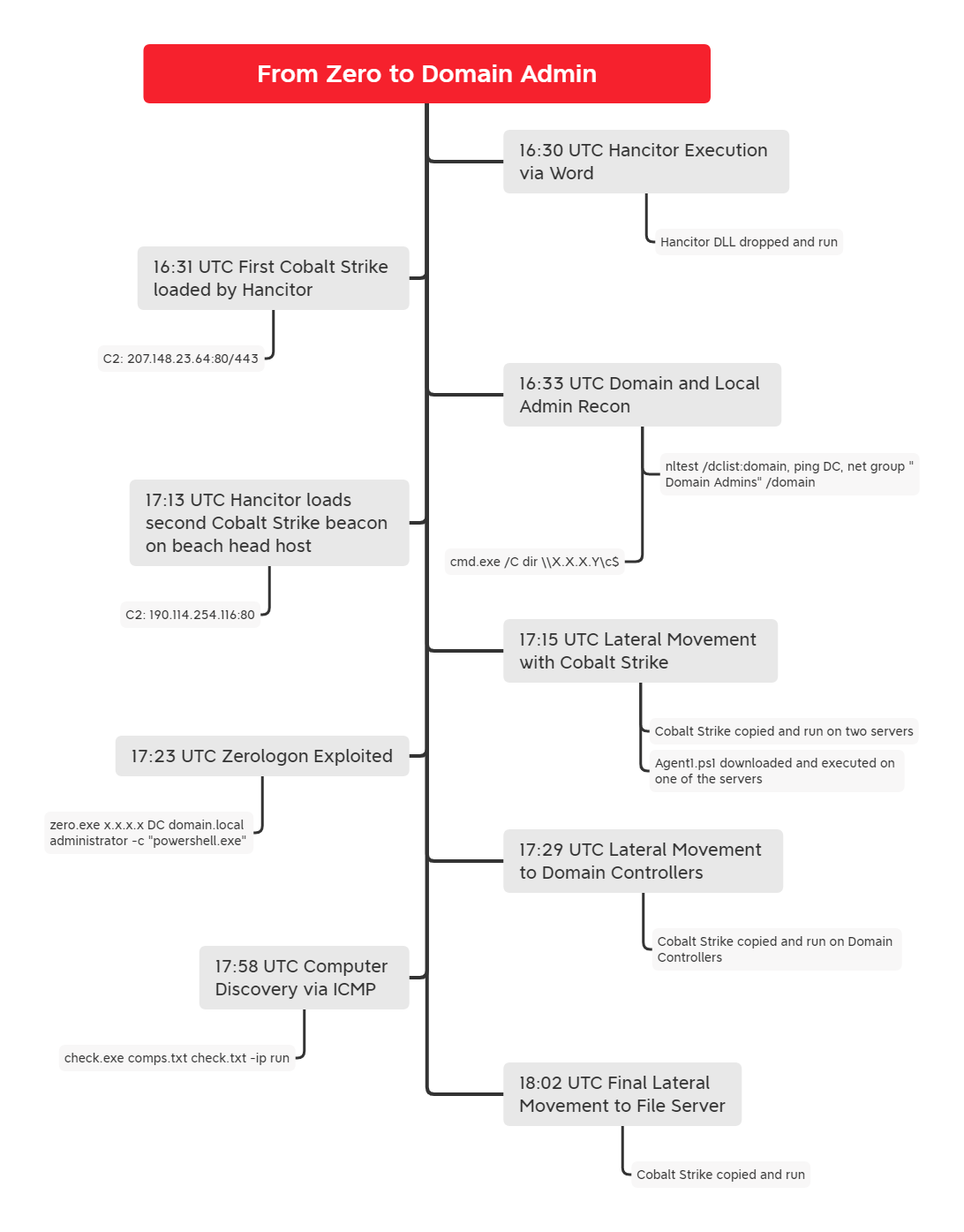
7 - https://thedfirreport.com/2021/11/01/from-zero-to-domain-admin/
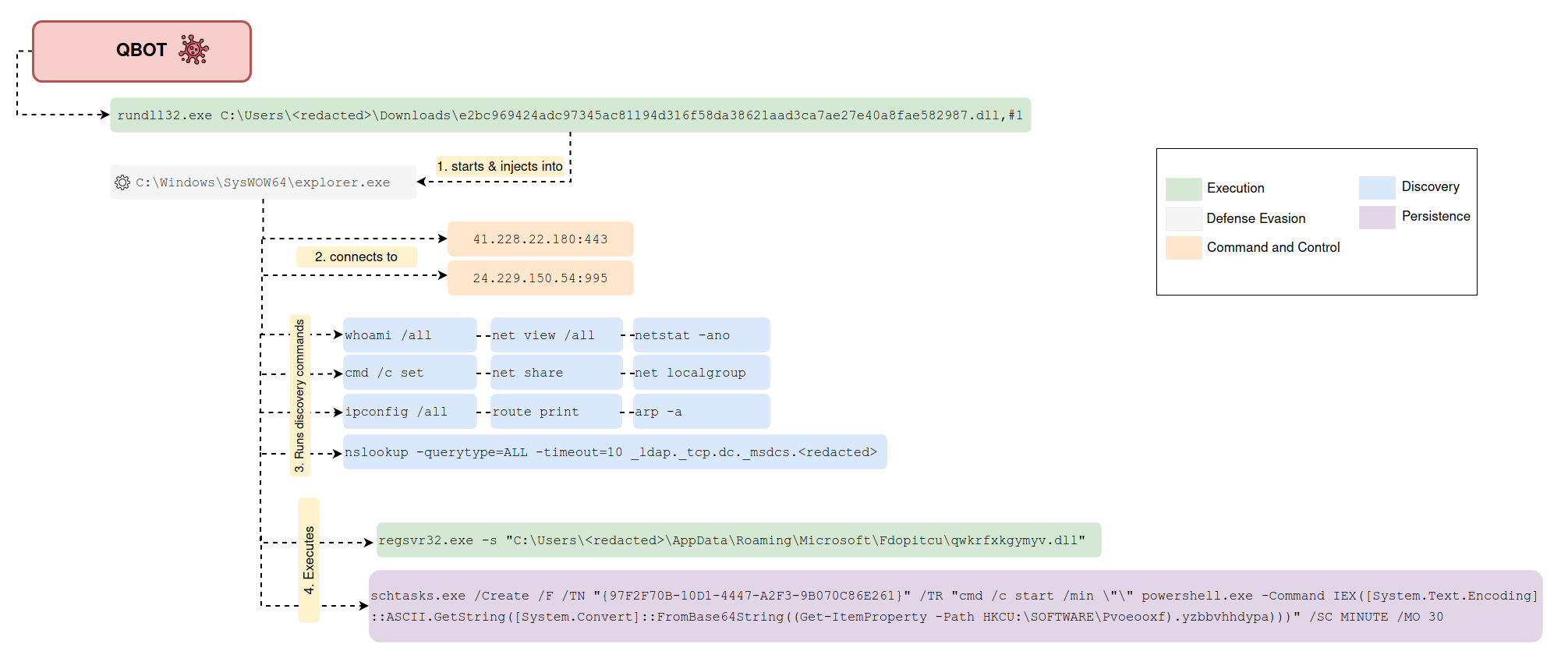
8 - https://thedfirreport.com/2022/02/21/qbot-and-zerologon-lead-to-full-domain-compromise/
9date: 2022-02-12
10modified: 2024-02-23
11logsource:
12 product: windows
13 category: process_creation
14detection:
15 selection1:
16 ParentImage|endswith: '\cmd.exe'
17 Image|endswith:
18 - '\cool.exe'
19 - '\zero.exe'
20 CommandLine|contains|all:
21 - 'Administrator'
22 - '-c'
23 selection2:
24 CommandLine|contains|all:
25 - 'taskkill'
26 - '/f'
27 - '/im'
28 selection3:
29 CommandLine|contains: 'powershell'
30 condition: selection1 and (selection2 or selection3)
31falsepositives:
32 - Unknown
33level: high
34tags:
35 - attack.execution
36 - attack.lateral-movement
37 - attack.t1210
yaml
References
Related rules
- Exploitation Attempt Of CVE-2020-1472 - Execution of ZeroLogon PoC
- HackTool - SharpWSUS/WSUSpendu Execution
- Audit CVE Event
- OMIGOD HTTP No Authentication RCE
- Exploitation Attempt Of CVE-2023-46214 Using Public POC Code