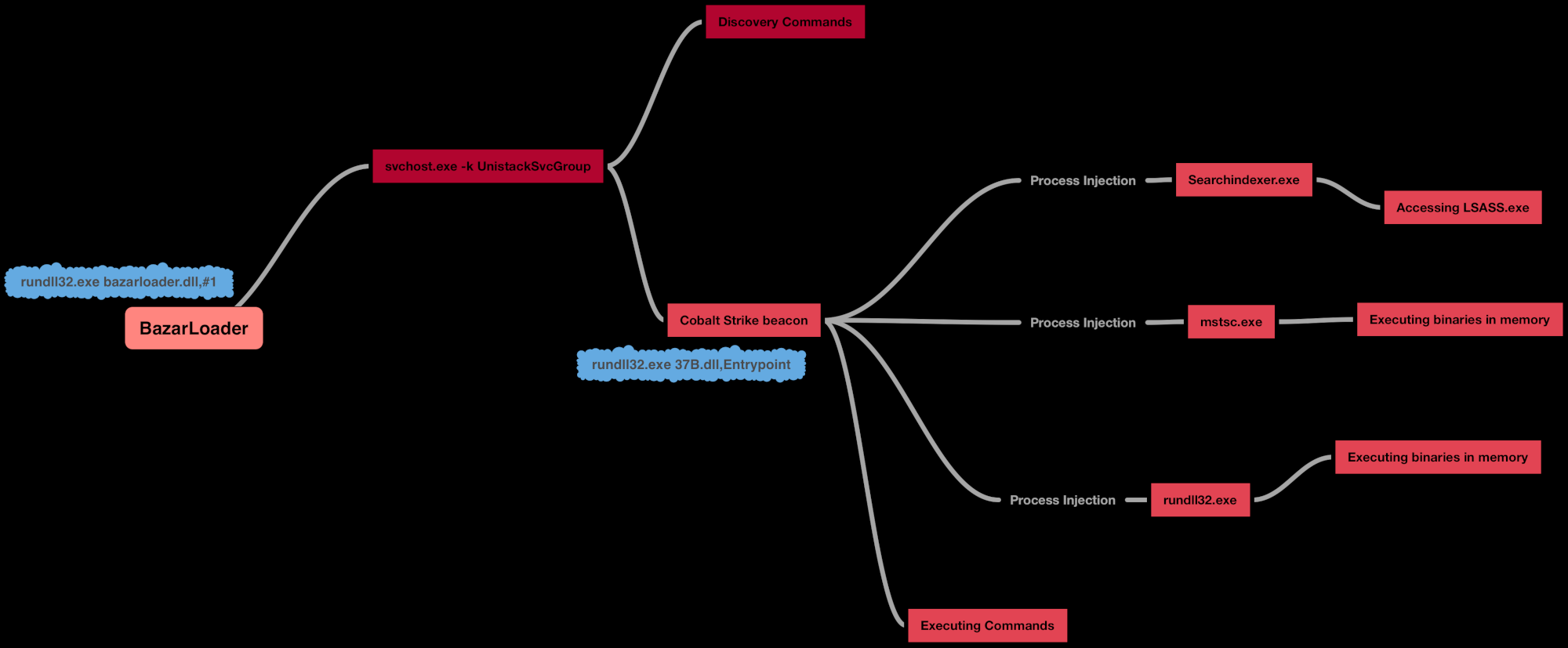
Operator Bloopers Cobalt Strike Commands
Detects use of Cobalt Strike commands accidentally entered in the CMD shell
Sigma rule (View on GitHub)
1title: Operator Bloopers Cobalt Strike Commands
2id: 647c7b9e-d784-4fda-b9a0-45c565a7b729
3related:
4 - id: 4f154fb6-27d1-4813-a759-78b93e0b9c48
5 type: similar
6status: test
7description: Detects use of Cobalt Strike commands accidentally entered in the CMD shell
8references:
9 - https://hstechdocs.helpsystems.com/manuals/cobaltstrike/current/userguide/content/cobalt-4-5-user-guide.pdf
10 - https://thedfirreport.com/2021/10/04/bazarloader-and-the-conti-leaks/
11 - https://thedfirreport.com/2022/06/16/sans-ransomware-summit-2022-can-you-detect-this/
12author: _pete_0, TheDFIRReport
13date: 2022-05-06
14modified: 2023-01-30
15tags:
16 - attack.execution
17 - attack.t1059.003
18 - stp.1u
19logsource:
20 category: process_creation
21 product: windows
22detection:
23 selection_img:
24 - OriginalFileName: 'Cmd.Exe'
25 - Image|endswith: '\cmd.exe'
26 selection_cli:
27 CommandLine|startswith:
28 - 'cmd '
29 - 'cmd.exe'
30 - 'c:\windows\system32\cmd.exe'
31 CommandLine|contains:
32 - 'psinject'
33 - 'spawnas'
34 - 'make_token'
35 - 'remote-exec'
36 - 'rev2self'
37 - 'dcsync'
38 - 'logonpasswords'
39 - 'execute-assembly'
40 - 'getsystem'
41 condition: all of selection_*
42falsepositives:
43 - Unknown
44level: high
yaml
References
Related rules
- Operator Bloopers Cobalt Strike Commands
- Potential APT FIN7 Exploitation Activity
- Remote Access Tool - ScreenConnect Remote Command Execution
- Potential Pikabot Infection - Suspicious Command Combinations Via Cmd.EXE
- Remote Access Tool - ScreenConnect Command Execution