Disable Windows Defender via Service
Detects Windows Defender disabling service installation
Sigma rule (View on GitHub)
1title: Disable Windows Defender via Service
2id: 92f0538f-ad13-4776-9366-b7351d51c4b8
3status: test
4description: Detects Windows Defender disabling service installation
5references:
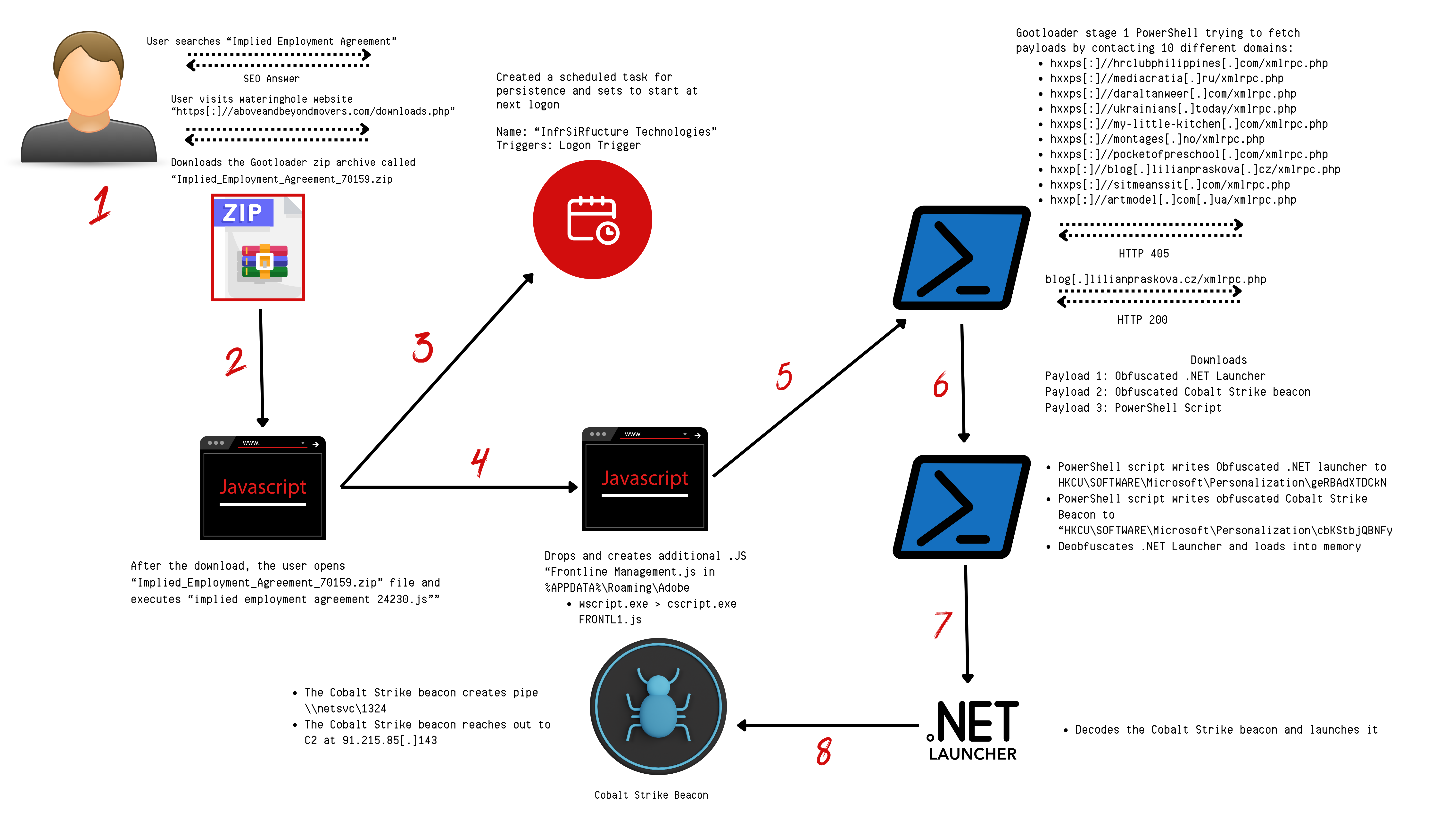
6 - https://thedfirreport.com/2024/02/26/seo-poisoning-to-domain-control-the-gootloader-saga-continues/
7author: _pete_0, TheDFIRReport
8date: 2024-02-17
9tags:
10 - attack.execution
11 - attack.t1569.002
12 - attack.t1562.001
13 - dist.public
14logsource:
15 product: windows
16 service: system
17detection:
18 selection_eid:
19 Provider_Name: 'Service Control Manager'
20 EventID: 7045
21 selection_image:
22 ImagePath|contains|all:
23 - 'Set-MpPreference'
24 - '-DisableRealtimeMonitoring'
25 - 'powershell'
26 condition: all of selection_*
27falsepositives:
28 - Unknown
29level: medium
yaml
References
Related rules
- Metasploit Or Impacket Service Installation Via SMB PsExec
- Suspicious Impacket PSExec Temp Executable File Creation
- Suspicious Impacket Pipe Creation - Psexec
- Autoit3.exe Executable File Creation Matching DarkGate Behavior
- DarkGate Autoit3.exe Execution Parameters