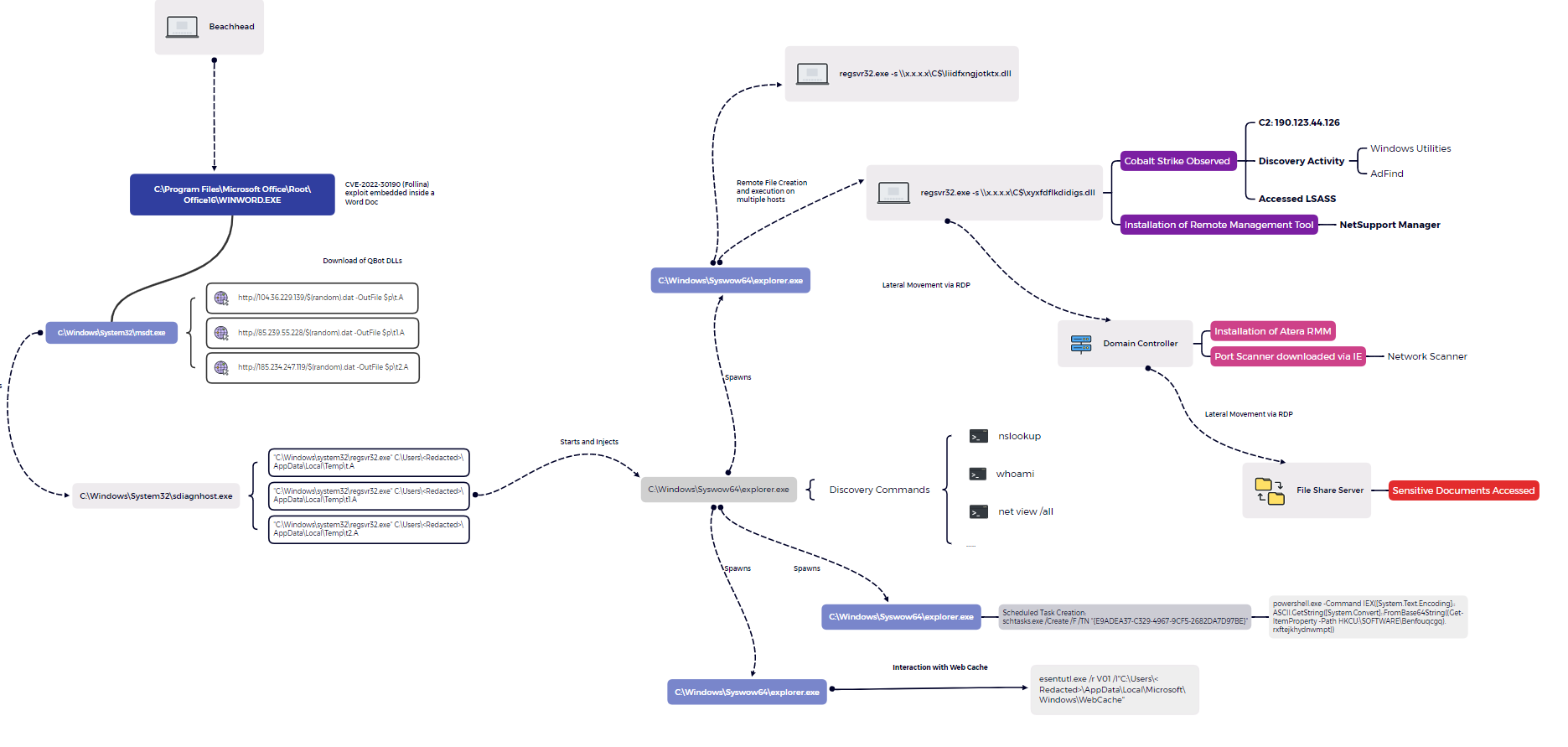
Potential Qbot SMB DLL Lateral Movement
Detection of potential us of SMB to transfer DLL's into the C$ folder of hosts unique to Qbot malware for purposes of lateral movement.
Sigma rule (View on GitHub)
1title: Potential Qbot SMB DLL Lateral Movement
2id: 3eaa2cee-2dfb-46e9-98f6-3782aab30f38
3status: experimental
4description: Detection of potential us of SMB to transfer DLL's into the C$ folder of hosts unique to Qbot malware for purposes of lateral movement.
5author: TheDFIRReport
6date: 2022-09-12
7modified: 2024-02-23
8references:
9 - https://thedfirreport.com/2022/10/31/follina-exploit-leads-to-domain-compromise/
10logsource:
11 product: zeek
12 service: smb_files
13detection:
14 selection_1:
15 zeek_smb_files_path|endswith:
16 - 'C$'
17 selection_2:
18 file_name|endswith:
19 - '\.dll.cfg'
20 condition: selection_1 and selection_2
21falsepositives:
22 - RMM Tools and Administrative activities in C$ Share.
23level: medium
24tags:
25 - attack.lateral_movement
26 - attack.t1570
References
Related rules
- Metasploit Or Impacket Service Installation Via SMB PsExec
- Potential SMB DLL Lateral Movement
- Execution of ZeroLogon PoC executable
- Enabling RDP service via reg.exe command execution
- Possible Impacket DCOMExec Connection Attempt - Zeek