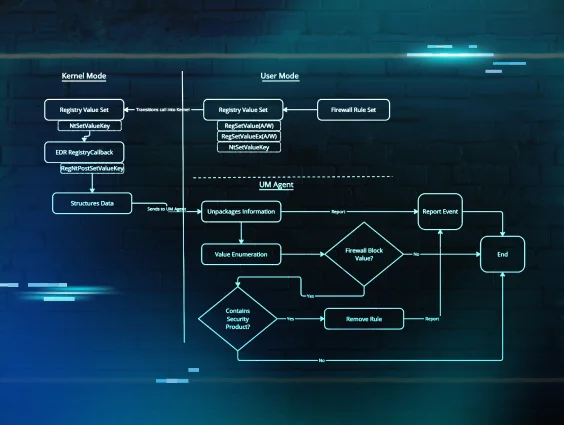
WFP Filter Added via Registry
Detects registry modifications that add Windows Filtering Platform (WFP) filters, which may be used to block security tools and EDR agents from reporting events.
Sigma rule (View on GitHub)
1title: WFP Filter Added via Registry
2id: 1f1d8209-636e-4c6c-a137-781cca8b82f9
3status: experimental
4description: |
5 Detects registry modifications that add Windows Filtering Platform (WFP) filters, which may be used to block security tools and EDR agents from reporting events.
6references:
7 - https://github.com/netero1010/EDRSilencer/blob/0e73a7037ec65c52894d8208e6f605a7da0a34a6/EDRSilencer.c
8 - https://www.huntress.com/blog/silencing-the-edr-silencers
9 - https://www.trendmicro.com/en_us/research/24/j/edrsilencer-disrupting-endpoint-security-solutions.html
10author: Frack113
11date: 2025-10-23
12tags:
13 - attack.defense-evasion
14 - attack.execution
15 - attack.t1562
16 - attack.t1569.002
17logsource:
18 category: registry_set
19 product: windows
20detection:
21 selection:
22 TargetObject|contains: '\BFE\Parameters\Policy\Persistent\Filter\'
23 filter_main_svchost:
24 Image:
25 - 'C:\Windows\System32\svchost.exe'
26 - 'C:\Windows\SysWOW64\svchost.exe'
27 condition: selection and not 1 of filter_main_*
28falsepositives:
29 - Unknown
30level: medium
References
Related rules
- HackTool - SharpUp PrivEsc Tool Execution
- Potential Windows Defender Tampering Via Wmic.EXE
- Windows Defender Exclusions Added - PowerShell
- AWS IAM S3Browser LoginProfile Creation
- AWS IAM S3Browser Templated S3 Bucket Policy Creation