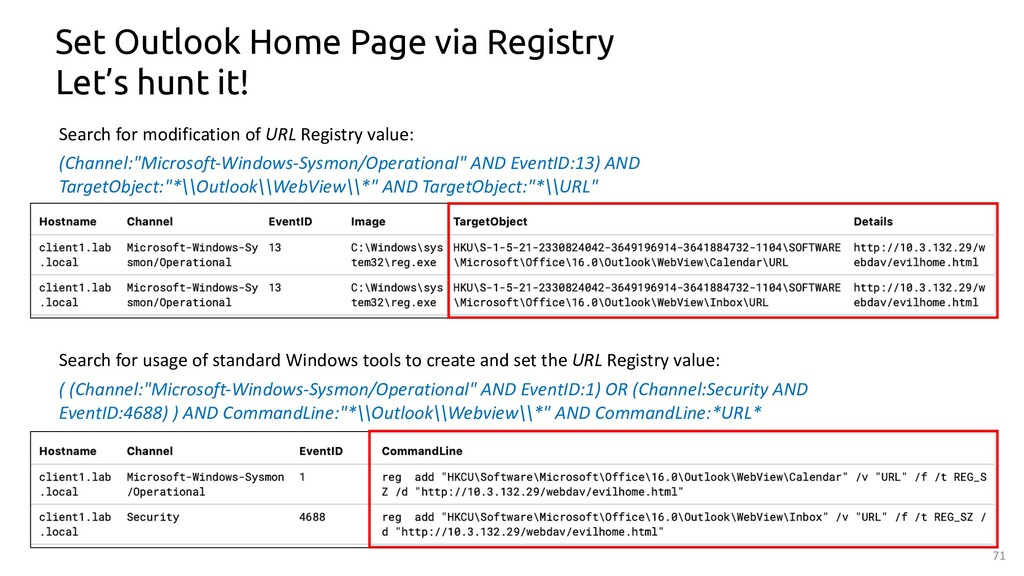
Potential Persistence Via Outlook Home Page
Detects potential persistence activity via outlook home page. An attacker can set a home page to achieve code execution and persistence by editing the WebView registry keys.
Sigma rule (View on GitHub)
1title: Potential Persistence Via Outlook Home Page
2id: ddd171b5-2cc6-4975-9e78-f0eccd08cc76
3related:
4 - id: 487bb375-12ef-41f6-baae-c6a1572b4dd1
5 type: similar
6status: test
7description: |
8 Detects potential persistence activity via outlook home page.
9 An attacker can set a home page to achieve code execution and persistence by editing the WebView registry keys.
10references:
11 - https://speakerdeck.com/heirhabarov/hunting-for-persistence-via-microsoft-exchange-server-or-outlook?slide=70
12 - https://support.microsoft.com/en-us/topic/outlook-home-page-feature-is-missing-in-folder-properties-d207edb7-aa02-46c5-b608-5d9dbed9bd04?ui=en-us&rs=en-us&ad=us
13 - https://trustedsec.com/blog/specula-turning-outlook-into-a-c2-with-one-registry-change
14author: Tobias Michalski (Nextron Systems), David Bertho (@dbertho) & Eirik Sveen (@0xSV1), Storebrand
15date: 2021-06-09
16modified: 2024-08-07
17tags:
18 - attack.defense-evasion
19 - attack.persistence
20 - attack.t1112
21logsource:
22 product: windows
23 category: registry_set
24detection:
25 selection:
26 TargetObject|contains|all:
27 - '\Software\Microsoft\Office\'
28 - '\Outlook\WebView\'
29 TargetObject|endswith: '\URL'
30 condition: selection
31falsepositives:
32 - Unknown
33level: high
References
Related rules
- Activate Suppression of Windows Security Center Notifications
- Add DisallowRun Execution to Registry
- Blackbyte Ransomware Registry
- Blue Mockingbird
- Change User Account Associated with the FAX Service